
On any given day, MSPs/MSSPs manage several clients. One client wants rapid security updates, another is dealing with strict industry-specific regulations, and yet another has sensitive data at risk. It’s a constant juggling act, with new regulatory changes and cyber threats left, right, and center. Missing something isn’t just costly in terms of fines—it’s about your clients losing the trust they’ve worked hard to build.
Thomson Reuters is reporting “regulatory fragmentation” due to the rise of AI and eCommerce fraud for 2024. As a result of headline news like this, different regions are starting to implement varying regulations in response to new technologies and fraud challenges. As a result, MSP/MSSP clients must navigate an increasingly complex compliance landscape, which is where compliance risk management best practices can help.
Compliance Risk Management 101: What It Is and Why It Matters
Compliance risk management is foundational to gaining visibility over cybersecurity risks and compliance failings. It offers insight into vulnerabilities and supports the creation of targeted strategies.
The goal for MSPs/MSSPs is straightforward yet challenging: ensure your clients’ organizations follow all relevant laws, standards, and internal policies. Effective compliance risk management protects against looming consequences like financial penalties, shields client reputations, and keeps operations running smoothly. For MSPs/MSSPs and their clients alike, it’s about maintaining trust, meeting requirements, and ensuring business continuity.
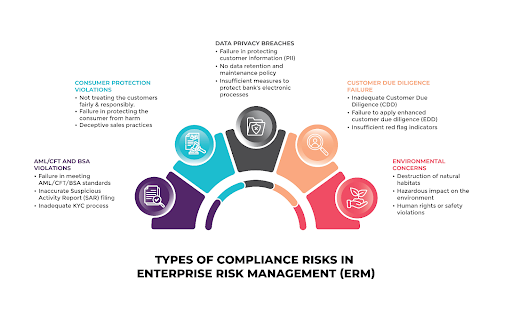
| Type of Compliance Risk | Description |
| Regulatory Risk | Fines and sanctions for failing to meet industry regulations. |
| Reputational Risk | Negative publicity damages clients’ brand image and customer trust. |
| Operational Risk | Service disruptions caused by compliance-related issues. |
| Cybersecurity Risk | Vulnerabilities leading to data breaches and unauthorized access. |
5 Steps to Conduct Compliance Risk Management Assessments
A solid risk assessment is at the heart of any effective compliance risk management program. Risk assessments help MSPs/MSSPs identify weak spots and build a framework for clients to meet regulatory requirements. Conducting compliance risk management assessments boils down to five key steps.
- Define Scope and Objectives: Start by determining which compliance frameworks are relevant to your client’s industry, such as GDPR, HIPAA, or PCI DSS. You can also open conversations to understand the client’s specific business activities, data processing practices, and locations, as these factors influence which regulations apply.
- Risk Identification and Analysis: Identify potential risks through strategies like vulnerability scans, security policy reviews, employee interviews, and risk assessments.
- Risk Evaluation: Quantify risks in terms of the likelihood and potential business impact.
- Prioritize and Mitigate Risks: Address the highest-impact risks first. For example, prioritize vulnerabilities that expose personal health information (PHI) over less critical issues.
- Use a vCISO Platform: To maximize efficiency, MSPs/MSSPs can use a vCISO platform to automate compliance assessments. For example, Cynomi speeds up the risk assessment process from days to hours by automating it with easy-to-complete custom-made questionnaires and automatic compliance mapping.
5 Best Practices for Compliance Risk Management Processes
Compliance risk management is a process of guiding clients to be proactive, not reactive. Frameworks and best practices offer a structured way to handle threats, and risk assessments bring focus by pinpointing vulnerabilities and their impact. MSPs/MSSPs need structure and strategy to manage compliance risks effectively for clients.
1. Adopt a Framework
MSPs/MSSPs can rely on structured frameworks like ISO 27001 or NIST to manage compliance risks effectively, ensuring data security best practices and consistent compliance success across all clients. Some tasks MSPs/MSSPs might follow under these frameworks include implementing regular audits and using performance metrics to measure adherence.
Types of Compliance Risk Management Frameworks
- ISO 27001: A globally recognized standard for managing information security risks, helping organizations protect their valuable data and systems through a systematic approach. ISO is also developing new frameworks, such as ISO 42001, in line with new topics of conversation in the compliance space, like AI.
