Cybersecurity threats are evolving faster than ever, and organizations, especially those supporting multiple clients, can’t afford blind spots. A well-structured cybersecurity risk assessment checklist helps prioritize defenses, align teams, and meet regulatory demands with confidence. In this article, we explore the core elements of these cybersecurity risk assessment checklists, the strategic value they deliver, and how to apply them effectively across environments.
What is a Cybersecurity Risk Assessment Checklist and Why it’s Important
A cybersecurity risk assessment checklist is a structured tool used to identify, evaluate, and prioritize cyber risks across an organization’s infrastructure, processes, and users. Unlike ad hoc reviews or reactive assessments, this checklist provides a standardized way to surface vulnerabilities, validate controls, and align mitigation efforts with business and regulatory requirements.
Rather than being a one-size-fits-all template, a security risk assessment checklist is often tailored to the specific needs of an organization, whether you’re a growing MSP, an enterprise managing sensitive data, or a compliance-focused consultancy. For larger environments, this may take the form of an enterprise risk assessment checklist, encompassing interconnected systems, departments, and external partners. In every case, the goal is the same: ensuring that no critical area, like access control, data encryption, third-party exposure, or backup integrity, is overlooked.
Why Use a Cybersecurity Risk Assessment Checklist?
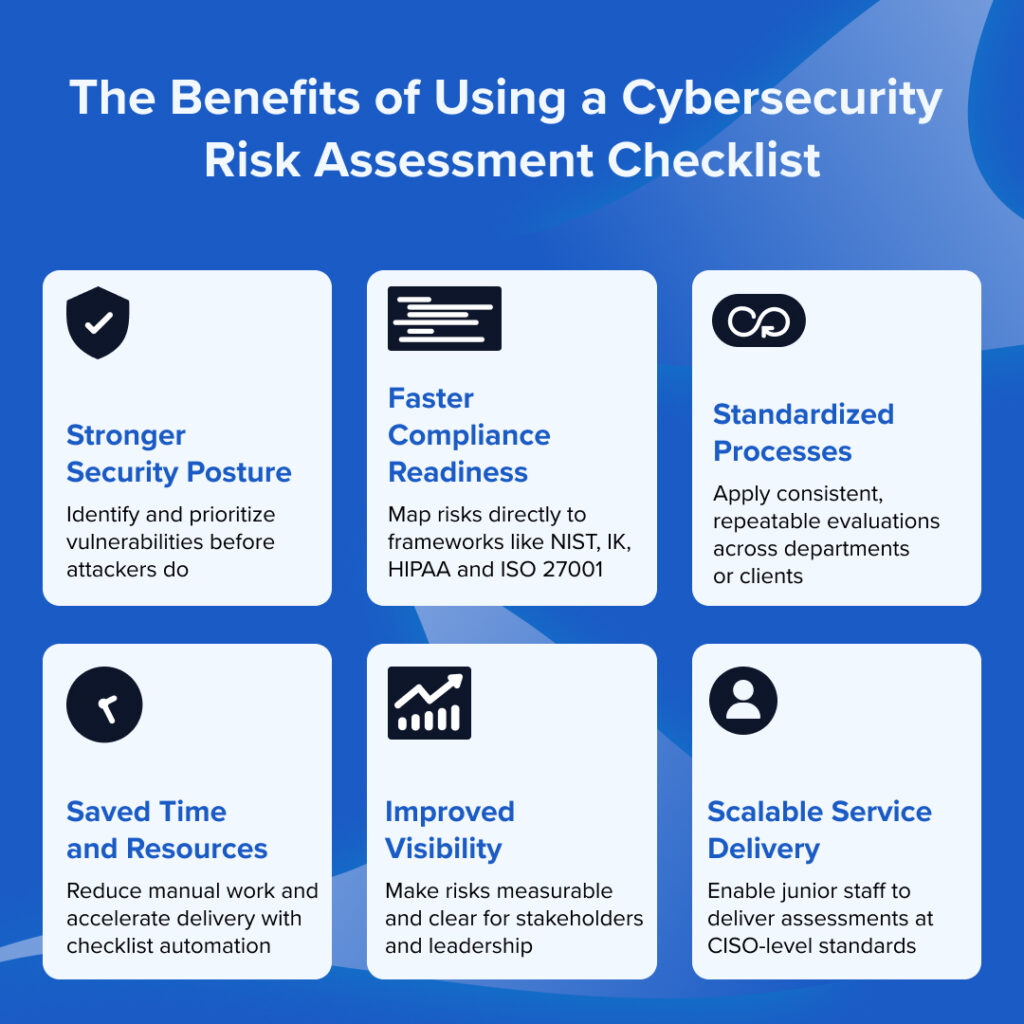
Organizations today face mounting cybersecurity pressure from regulators, cyber insurers, and clients alike. A standardized checklist helps navigate that complexity and build resilience. Here’s why it matters:
- Regulatory compliance: Frameworks like HIPAA, CMMC, ISO 27001, and PCI DSS all require structured risk evaluations. A checklist helps document and demonstrate due diligence.
