
Your clients are attractive targets for swindlers and bad actors. Can you really trust that their organization won’t fall victim to ill-intended third-party vendors or a new hire with a suspicious background? It’s easy for your clients to say that these situations would never happen to their company or employees, but as an MSP, it’s your job to convince them otherwise.
Phishing attacks remain the most common type of fraud, with 43% of global merchants in the eCommerce industry falling victim. Over in the finance industry, the statistics are equally harrowing – the attempted fraud rate for international payments increased by 31% in the first few months of 2023.
While you can’t take on the role of a dragon protecting your clients’ golden assets, you can do the next best thing: Conduct a fraud risk assessment and be proactive against these threats.
What is a fraud risk assessment?
A fraud risk assessment is a set of processes MSP/MSSPs can follow to identify, analyze, and remediate potential fraudulent activities affecting clients. It covers external threats like hacking and phishing as well as internal risks such as embezzlement.
Every fraud risk assessment method is different depending on your client’s industry and company. Although industries like financial services are commonly mentioned in the same sentence as ‘fraud’, the reality is that anyone can commit fraud if they have a motive, which means any business – no matter the size or industry – can be a target.
What are the types of fraud risks?
There are many different types of fraud risks, so let’s look at three of the most common threats MSPs might encounter.
1. Identity Theft
Identity theft is a unique type of fraud in which a bad actor illegally obtains personal information and uses it without permission. Social engineering attacks like phishing open the gateway for identity theft – just one fake email could coerce an unsuspecting employee to reveal their credit card details, Social Security number, or address.
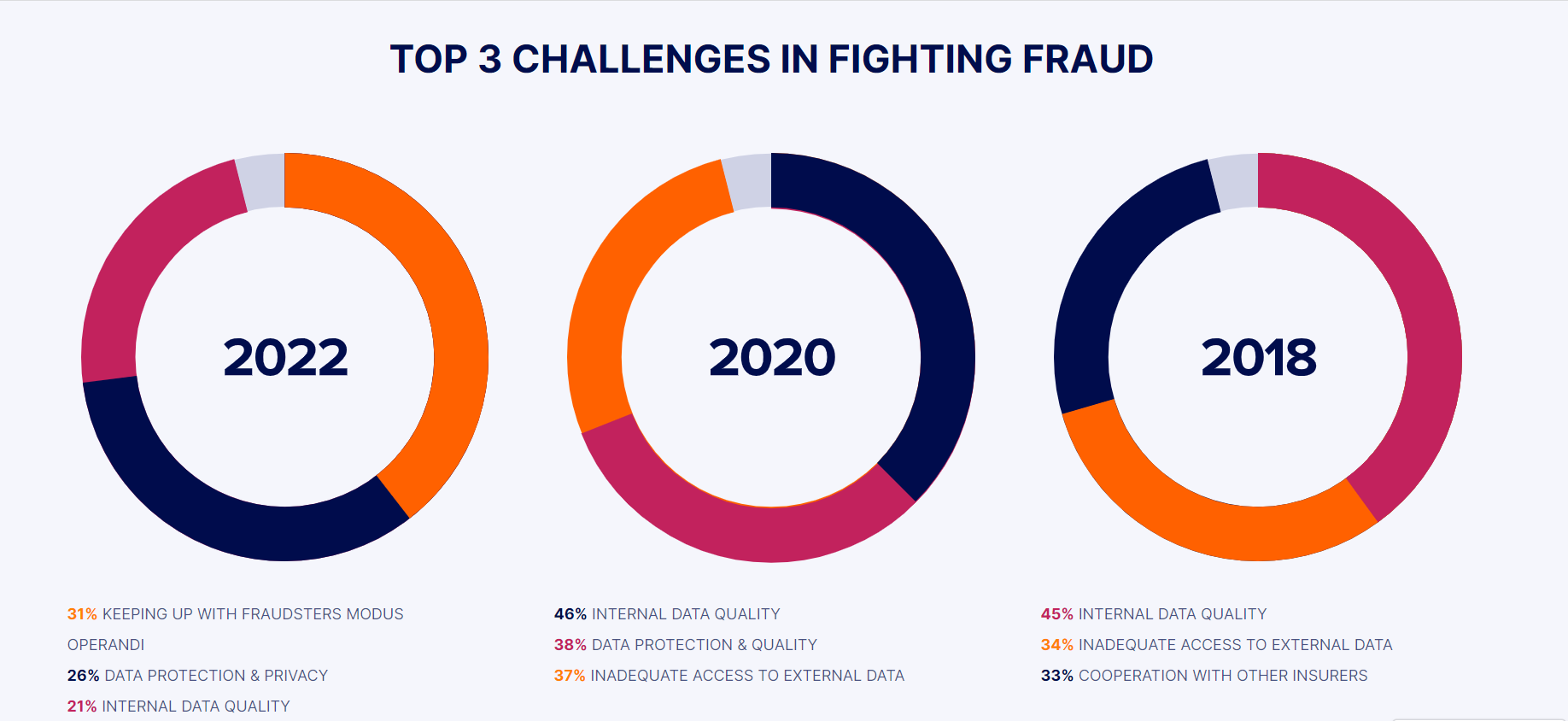
2. Reporting Fraud
Reporting fraud covers financial and non-financial incidents. It happens when an internal source deliberately misrepresents reports or statements. In most cases, the goal is to inflate a company’s achievements and stability and deceive third parties like investors. Common examples of reporting fraud include understating expenses and modifying compliance records.
