Simplified Cybersecurity and Compliance Management
Scrap Manual Work.
Boost Efficiency. Drive Sales.
Scale your services with the first
AI-Powered vCISO Platform
Cynomi combines AI automation with built-in CISO expertise to power high-quality, high-margin security and compliance services.
No Setup, No Hassle,
Just Results
The platform automates security and compliance management with no manual hassle, working seamlessly from day one.
Security, Risk, and Compliance in One Flow
Cybersecurity and compliance are combined into a unified workflow, so that every security action automatically doubles as a compliance measure – maximizing efficiency and eliminating duplicate work.
Ready to Use, Fully Tailored
Cynomi comes pre-configured for immediate use, yet automatically builds a unique cyber profile for each client. This saves setup time while ensuring every action is relevant and customized.
Built-In CISO Expertise
CISO-level knowledge and insights are embedded directly into automated workflows, empowering even junior staff to deliver expert-level security services.
Fully Connected Workflows
Every component in Cynomi’s platform – assessments, risk scores, tasks, remediation plans, policies and controls – is connected in one seamless flow to ensure consistency, save time, and prove progress.
AI-Powered Intelligence: Automate, Customize, and Scale
Cynomi uses AI to assess risks, generate insights, and deliver recommendations rapidly, enhancing service efficiency and scalability.
No Setup, No Hassle,
Just Results
The platform automates security and compliance management with no manual hassle, working seamlessly from day one.
Security, Risk, and Compliance in One Flow
Cybersecurity and compliance are combined into a unified workflow, so that every security action automatically doubles as a compliance measure – maximizing efficiency and eliminating duplicate work.
Ready to Use, Fully Tailored
Cynomi comes pre-configured for immediate use, yet automatically builds a unique cyber profile for each client. This saves setup time while ensuring every action is relevant and customized.
Built-In CISO Expertise
CISO-level knowledge and insights are embedded directly into automated workflows, empowering even junior staff to deliver expert-level security services.
Fully Connected Workflows
Every component in Cynomi’s platform – assessments, risk scores, tasks, remediation plans, policies and controls – is connected in one seamless flow to ensure consistency, save time, and prove progress.
AI-Powered Intelligence: Automate, Customize, and Scale
Cynomi uses AI to assess risks, generate insights, and deliver recommendations rapidly, enhancing service efficiency and scalability.
Deliver Expert-Level Cybersecurity. Effortlessly.
See exactly where clients stand. Set strategic goals.
Get them there with built-in CISO knowledge and workflows.
vCISO Services
Build and scale vCISO programs with automated, CISO-guided workflows. Tailor frameworks, policies, and plans per client, reduce manual work, and align risk, compliance, and security programs in one platform.
Read MoreCyber Resilience Management
Strengthen client resilience with standardized cybersecurity programs and actionable insights. Help clients understand, monitor, and strengthen their security posture while reducing complexity and boosting protection.
Read MoreCompliance Automation
Automate compliance mapping, tracking, and evidence collection across multiple frameworks. Reduce manual effort while ensuring clients remain prepared, audit ready, and confident.
Read MoreSecurity Posture Assessment
Streamline assessments with automated scans and guided questionnaires. Identify risks instantly, deliver visual results, and accelerate onboarding while tracking progress to keep clients engaged and protected.
Read MoreRisk Management
Gain immediate insight into clients’ risk posture with an automated, guided assessment. Auto-generate risk registers and remediation plans tailored to each client, delivering visibility and clear mitigation paths across domains.
Read MoreTPRM
Assess, monitor and manage third-party vendor risk alongside internal security posture in one platform. Streamline vendor assessments, automate scoring, and turn findings into services to strengthen client security and unlock revenue opportunities.
Read MoreThe Cynomi Process:
From Assessment to Impact
Cynomi guides you step by step through managing cybersecurity and compliance.