- Consistent security posture evaluation: Whether you’re assessing internal systems, client environments, or third-party vendors, a checklist ensures you evaluate each one against the same set of baseline controls.
- Centralized documentation: Checklists streamline reporting, reduce duplication, and simplify audit prep by keeping all findings, remediation plans, and justifications in one place.
- Scalable service delivery: For MSPs and MSSPs, building risk assessment checklists allows junior staff to run assessments at a higher standard, unlocking greater service efficiency and consistency across clients.
- Clear prioritization: By integrating likelihood and impact scoring, checklists help prioritize what matters most, reducing noise and accelerating response.
Core Components of a Cybersecurity Risk Assessment Checklist
A well-built cybersecurity risk assessment checklist provides full visibility into technical, procedural, and organizational risks across your environment, or your clients’ environment, in the case of service providers. It acts as a map for identifying exposures, assigning risk levels, and prioritizing mitigation. While each checklist may be adapted to industry and size, the most effective ones share several core categories.
Below are the essential components of a comprehensive security risk assessment checklist, with examples of what’s typically evaluated in each.
1. Network and Infrastructure Risk Scans
Evaluate the health, configuration, and exposure of on-premises and cloud-based network infrastructure.
Key items to assess in this subset of our wider checklist – a network security risk assessment checklist :
- Open ports and unused services
- Outdated or unpatched systems
- Firewall rule misconfigurations
- Rogue or unknown devices
- Cloud workload exposures (e.g., misconfigured S3 buckets)
For example, if an SMB network has a legacy VPN server with a known vulnerability (CVE) still in use, the checklist will flag this under “Patch Management” with a high-priority risk score.
2. Identity and Access Management (IAM)
Assess how users are authenticated and authorized across all systems.
Key items to assess:
- Use of Multi-Factor Authentication (MFA)
- Privileged Access Management (PAM) policies
- Orphaned accounts or unused credentials
- Role-based access control enforcement
- Credential rotation policies
For example, the checklist may reveal that five terminated employees still have active VPN credentials, and flag this under IAM as a high-impact finding.
3. Data Protection and Encryption
Check how sensitive data is handled, stored, and protected across systems and workflows.
Key items to assess:
- Use of encryption for data in transit and at rest, with up-to-date protocols such as TLS 1.2 or higher
- Endpoint and mobile device encryption
- Data classification and handling policies
- Use of secure protocols (SFTP, HTTPS, etc.)
For example, if the checklist surfaces that a healthcare provider stores patient records on laptops without full disk encryption, this will be marked as a compliance-critical risk under HIPAA.
4. Threat Modeling and Risk Scoring
Use structured techniques to understand how threats could materialize and impact business operations.
Key items to assess:
- Threat scenarios mapped to assets and entry points
- Risk scoring using likelihood × impact models
- Mapping to MITRE ATT&CK or STRIDE models
- Known vulnerabilities correlated with exploitability
For example, the checklist can include a threat model showing how lateral movement from an unsegmented IoT device could compromise patient data.
5. Asset Classification and Business Impact
Inventory all hardware, software, and cloud resources, and classify them by criticality.
Key items to assess:
- Asset inventory completeness (systems, apps, cloud services)
- Business impact rating (high/medium/low)
- Critical process dependencies
- Owner/steward assignment
For example, if the checklist uncovers a forgotten application running on an outdated server, it may be linked to a critical revenue-generating workflow, raising its priority despite low visibility.
6. Backup, Recovery, and Resilience
Evaluate the organization’s ability to recover from cyber incidents and data loss.
Key items to assess:
- Frequency and scope of backups
- Test results from recent recovery drills
- RPO (Recovery Point Objective) and RTO (Recovery Time Objective) thresholds
- Segmentation of backup systems from primary networks
For example, if the checklist surfaces that the organization performs daily backups but has never tested recovery, this will be highlighted as a medium-likelihood, high-impact risk.
