
Cyber risk unites all organizations, from new startups to well-established enterprises. Businesses strive to reduce their cyber risk to avoid costly breaches and comply with increasingly stringent data protection and system reliability laws.
But there’s a problem—risk assessment specialists are hard to come by. As many as 71% of organizations admit that the cybersecurity skills shortage has already had a negative impact. Organizations that lack in-house risk expertise often turn to MSPs and MSSPs to deliver this service for them, giving them peace of mind.
The World Economic Forum estimates that by 2030 there could be a global talent shortage of more than 85 million cybersecurity professionals. Risk assessment training benefits individuals, organizations, and MSPs/MSSPs in different ways (as we will explore in this article), ultimately helping close knowledge gaps and keep businesses secure.
What is cyber risk assessment training?
Risk assessments are one of the foundations of any risk management strategy. They employ various methodologies and frameworks to identify, analyze, and evaluate potential cyber threats to an organization and their potential impact. Security risk assessments templates aim to aid decision-makers in making informed choices regarding cybersecurity investment and where it is needed most.
To perform a risk assessment professionally and effectively requires specific skills, knowledge, and hands-on experience with relevant cybersecurity tools and platforms. To acquire these, individuals can turn to risk assessment training courses, some of which also provide accreditation upon completion.
Risk assessment training can be provided in many different ways:
- As a university or college course.
- As a free online course, such as those provided by the CIS.
- Paid online risk assessment training, like the options offered by SANS.
- In-house risk assessment training through skill-sharing programs within the organization.
Who needs cyber risk assessment training?
Cyber risk assessment training is designed for a variety of roles in organizations and among service providers, including:
- Auditors
- Risk protection and fraud professionals
- IT team members
- Cybersecurity professionals
- Compliance professionals
- Legal experts
5 Reasons Why Risk Assessment Training is Important
Risk assessment training benefits various roles in your client’s business in different ways.
Benefits of Risk Assessment Training for IT and Risk Professionals
1. Professional development and employment opportunities
Many risk assessment training courses offer accreditation and certification, meaning professionals in IT and risk management fields can increase their market value and broaden their overall skillset with a highly demanded proficiency.
Benefits of Risk Assessment Training for Businesses
2. Proactive risk management and stronger security posture
Cyber risk mitigation is vital for any organization, and risk assessment training is at the heart of the process and strategy. When in-house IT and risk management teams are skilled in proactively identifying, assessing, and managing cyber risks, companies can enhance their overall security posture and stay ahead of vulnerabilities and potential threats.
3. Informed decision-making and effective resource allocation
Through risk assessment training, business leaders can fully understand the cyber risks threatening the organization and make strategic decisions to ensure optimal resource investment. For example, they can implement the necessary security controls, adopt appropriate tooling, and employ risk management best practices.
4. Streamlined compliance audits
By providing comprehensive risk assessment training to compliance, risk, and fraud teams, businesses can bridge the gaps between information security and IT teams and the non-technical stakeholders in legal and compliance departments.
Benefits of Risk Assessment Training for Managed Service Providers
5. Customer retention and upsell opportunities
Regulatory requirements, partner demands, and the high cost of skilled cybersecurity expertise are just some of the factors pushing small and medium businesses to seek out managed security solutions, including cyber risk management services like risk assessment training. When clients lack the ability to conduct risk assessment training in-house, they can turn to MSPs/MSSPs.
7 Core Principles for Risk Assessment Training
Risk assessment training courses differ according to their scope, depth, target audience, and more. Here are some of the main topics and principles traditionally covered in risk assessment training.
1. The Fundamentals of Cyber Risk Assessment and Management
The first core principle of risk assessment training covers the basics of cyber risk management. These usually include:
- The definitions of business risk, cyber risk, and related terminology.
- The base components of risk, including assets, threats, and vulnerabilities.
- Risk management tiers in an organization.
- Response vs recovery.