3. Regulatory Compliance Fraud
In fact, modifying compliance records is serious enough to fall into its own category. MSP/MSSPs know firsthand how challenging it is to uphold compliance expectations, from SOC2 in cybersecurity to HIPAA in healthcare. Companies may be tempted to provide false information to appear compliant with laws, regulations, and industry standards.
Why You Need a Fraud Risk Assessment
Meet Regulatory Expectations
Your clients must prove to regulators in their industry that they prioritize fraud prevention. Otherwise, they risk penalties and a possible legal fight – and they could even fall into the ‘compliance fraud’ category in the eyes of the law.
Protect Your Resources
Bad actors rarely commit fraud because they’re bored. There’s always a motive, usually to steal or access your clients’ financial or technical assets or other resources. A fraud risk assessment ensures every type of fraud threat is on your radar so your clients don’t leave the metaphorical door unlocked.
Uphold Your Reputation
End users won’t blame themselves for falling victim to a website spoofing scam or a fake ‘thanks for your order’ text. Instead, they’ll blame your clients. A fraud risk assessment helps you take every possible precaution to protect your clients’ reputations and customer trust, even if an incident occurs.
5 Components Every Fraud Risk Assessment Must Have
1. Identification
Although this step is called ‘identification,’ it’s pretty similar to ‘investigation’. You can put on your detective’s hat to interview and observe your clients’ operations, aiming to find out which fraud risks affect their company.
At this stage, you should accurately identify all relevant types of fraud risks, from expense manipulation to asset theft and phishing attacks. You can gather data or industry-wide knowledge that will help inform your awareness of fraud and security gaps. You can ask questions like:
- What policies, controls, or prevention measures does the client currently have in place?
- What existing resources or technology does the client have to mitigate the risks?
- How aware are employees of possible fraud risks and prevention strategies?
2. Prioritization
No matter how many fraud risks your assessment identifies, the fact is that they will not have equal weighting. Therefore, you should prioritize and quantify risk management based on factors such as:
- How prevalent are the risks? How likely are they to occur?
- What are the financial and legal liabilities?
- What are the reputational and operational impacts?
- What audits, processes, or next steps do you recommend implementing immediately?
You can seek guidance from a risk assessment table, otherwise known as a risk assessment matrix, to assign a score to each item classified in the fraud risk assessment. For example, you could define the likelihood of the fraud risk using the following perimeters:
- High: Annual occurrence or more frequent.
- Medium: Occurs every three to five years.
- Low: Occurs every five to ten years.