- Speed up client discovery and onboarding with guided, interactive risk assessments
- Seamlessly integrate results from third-party scanners like NESSUS, Qualys, or Microsoft Secure Score – or run Cynomi’s built-in scan
- Instantly analyze security posture, identify gaps and set goals
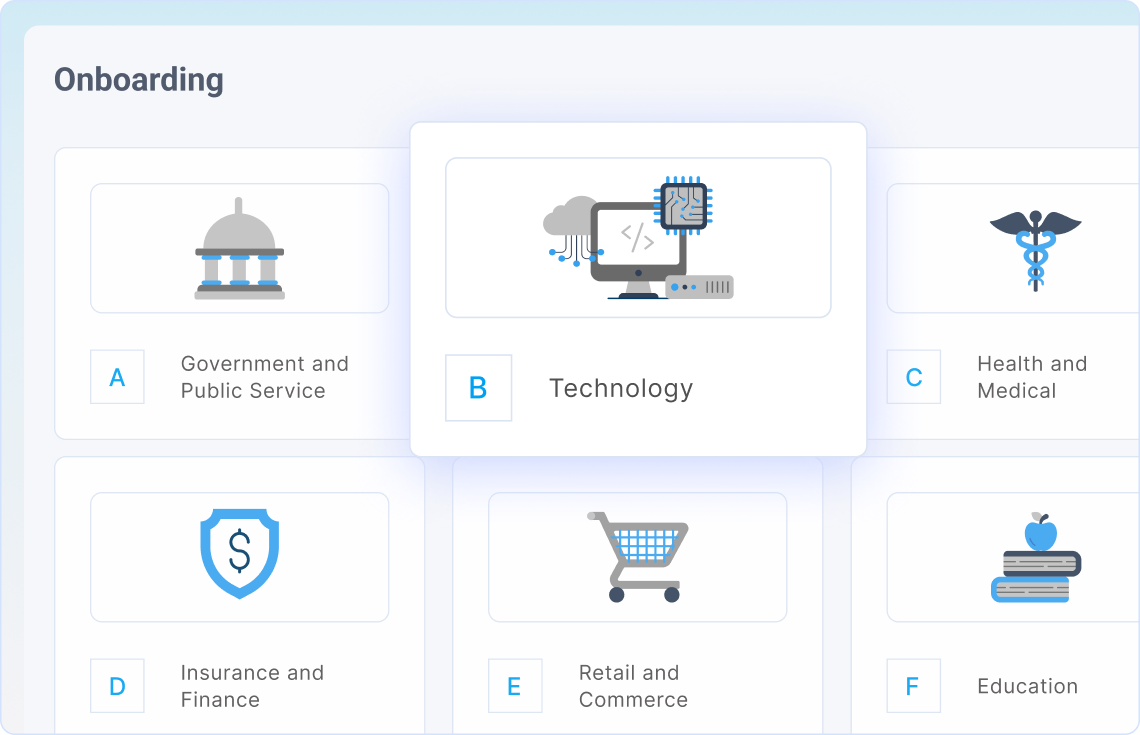
- Auto-generate client-specific security and compliance policies tailored to industry, size, and needs, powered by expert CISO knowledge
- Generate a unified risk and compliance action plan with step-by-step remediation tasks
