What is SOC 2?
SOC 2 is one of the most widely recognized compliance frameworks for technology and service organizations. Designed to help businesses protect sensitive customer information, SOC 2 builds trust with clients and demonstrates a commitment to secure operations.
With increased focus on data privacy and third-party risk, SOC 2 is now a baseline expectation for service providers handling customer data. Whether you’re responding to client demands or preparing for long-term growth, understanding SOC 2 is a critical first step.
Introduction to SOC 2
SOC 2 stands for System and Organization Controls 2. It was developed by the American Institute of Certified Public Accountants (AICPA) to evaluate how service organizations manage data security, availability, and privacy.
Unlike a certification, SOC 2 is an attestation report provided by an independent third-party auditor. It assesses whether an organization’s security practices meet a specific set of criteria, known as the Trust Services Criteria.
SOC 2 applies to any company that stores, processes, or transmits customer data, particularly SaaS providers, cloud services, and IT vendors.
Why SOC 2 Compliance Matters
Service providers today are expected to prove they can protect customer data. SOC 2 compliance helps establish that trust.
Key reasons SOC 2 matters:
- Client Confidence – Demonstrates to customers that you follow industry-standard data protection practices
- Market Access – Many organizations require SOC 2 before signing vendor agreements
- Operational Rigor – Forces internal structure, documentation, and accountability
- Audit Trail – Prepares your organization for regulatory scrutiny and future growth
In a landscape shaped by increasing risk and rising expectations, SOC 2 isn’t just a checkbox, it’s a business enabler.
SOC 2 vs. Other Compliance Frameworks
How does SOC 2 compare to other common standards?
| Framework | Focus | Report Type | Key Difference |
| SOC 2 | Security, availability, privacy, etc. | Private attestation | Tailored to each organization |
| ISO 27001 | Information security management systems | Certification | Formal certification with global recognition |
| SOC 1 | Financial reporting controls | Private attestation | Focused on financial process impact |
| SOC 3 | Public version of SOC 2 | Public report | High-level summary with no detailed findings |
SOC 2 is often the preferred option for U.S.-based service providers focused on operational and client-facing controls.
The MSP Guide to SOC 2: Preparing for a SOC 2 Journey
DownloadUnderstanding the Five Trust Services Criteria
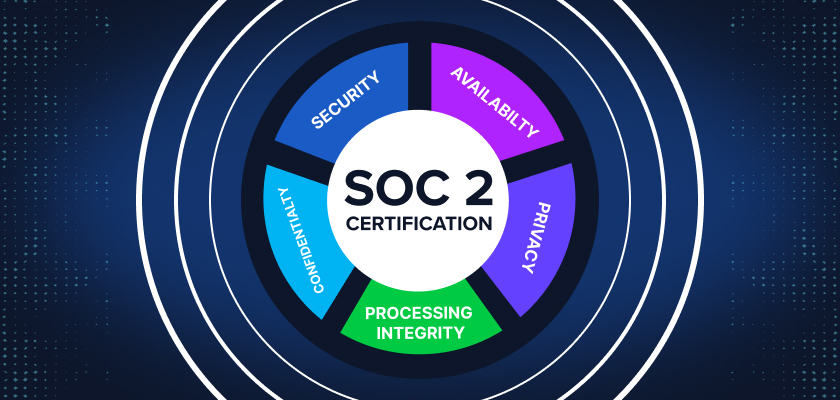
SOC 2 evaluates systems and processes against five Trust Services Criteria. Each one addresses a different aspect of secure and reliable service delivery.
- Security(Required) – Protection of data from unauthorized access.
- Example: Firewalls, MFA, and endpoint monitoring.
- Availability – System uptime and operational resilience.
- Example: SLAs, disaster recovery plans.
- Processing Integrity – Ensuring systems operate accurately and reliably.
- Example: Error-checking, transactional accuracy.
- Confidentiality – Limiting data access to authorized parties.
- Example: Data classification and encryption at rest.
- Privacy – Managing personal information according to regulatory expectations.
- Example: Consent tracking, data subject rights.
Organizations select the criteria most relevant to their services and client requirements.
SOC 2 Type I vs. Type II
There are two types of SOC 2 reports, depending on the level of assurance your clients need:
SOC 2 Type I
- Evaluates whether required controls are properly designed at a specific point in time.
- Use Case: Early-stage companies establishing controls for the first time.
SOC 2 Type II
- Assesses the operational effectiveness of those controls over a defined period (typically 3–12 months).
- Use Case: Mature organizations demonstrating ongoing compliance.
Clients often start with Type I and progress to Type II as part of their long-term compliance strategy.
FAQs About SOC 2
SOC 2 is a report that shows your organization has the right systems in place to protect customer data.
Type I looks at whether controls are in place today; Type II checks if they’re working consistently over time.
No, it’s voluntary, but it’s often required by clients and partners before doing business.
It depends on your current security maturity. Type I typically takes 1–3 months. Type II takes 3–12 months depending on the review period.
Independent CPA firms that are qualified to issue AICPA attestation reports.