
It’s 3 a.m., and the breach alarms go off. Now what? Your team scrambles to log, identify, and contain the threat, and every second feels like a ticking time bomb. It’s not just the hackers you’re racing against—it’s human error, slow communication, and the limitations of manual processes.
An Apple-sponsored study found breaches in the first nine months of 2023 shot up by 20% compared to the previous year. With threats escalating, there’s no time for hesitation. In cybersecurity, speed is survival, and automated incident response (IR) offers the kind of speed that human teams simply can’t match.
What is automated incident response?
Automated incident response (IR) leverages machine learning to detect, analyze, and respond to threats faster than a human ever could. It often involves using a platform or software that orchestrates and automates tasks to combat threats like data breaches, malware infections, and denial-of-service attacks.
Traditionally, when something goes wrong, humans have to step in to look at logs, identify the source, and decide on containment steps. Automation flips that. When a risk pops up, predefined automated workflows kick into gear: threats are contained, systems are secured, and the incident is logged for later review—all within seconds, not hours.
Here’s a high-level overview of what a typical manual incident response looks like:
- Incident Detection: You detect the threat. Maybe through a log or a user report.
- Initial Analysis: Your team scrambles to analyze it. Is it serious? What systems are affected?
- Containment: Now comes the fire drill—isolating the threat to keep it from spreading.
- Mitigation: You apply fixes to eliminate the root cause.
- Recovery: Finally, you restore systems and figure out how to avoid this next time.
However, these manual steps take time. In contrast, by the time your human team even registers the breach, automation has already begun isolating the threat, protecting key systems, and kicking off recovery protocols. It’s an essential inclusion for the security and compliance of incident response efforts.
Why Automated Incident Response Is Essential
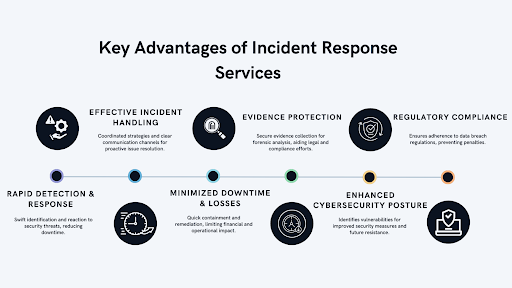
Speed
In cybersecurity, speed is everything. A few minutes can mean the difference between containing a breach and allowing an attacker to exfiltrate sensitive data. Automated incident response tools can react in real-time, drastically reducing the time it takes to isolate and address threats.
Consistency
Humans are great at adapting but prone to fatigue and error. Automated systems, by contrast, follow predefined workflows flawlessly, ensuring that even under pressure, nothing gets missed. Whether it’s 3 a.m. or 3 p.m., the response is the same: fast, accurate, and complete.
Scalability
As organizations grow, so do their cybersecurity needs. Manual incident response processes cannot be scaled without hiring exponentially more staff, which isn’t feasible for most companies. Automation allows your response capabilities to scale with your organization, handling increasing volumes of threats without added human workload.
Cost Efficiency
A faster response minimizes the impact of a breach, reducing downtime and limiting financial damage. By automating incident detection, containment, and initial mitigation steps, organizations can save significant resources that would otherwise be spent on manual responses or, worse, cleaning up after a large-scale breach.
Learning and Improvement
With machine learning, automated systems can continuously improve. Every incident provides data that refine algorithms, making the system better at detecting future threats. Human teams, while invaluable for oversight and complex decision-making, simply can’t evolve at this pace.
6 Steps to Implement Automated Incident Response
1. Pick the Right Tools
Automation is only as good as the tools you use. Security Orchestration, Automation, and Response (SOAR) platforms and Endpoint Detection and Response (EDR) tools are essential. These systems integrate seamlessly with your existing security architecture, automating everything from detection to mitigation.
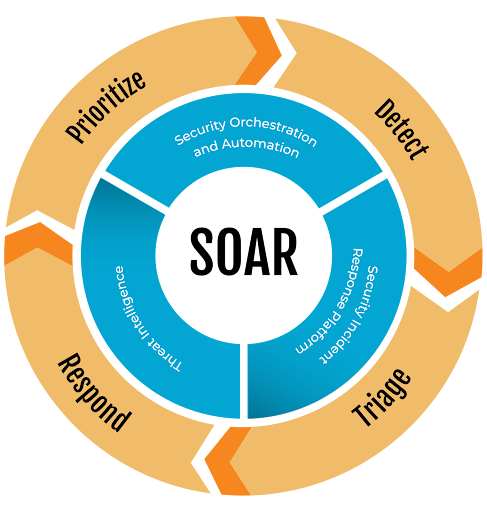
2. Feed Your System Real-Time Threat Intelligence
Automation doesn’t work in a vacuum. It needs data—lots of it. Integrating real-time threat intelligence allows your automated system to stay current on the latest attack methods and adapt its response accordingly. This kind of data comes from both internal sources (logs, events) and external feeds (threat intelligence providers).
3. Define Your Workflows
Your organization’s risk tolerance and security priorities will dictate how your automated workflows are structured. Decide which incidents get handled automatically and which need human oversight. For example, automated systems might deal with a low-severity phishing attack, but a sophisticated malware infection could trigger a human-in-the-loop process.
4. Leverage AI and Machine Learning
The beauty of automation is that it learns. AI-driven automation uses machine learning to spot trends in your data and adapt to new threats as they emerge. It isn’t just about responding to incidents—it’s about anticipating them. The more data your system processes, the better it gets at predicting and preventing future attacks.
5. Test, Test, and Test Again
Automating your incident response doesn’t mean you set it and forget it. Regular testing through incident simulations or controlled breaches helps ensure that your workflows function correctly in real-world scenarios. It helps you find weaknesses in the system before attackers do.
6. Train Your Team
Automation is a powerful tool, but it’s not a replacement for human intelligence. Your team still needs to monitor the system, manage workflows, and intervene when things go sideways. Train your staff on using your automation tools effectively and understand when to step in for manual intervention.
Key Use Cases for Automated Incident Response
Here’s where automation proves its worth:
1. Phishing Attack Mitigation:
Automated systems can detect phishing emails, block malicious links, and flag affected users in real-time, preventing damage before it spreads.

2. Ransomware Containment:
When ransomware is detected, automation immediately isolates infected systems and initiates a recovery process, minimizing data loss.
3. Unauthorized Access Attempts:
Automated IR flags suspicious login activity, locks compromised accounts, and alerts security teams before a breach occurs.
4. Data Exfiltration Prevention:
When abnormal data transfer rates are detected, automated systems can shut down the transfer, block the attacker’s unauthorized access, and log the incident for further investigation.
Before Automation, You Need an Incident Response Policy
Automated incident response allows organizations to keep pace with increasingly sophisticated threats, offering speed, accuracy, and scalability that human teams alone can’t match. But before you can automate, you need clear plans and goals—and that starts with your IR policy.
Cynomi provides MSPs/MSSPs with the tools to automate the creation of a tailored IR policy, enabling them to guide clients in taking the first step toward total IR automation. With a customized policy in place, MSP/MSSP clients are better prepared to implement advanced automation tools for incident response, making their security infrastructure both proactive and resilient.
Cynomi’s AI-powered platform provides a built-in incident response policy template and automates readiness assessments for each of your client’s unique IR, compliance, and security efforts. Plus, with helpful reporting features, MSPs/MSSPs can communicate the progress and success of IR policy creation clearly to client stakeholders, enabling clients to prepare early for the first step in their IR automation journey.
Ready to get started? Request a demo to see how the platform can help MSPs/MSSPs automate the future of incident response.