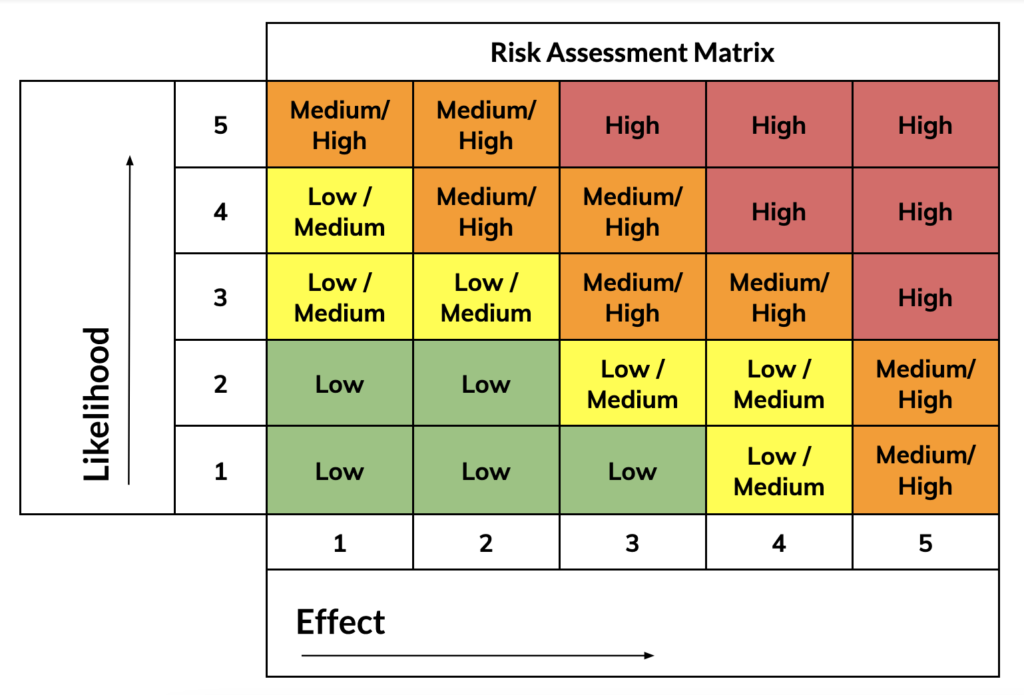
3. Prevention
Prevention is about going above and beyond to stop fraud from affecting your clients. Effective strategies include:
- Implementing continuous security risk assessment template monitoring tools for all clients.
- Implementing an identity and access management (IAM) policy to better control who and what can access your clients’ resources.
- Conducting regular fraud awareness training, possibly in tandem with other sessions like phishing awareness.
At the prevention stage, you can also guide your clients on what exactly defines a fraud incident so there’s no confusion over internal or external fraudulent behavior.
4. Detection
Let’s assume the worst-case scenario – your client, a vendor, or an employee has been tricked, and a fraud incident has occurred. The fraud risk assessment outlines exactly what your client should do and how to do it to avoid a panicked frenzy during an event.
At the fraud detection stage, the assessment should cover investigation protocols like:
- Who should act, and what their individual responsibilities should be. For example, terminating the activity.
- Who to inform, such as law enforcement or regulatory authorities.
- Who is authorized to make incident-related decisions.
- Who should record incident details, and where and how to record them.
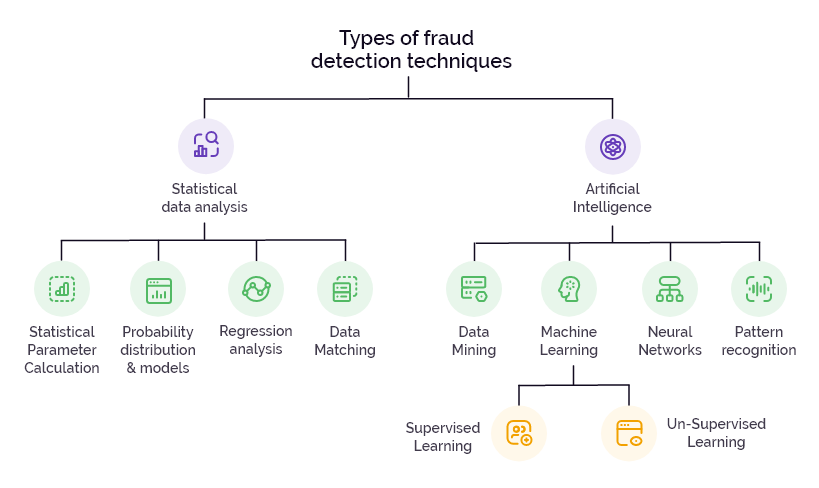
5. Monitoring and Reporting
Monitoring and reporting are the cherries that complete the fraud risk assessment cake. Continuous monitoring and fraud detection tools detect anomalies and behavioral changes in everyday activities, helping you identify incidents quickly before they negatively impact your clients.
The fraud risk assessment should outline a long-term and ongoing review process that determines when and how it should be updated, and who is responsible for making it happen. Treating the assessment like an ongoing priority helps your client integrate and communicate the fraud risk strategy across departments, vendors, and stakeholders.
After completing any review, update, or audit, you should communicate the fraud risk assessment results and new actions to the relevant client stakeholders and departments.