- The risk equation and its role in risk assessment processes.
- Qualitative vs quantitative risk assessments.
2. Identifying Risk Assessment Requirements
With the basics in place, the next principle is about identifying and collecting the specific information and data required to assess the risk for an organization. Since the requirements are unique to every organization, this principle includes aspects such as:
- Gathering information.
- Outlining the scope and boundaries of the risk assessment.
- The roles and responsibilities of the parties involved in the risk assessment process.
- Business continuity, incident response, and risk.
- Business risk impact analysis.
- Operational resilience assurance.
- Asset categorization.
- How to prepare for a risk assessment.
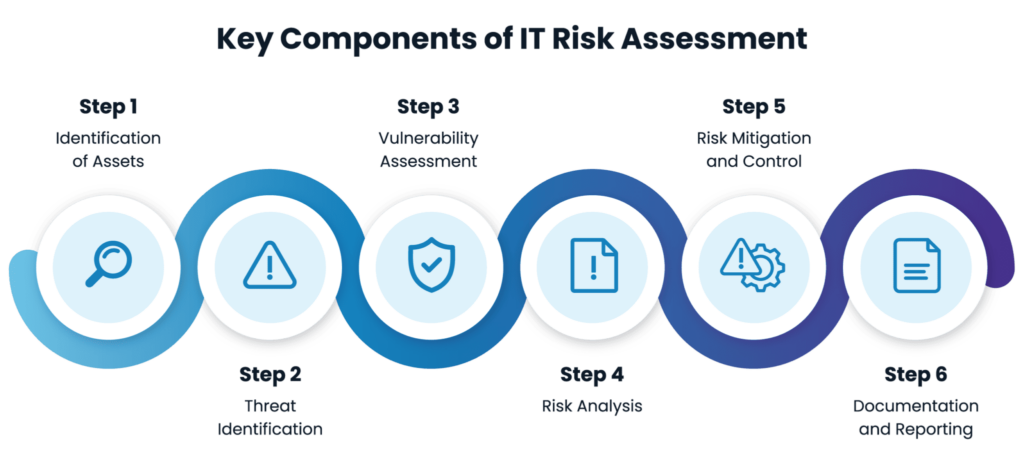
3. Selecting and Customizing the Appropriate Risk Assessment Standard or Framework
This principle of risk management training is especially versatile, as it differs significantly according to local regulations and cybersecurity laws, as well as different industries with specialized risk assessment standards. Some risk assessment training courses also include chapters on designing your own risk assessment framework. This principle typically addresses:
- Standards for risk management hierarchies and frameworks.
- Risk and threat modeling.
- Common risk assessment standards, methodologies, and frameworks like NIST SP 800-30, CISA OCTAVE ® (Operationally Critical Threat, Asset, and Vulnerability Evaluation), CIS RAM, CERT-RMM, and others relevant to your client’s specific industry.
4. Conducting a risk assessment
The next principle in the risk assessment training process entails learning the practicalities of applying cyber risk assessment frameworks to any specific organization or project. Skills required for this stage include:
- Identify and analyze vulnerabilities.
- Understand security controls, parameters, and enhancements.
- Define and set a security control baseline.
- Set acceptable risk tolerance and appetite.
- Determine likelihood and business impact.
- Understand how risk can be reduced through the implementation of security controls.
5. Effectively Implementing Applicable Security Controls
Next, it’s important to learn more about security controls, authorization, authentication, and other methods of reducing risk by implementing the applicable security controls. This core principle, therefore, focuses on topics like:
- Embedding security best practices to minimize risk.
- How to choose validated components to strengthen security posture.
- Reducing legacy system risk with add-on elements.
- How to select the appropriate security controls.
- Understand the topics of risk-based authorization, security authorization packages, and identity and access management (IAM).
- Applying framework-specific security controls (such as ISO, NIS2, etc).