7. Physical and Environmental Security
While often overlooked in digital-first checklists, physical security risks remain relevant.
Key items to assess:
- Server room access controls and logging
- Security camera coverage and retention
- Device storage policies for remote staff
- Paper record handling (where applicable)
For example, the checklist may flag an open-access server closet in a satellite office, which will then be highlighted as a physical breach risk for compliance review.
8. Third-Party and Supply Chain Risks
Evaluate vendors, partners, and outsourced IT systems that may introduce vulnerabilities.
Key items to assess:
- Existence of vendor risk assessments
- Access rights granted to third parties
- Incident notification SLAs in vendor contracts
- Use of outdated or unsupported third-party software
If, for example, a checklist shows no documented due diligence for a payroll provider with admin access to sensitive HR systems, this should trigger a third-party risk alert.
9. Security Policies and Awareness
Ensure policies exist, are current, and are understood by relevant teams.
Key items to assess:
- Acceptable Use Policy (AUP)
- Remote work and BYOD policies
- Security awareness training frequency
- Incident response plan distribution
For example, the checklist may identify that the last company-wide phishing simulation was over 18 months ago, and flag this as a gap in user awareness training.
Each of these categories contributes to a complete, defensible picture of cybersecurity risk, especially when combined into a repeatable, automated framework. By structuring assessments around these areas, organizations and service providers can improve visibility, make data-driven decisions, and demonstrate readiness to clients, partners, and regulators.
Cybersecurity Risk Assessment Checklist Example
The following example shows how risk items are documented, scored, and actioned, illustrating how organizations can structure evaluations, document findings, and prioritize remediation actions based on risk level.
| Network Security | Are all unnecessary open ports closed on external firewalls? | Ports 21, 23, and 3389 found open | High | Reconfigure firewall rules |
| Patch Management | Are critical systems regularly patched and up to date? | Several servers missing updates | Medium | Schedule patch cycle |
| Access Controls | Is MFA enforced for admin accounts? | Enforced on 70% of systems | High | Expand MFA to all admin accounts |
| Data Protection | Has encryption been implemented for sensitive data during storage and transmission? | Transit encrypted; rest not | High | Implement disk-level encryption |
| Backup & Recovery | Are backups tested at least quarterly? | No testing in 12 months | High | Perform recovery drill |
| Asset Management | Is there a complete and current asset inventory? | Missing cloud app records | Medium | Update inventory |
| Threat Modeling | Has a formal threat model been developed and reviewed? | Not documented | Medium | Initiate threat modeling process |
| Vendor Risk | Have third-party vendors been assessed in the past 12 months? | No current risk assessments | High | Conduct vendor assessments |
| Policy Management | Are all key security policies current and distributed? | Some outdated documents | Medium | Review and update policies |
| User Awareness | Are users receiving regular cybersecurity training? | Last training 18 months ago | Medium | Schedule new training session |
How Cynomi Simplifies Cybersecurity Risk Assessments
For MSPs, MSSPs, and consultancies, conducting risk assessments at scale is one of the most time-consuming and resource-intensive parts of delivering cybersecurity services. Cynomi’s vCISO platform simplifies and accelerates this process through automation, built-in intelligence, and structured workflows, allowing service providers to deliver consistent, high-quality results across clients without adding headcount.
Here’s how Cynomi transforms the risk assessment process:
Built-In, Standards-Based Checklists
Cynomi provides pre-built assessment checklists mapped to leading frameworks such as NIST, CIS, and ISO 27001. These templates ensure full coverage across required domains and make it easy to deliver standardized services aligned with regulatory and best-practice expectations.
Continuous Scoring and Visual Dashboards
The platform continuously scores cybersecurity posture across client environments, and offers visual dashboards that highlight risk levels by domain, control category, and compliance framework. This makes it easier for both technical and non-technical stakeholders to understand what’s working and what’s not.
Remediation Plans Powered by CISO Knowledge
Powered by AI and infused with seasoned CISO knowledge, Cynomi automatically generates client-specific remediation plans. These plans are tailored to each organization’s unique environment and maturity level, helping teams prioritize actions and demonstrate immediate value.
Audit-Ready Documentation and Reporting
Cynomi centralizes all assessment findings, recommendations, and supporting evidence, making it easy to produce audit-ready documentation for internal stakeholders, external auditors, or client-facing reports. This eliminates the manual burden of consolidating spreadsheets and policy drafts.