- HIPAA: A US law that safeguards patient health information by setting strict rules for how healthcare providers and related businesses handle sensitive medical data.
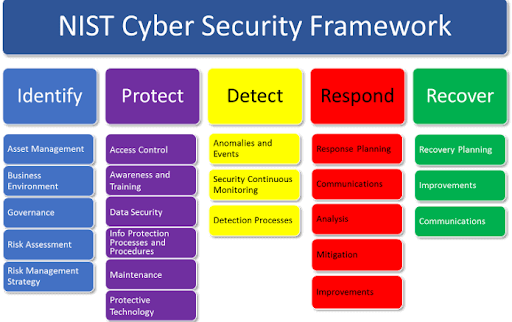
- NIST Cybersecurity Framework: A voluntary set of guidelines and best practices that companies can follow to improve their cybersecurity posture and manage risks effectively.
- SOC2: A framework that enables businesses to prove that they handle customer data securely and responsibly.
2. Automate Compliance Tasks
Scaling compliance operations is challenging, especially with a growing client base with diverse needs. Automation makes compliance activities manageable by reducing human error, keeping operations efficient, and ensuring MSPs/MSSPs stay ahead of regulatory demands for clients.
You can also turn to automation compliance platforms and solutions like vCISOs and GRC software to offload tasks like risk assessments, compliance gap analysis, and reporting. With automation as a copilot, MSPs/MSSPs can streamline the delivery of compliance risk management to each client.
3. Focus on High-Risk Areas
Not all risks are created equal; MSPs/MSSPs must support clients by prioritizing high-risk areas that pose the greatest threats. You could start by creating a risk assessment table that quantifies risks based on the likelihood and severity of the impact.
Once high-risk areas are identified—such as unencrypted customer data or outdated software—it’s time to act. Deploying safeguards like encryption, multi-factor authentication, and endpoint protection can mitigate these vulnerabilities and support compliance risk management efforts by helping your client prove they are focused on closing compliance gaps.
4. Employee Training and Awareness
Compliance isn’t just a technical challenge; it’s a people problem. Studies show that human error accounts for 74% of data breaches, making employee awareness a crucial component of compliance risk management strategies. For MSPs/MSSPs, this means advising clients on the importance of training—and emphasizing that it doesn’t need to be boring!
Gamified learning modules, interactive workshops, or role-based scenarios like phishing awareness training can help clients keep employees focused on the training and maximize the positive impact of the cyber training. For example, an MSP/MSSP serving financial clients could encourage them to host quarterly role-playing workshops to keep staff updated on SEC regulations.
5. Document Everything
For MSPs/MSSPs, maintaining detailed compliance records not only prepares clients for audits but also provides a defensible position if issues arise. Automated tools like Cynomi’s vCISO platform help you generate and maintain compliance logs effortlessly, ensuring no critical details are missed.
Let’s pretend we have a GDPR audit on our hands. An MSP/MSSP equipped with automated documentation tools can provide regulators with a complete record of compliance activities, showcasing the client’s due diligence and avoiding penalties. By taking the lead in documentation, MSPs/MSSPs position themselves as trusted partners in their clients’ compliance journeys.
Automate and Accelerate the Delivery of Compliance Risk Management Tasks with Cynomi
Compliance risk management is not just about adhering to legal requirements—it’s about proactively mitigating risks that can threaten an organization’s very existence. With increased regulatory demands and a rapidly evolving threat landscape, the complexity of compliance has grown significantly—too much for some clients to handle alone without the support of an MSP/MSSP.
Cynomi can dramatically reduce the manual work in conducting compliance and risk assessments for multiple clients, speeding up the process from days to hours. Cynomi’s vCISO platform tailors the relevant questionnaires and scans to automatically build each client’s cyber profile, using guided questionnaires and express scans to uncover critical vulnerabilities. Cynomi automates compliance mapping and links activities to their impact on compliance adherence, saving manual work and precious time.
Ready to simplify compliance? Book a demo to explore how Cynomi can streamline your compliance processes, reduce manual work, and enhance security for your clients.