- Align cybersecurity programs to client business goals with interactive, streamlined Business Impact Analysis and Business Continuity Planning
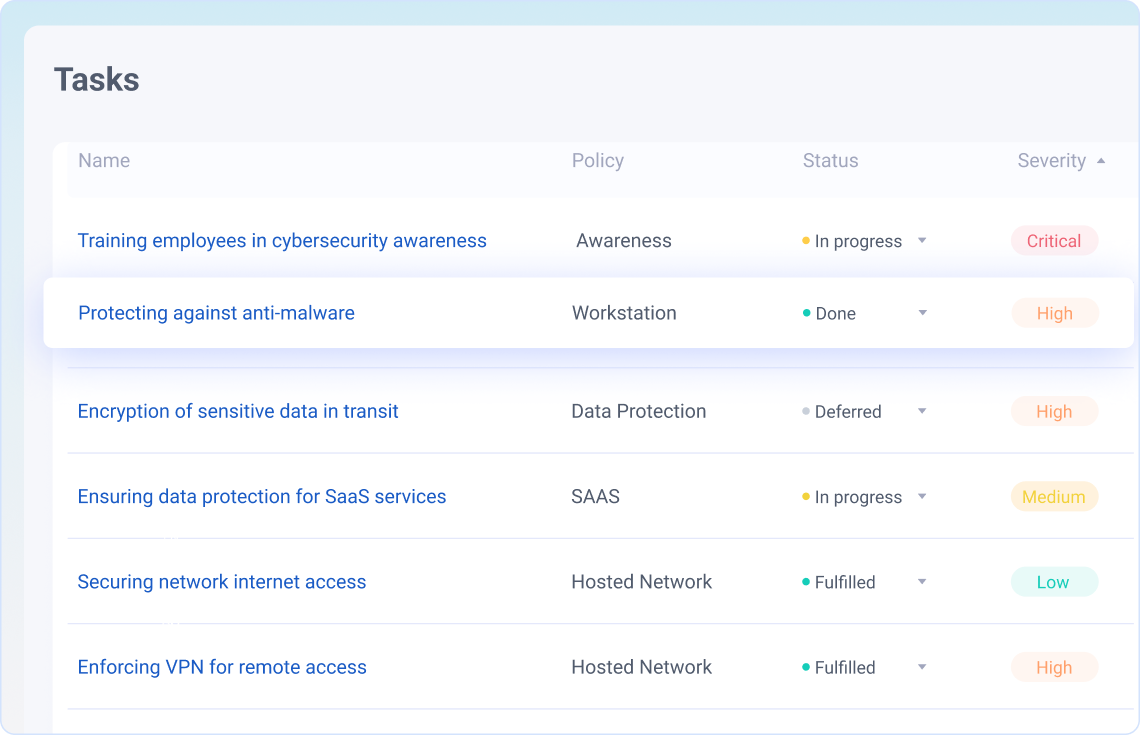
- Gain full visibility and manage all tasks from a single centralized dashboard
- Automatically track improvements to security posture and compliance readines
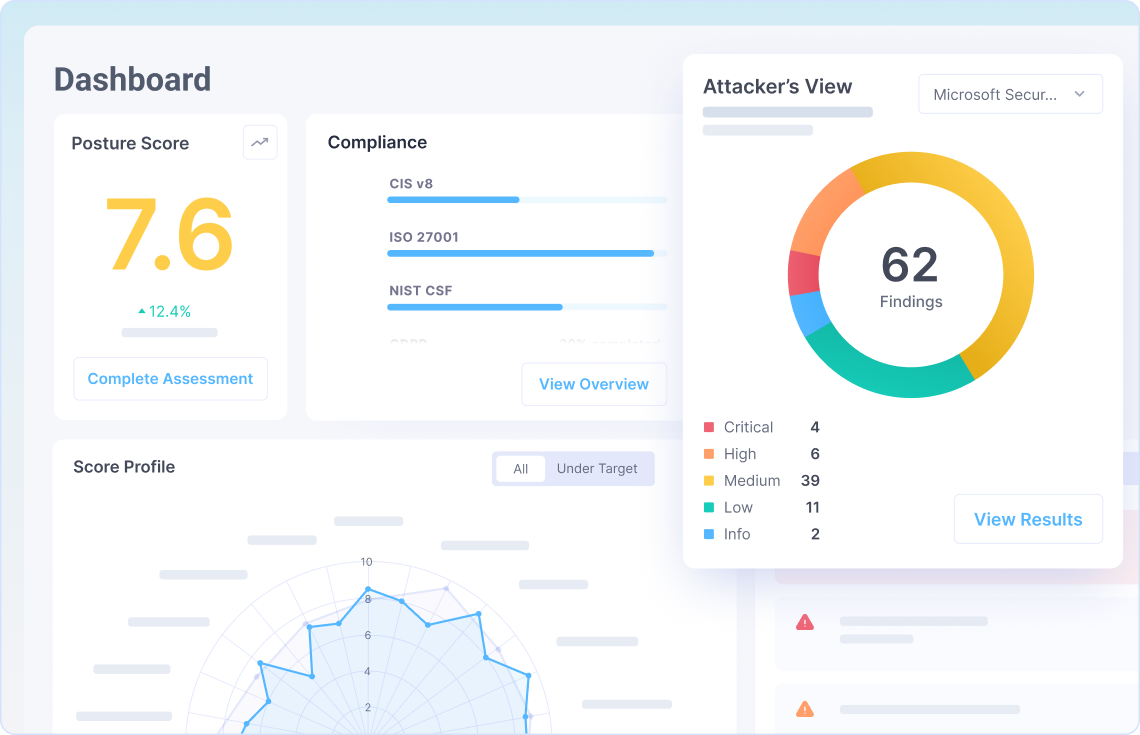
- Instantly demonstrate value with custom-branded, board-ready reports at any stage
Efficiency that Fuels Growth
Service providers use Cynomi to deliver high-impact cybersecurity and compliance services – faster, smarter, and with fewer resources.