Efficiency and Scale
By automating a significant portion of the manual work, Cynomi allows junior team members to execute assessments that meet executive-level standards. This dramatically increases service capacity, improves margins, and enables providers to grow their cybersecurity offerings with fewer bottlenecks.
Best Practices for Effectively Using Cybersecurity Risk Assessment Checklists
Establishing a cybersecurity risk assessment checklist is a great first step, but how you use it makes all the difference. Whether you’re protecting your own organization or delivering security services to clients, applying the checklist effectively ensures accurate results, stronger remediation, and audit-ready outcomes.
Below are several proven best practices to get the most value out of your security risk assessment checklist. By following these best practices, organizations can evolve their use of the cybersecurity risk assessment checklist from a compliance formality into a dynamic tool that drives operational efficiency, client trust, and long-term security resilience.
Customize to Your Environment and Compliance Needs
Start with a standardized checklist, but tailor it to fit your organization’s industry, size, and regulatory context. A healthcare provider, for example, will need to map checklist items to HIPAA, while a defense contractor may need to align with CMMC or NIST SP 800-171. There are templates that are mapped to specific frameworks (e.g., NIST, CIS, ISO 27001) that you can use to reduce setup time while ensuring coverage.
Conduct Reviews on an Ongoing Basis
Risk assessments should not be a one-time exercise. They need to be regularly performed to ensure ongoing visibility into changing risk conditions and maintain readiness for compliance audits. Perform reviews:
- During onboarding (new clients, new systems)
- On a scheduled basis (quarterly or annually)
- After significant events (breaches, audits, major infrastructure changes)
Involve Key Stakeholders Early
Effective assessments require input from across the organization, including IT, GRC teams, compliance officers, and business leaders. Their participation ensures findings are accurate and that remediation is prioritized based on both security risk and business impact.
Document Everything, Including Justifications
Documentation is critical as it supports internal tracking, but also prepares you for audits and client transparency. For each checklist item, document:
- The finding
- The rationale behind the risk score
- Any compensating controls
- Remediation timelines and responsible owners
Link Findings to Remediation Plans
Don’t treat the checklist as a standalone report. Translate findings into concrete actions by assigning remediation tasks to the right owners, including target deadlines, and tracking progress over time. This part can be significantly simplified by using platforms like Cynomi, where these tasks can be auto-generated and tracked through dashboards.
Use Checklist Results to Support Strategic Goals
Well-documented risks become talking points that align cybersecurity with business priorities. Beyond technical remediation, assessment findings can inform and influence:
- Budget planning
- Cyber insurance renewals
- Client onboarding conversations
- Executive briefings and QBRs
Improve Risk Visibility with Cybersecurity Checklists
In today’s evolving threat landscape, risk assessments can no longer be reactive or inconsistent. A cybersecurity risk assessment checklist turns fragmented reviews into structured, repeatable evaluations that provide clarity, control, and confidence, whether you’re managing a single environment or dozens of client networks.
The benefits are clear: cybersecurity risk assessment checklists streamline documentation, accelerate compliance readiness, and help organizations build a stronger, more resilient security posture. They also support scalable, standardized delivery across teams or clients, and improve both internal collaboration and client-facing communication.
Adding a platform like Cynomi into the mix can take those benefits even further, automating large portions of the manual work and delivering high-quality assessments backed by AI and CISO expertise.
FAQs
A structured framework used to evaluate and prioritize cyber risks across systems, users, and processes, helping organizations identify vulnerabilities, meet compliance requirements, and guide remediation.
A standardized checklist ensures consistent, repeatable assessments across environments, reduces manual work, and supports clear documentation for audits, reporting, and internal alignment.
A comprehensive checklist covers areas like network vulnerabilities, access controls, data protection, threat modeling, asset classification, backup and recovery, vendor risks, and policy reviews, each tied to risk scoring and business impact.
Tailor the checklist to your regulatory context, conduct assessments regularly, involve key stakeholders, document findings with justifications, and link results to actionable remediation plans.
Cynomi offers an automated vCISO platform with built-in risk assessment checklists, continuous scoring, and AI-driven remediation plans, reducing manual effort and enabling scalable service delivery.
MSPs, MSSPs, internal IT and security teams, and security consultants use these checklists to assess their own environments or deliver structured cybersecurity services to clients.