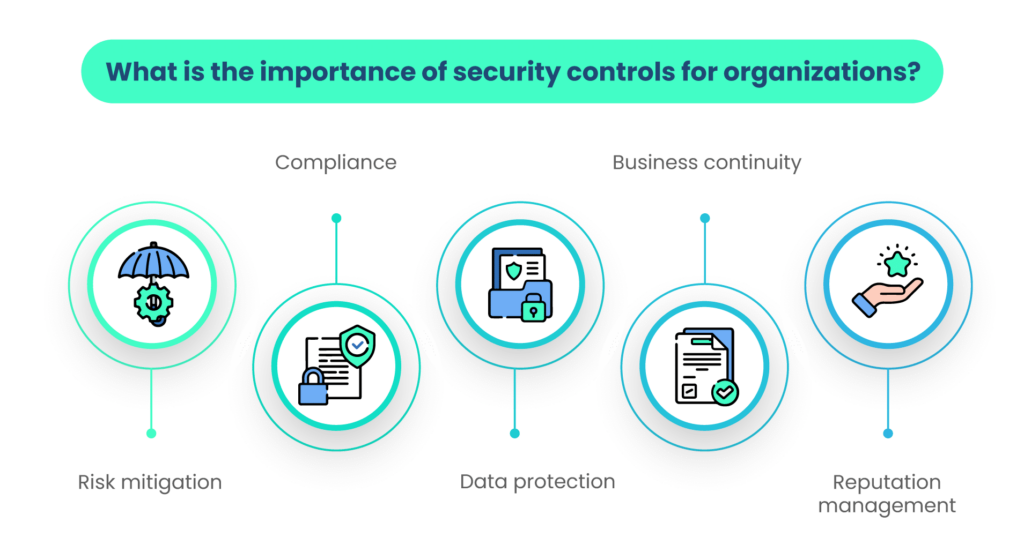
6. Cyber Risk Mitigation Strategy Maintenance
Often, the organization will already have a cyber risk mitigation strategy and risk assessment methodology in place. This core principle involves continuous maintenance of risk assessment and management protocols. These typically include:
- Continuous risk monitoring strategies.
- Account and system removal and decommissioning processes.
- Risk assessment planning.
- Reviewing risk assessment plans.
- Updating risk assessments.
7. Reporting and Compliance Auditing
Regulatory requirements and standards are one of the main drivers for performing risk assessment training and risk assessments. Therefore, professionals undergoing risk assessment training need a comprehensive understanding of the role of security controls and risk management in compliance assessments. Depending on the depth and scope of the risk assessment training course, the topics under this principle may include:
- Assessing compliance.
- Verifying compliance (through examinations, tests, etc).
- Aligning ownership and responsibility.
- Coordinating implementation across technical, operational, and administrative controls in the organization.
- How to develop and review security impact assessments.
- Providing evidence of compliance.
Assessing Cybersecurity Risk at Scale with Cynomi
Cybersecurity risk assessment training helps IT and risk management professionals gain the necessary skills to perform risk assessments for their organizations or as external consultants for small and medium-sized organizations. Risk assessment training is a wise investment in 2024 and covers a wide range of topics, from risk assessment frameworks to compliance auditing and reporting.
For MSPs/MSSPs looking to scale their cybersecurity risk assessment and management services, Cynomi’s vCISO platform is a go-to solution for risk assessment automation and reporting. Even those without formal risk assessment training can leverage Cynomi’s intuitive, step-by-step guidance and embedded knowledge base to conduct thorough assessments.
Cynomi features self-guided discovery questionnaires to expedite and streamline risk assessment processes, plus automated scans to uncover vulnerabilities and weaknesses in externally visible resources. In addition, Cynomi helps prepare your customers for compliance audits with one-click benchmarking of each client’s cyber risk profile against industry standards and global regulatory requirements.
To discover how Cynomi can help you scale your cybersecurity offering and automate risk assessments for your clients, book a demo.