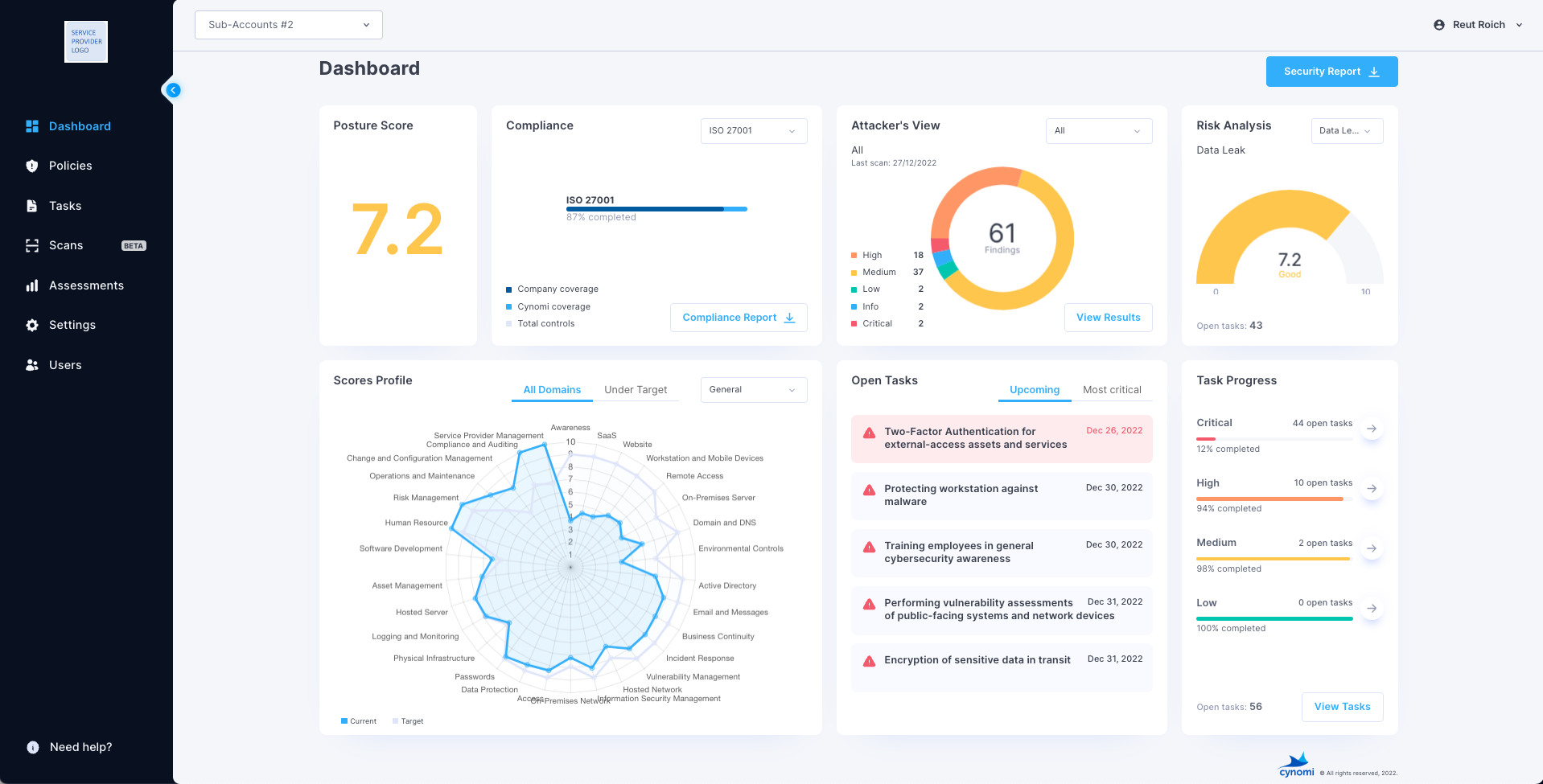
Tailored Fraud Risk Assessments For Every Client
Cynomi’s AI-powered, automated vCISO platform helps MSPs/MSSPs deliver comprehensive risk assessments to each client, including automatically-generated tailored policies and strategic remediation plans with prioritized tasks. When measuring risk, Cynomi looks at four different risk areas, and one of them is fraud.
Cynomi tailors the relevant questionnaires and scans to automatically build each client’s cyber profile. After all, a large financial services organization will have different fraud concerns and compliance to consider compared to a small healthcare company.
Using Cynomi, MSP/MSSPs can offer comprehensive risk assessments at a scale that differentiates your offering without the need to develop further in-house expertise or scale existing resources. With Cynomi, you can upsell your fraud risk assessment services with ease and generate more business revenue.
Book a Demo today to discover how Cynomi can automate and scale fraud risk assessment services for your clients.