
There’s nothing wrong with getting a little help. Cyber threats, compliance requirements, and the shortage of InfoSec professionals mean businesses seek external assistance with their cybersecurity challenges. After all, it’s easier to fight the menace of cyber risk with experienced combat veterans at your side, and this support often comes from managed cybersecurity service providers.
The demand for managed cyber security services is also evident in market size projections. According to these projections, the global managed security services market is projected to grow at a 15.4% compound annual growth rate (CAGR) between now and 2030.
The Role of a Managed Cybersecurity Service Provider
An MSSP is a third-party provider that delivers outsourced monitoring and management of security devices and systems. Typically, MSSPs offer various services and products that help unload work from in-house InfoSec teams and reduce the number of personnel a business must onboard to maintain an acceptable cybersecurity posture and comply with applicable regulations.
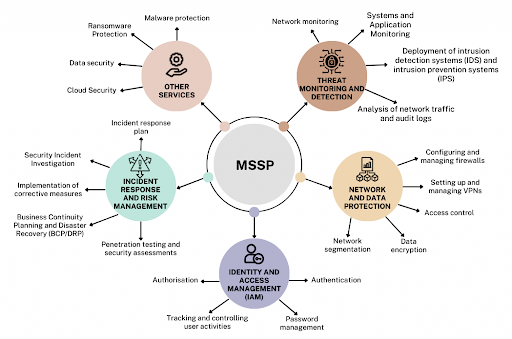
Depending on the client’s requirements, MSSPs traditionally offer intrusion detection, risk assessment, vulnerability management, and endpoint security.
Managed Service Provider (MSP) vs Managed Cybersecurity Service Provider (MSSP)
MSPs and MSSPs offer similar services but differ in their focus and expertise. An MSP typically provides general connectivity and IT services, including SaaS platforms and backup and recovery services, to deliver the connectivity and support necessary to mitigate the business impact of cybersecurity initiatives. An MSSP, on the other hand, is focused primarily on securing and protecting the data, applications, and endpoint devices in the organization.
The difference between MSPs and MSSPs is apparent in the unique expertise of their workforce, the type of operations center they use (NOC vs SOC), their tech stack, and their overall business goals.
It’s worth noting that while there is a distinction in the definition of the two types of service offerings, MSPs often expand their portfolios to include managed cybersecurity services as well.

What services do managed cybersecurity service providers offer?
Managed cybersecurity service providers usually model their offerings according to the specific needs of clients in the region or industry and the expertise and skills of the MSSP staff of cybersecurity professionals. That said, there are some services that you are likely to find in the portfolio of most MSSPs:
- Cyber risk assessments are one of the most important services for understanding the threat landscape and the risk to a client in a way that informs decision-makers in monetary terms.
- Managed detection and response (MDR) includes security event detection, alerting, remediation, and sometimes proactive threat hunting and security testing to prevent potential cyberattacks.
- Vulnerability management entails ongoing identification, assessment, documentation, prioritization, and remediation of security vulnerabilities across the client’s systems.
- Identity and access management are designed to ensure that only authorized persons and systems get access to data and applications they should. MSSPs often aid companies in setting up as well as testing their data and service access policies.
6 Tips for Evaluating Managed Cybersecurity Service Providers
Different MSSPs offer varying services and contracts and specialize in specific industries or regulatory requirements. Before you choose an MSSP that will serve your cybersecurity needs and support your in-house teams, there are a few considerations to take into account.
1. Assess MSSP Experience in Your Industry
Ensure that the MSSP you choose has relevant experience in your industry and a proven track record of understanding the specific cybersecurity challenges and compliance requirements. Verify they have deep industry knowledge and a history of working with clients in similar market conditions. Also, check that they stay up-to-date on new and upcoming threats and regulations as well as innovations in the world of cybersecurity tooling and technologies.
2. Scrutinize the Service Offering, Infrastructure, and Tech Stack
Carefully and meticulously examine the range of managed services the MSSP offers to ensure they can deliver the solutions to support your organization’s security posture and align with your cybersecurity needs and requirements. Look for MSSPs that provide a comprehensive suite of services, including tools and solutions like vulnerability management, proactive security monitoring, incident detection and response, risk assessments, and compliance monitoring, to name a few.
Pay special attention to the MSSP toolkit and infrastructure, including their security operations center (SOC) technologies, operational methodologies, and processes. Familiarize yourself with the systems they have in place, the applications they employ for collaboration with customers, and how these can interface with your organization’s existing cybersecurity and IT stacks.
One key benefit of hiring an MSSP is their ability to combine services and solutions into a cohesive suite that mitigates threats relevant to your organization. Seek out the MSSPs that excel in seeing “the big picture” and can aid in bridging the gaps you may not even be aware of in your organizational security posture.
3. Prioritize Scalability and Flexibility
The business environment, regulatory demands, and business growth all affect organizations’ cybersecurity requirements. This means that the MSSP you hire should be able to adapt and adjust your cybersecurity strategy, increasing or shrinking security coverage as needed and optimizing resource allocation and service costs.
4. Emphasize Responsiveness and SLAs
Cyber attacks and security breaches cannot be scheduled, so it’s important to thoroughly assess the Service Level Agreements (SLAs) and customer support responsiveness and availability. Make sure that these align with your business and compliance requirements, such as incident response times, communication protocols, regular updates, and collaboration protocols with the organization’s in-house InfoSec teams.
In addition, check what measures the MSSP employs to ensure that security measures are adequately maintained, updated, and adjusted as business needs shift.
5. Ensure Compliance and Look for Certifications
A big motivation for utilizing MSSPs is the need for regulatory compliance. If your business operates in a highly regulated field, be sure to evaluate the MSSP’s compliance service offerings closely to ensure that they align with your current and future compliance needs.
In addition, it’s important to remember that an MSSP, while tasked with securing an organization’s information systems, is still a third-party service provider and should be treated as such when performing due diligence. Look for compliance certifications (like SOC 2, ISO 27001, and GDPR) to ensure the MSSP follows strict security standards when handling your business’s sensitive information and mission-critical applications.

6. Check Positioning and Reviews in Relevant Directories
As with any product or service you employ, checking a vendor’s track record and reputation is important before you make any decision. When seeking out reputable and trustworthy managed cybersecurity service providers, be sure to get references from their current and past clients, plus online testimonials. Check specialized collections of MSSPs, like The vCISO Directory. These will help you evaluate the reliability, service quality, and services you can expect from the MSSP you’re researching.
Scalable MSSP Operations and Enhanced Service Delivery with Cynomi
If you are looking for an MSSP
An MSSP is, first and foremost, a trusted advisor on all things cybersecurity and should work closely with your in-house teams to align cybersecurity investments with business goals. A lot of research is needed to find the right fit, as you must evaluate numerous criteria, from industry experience to responsiveness and tech stack compatibility.
That said, hiring an MSSP that genuinely cares about enhancing the security posture of your business without overloading your in-house teams is often the only way to deal with the increasing risk of catastrophic cyber breaches and growing compliance demands.
If you are an MSSP
To attract and retain clients, you must clearly demonstrate the value of your offering and adjust swiftly to their shifting demands. With Cynomi’s vCISO platform, you can do both and easily scale operations without expanding your existing in-house expertise and resources.
Using Cynomi for risk assessment services differentiates your MSSP from competitors—our platform helps you demonstrate the clear value of your services in response to the client’s security and compliance gaps. Build an effective, tailor-made cybersecurity strategy for each client in a fraction of the time.
Discover how Cynomi’s vCISO platform can help you close gaps in your clients’ security postures.