SOC 2 Compliance Requirements: What’s Required and Why It Matters
SOC 2 compliance is built on a rigorous framework of principles and controls, but many service providers underestimate what’s actually required to pass an audit.
Whether you’re preparing for a Type I or Type II report, success depends on more than good intentions. It requires well-documented policies, assigned control ownership, tested procedures, and detailed evidence.
This guide breaks down the core elements of SOC 2 compliance, what auditors expect and how to get there with confidence.
The Foundation: Trust Services Criteria
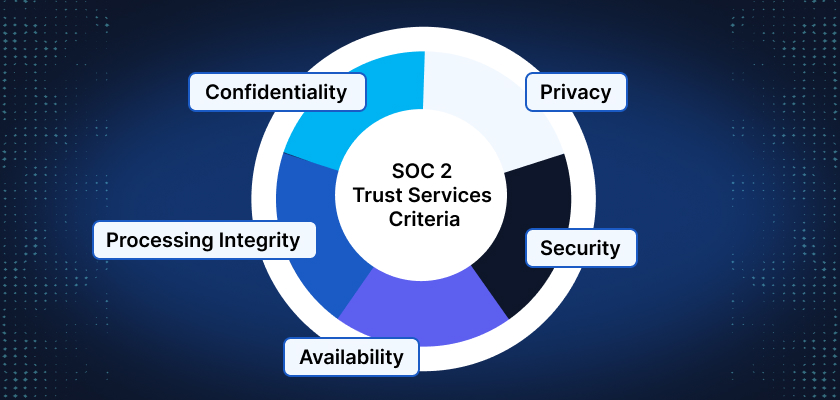
SOC 2 reports are built around the AICPA’s Trust Services Criteria (TSC). Each criterion represents a pillar of operational trust.
You must include Security in your SOC 2 scope. The remaining four are optional but often adopted based on client needs or industry expectations.
- Security (Required)
Protect systems against unauthorized access, disclosure, or misuse.
Examples: Firewalls, access controls, MFA, vulnerability scans - Availability
Ensure systems are available for operation as committed.
Examples: Uptime SLAs, redundancy, disaster recovery - Processing Integrity
Ensure system processing is complete, accurate, timely, and authorized.
Examples: Input validation, transactional accuracy, error detection - Confidentiality
Protect sensitive information from unauthorized disclosure.
Examples: Data encryption, access restrictions, data loss prevention - Privacy
Address how personal data is collected, used, retained, and disposed of according to your privacy notice.
Examples: Consent tracking, data subject rights, retention schedules
What You Need to Document and Prove
SOC 2 isn’t just about having strong controls, it’s about proving they exist and operate effectively.
Auditors expect structured, version-controlled, and reviewable documentation across:
- Formal Policies and Procedures
Access control, asset management, change management, incident response, encryption standards, data classification, and more. - Control Ownership Assignments
Every control must have a designated owner accountable for execution and maintenance. - System Description (included in the final report)
Details of your infrastructure, software stack, people, data flows, vendor relationships, and geographic regions. - Evidence of Operation
Collected over the audit period (Type II), this includes:- Access logs
- System configuration exports
- Screenshots
- Acknowledged policies
- Change tickets
- Incident records
- Access logs
The MSP Guide to SOC 2: Preparing for a SOC 2 Journey
DownloadCommon SOC 2 Controls and What They Cover
Here are some control categories commonly reviewed during a SOC 2 audit, with example requirements:
- Access Control
Role-based access, MFA enforcement, password complexity policies, user provisioning and deprovisioning - Change Management
Documented approval and rollback process for infrastructure, software, and system changes - Security Awareness Training
Mandatory, recurring training for all staff with attendance records or acknowledgment - Monitoring and Logging
Centralized log collection, real-time alerts for suspicious activity, log retention policies - Incident Response
A formal IR plan, tested regularly, with documentation of incidents and post-incident reviews
How Requirements Vary Between Type I and Type II
While the overall scope of work is similar, the level of proof differs depending on which report you pursue.
- SOC 2 Type I
You must show that your controls are designed appropriately as of a single point in time.
Best for initial audits or when launching a compliance program. - SOC 2 Type II
You must show that your controls are operating effectively throughout a specified period (commonly 3–12 months).
Provides stronger assurance and is often preferred by enterprise clients.
FAQs About SOC 2 Requirements
The Security criterion is mandatory. The others, Availability, Processing Integrity, Confidentiality, and Privacy, are optional but frequently adopted depending on your business and client demands.
No. You can scope your audit to Security only, or include additional criteria based on what your customers expect and what your systems support.
Auditors assess your system description, control design, supporting documentation, evidence of operation (for Type II), and alignment with the Trust Services Criteria.
Yes, many MSPs and smaller providers succeed by leveraging compliance platforms, assigning cross-functional ownership, and adopting automation to manage documentation and evidence.