Cyber criminals never sleep, so compliance requirements must keep moving forward to stay one step ahead. One of the EU’s many responsibilities is to set compliance standards in stone, therefore creating a standardized and optimally secure cyber ecosystem.
Cybecrime is estimated to reach over $13 billion in 2028, so it’s up to governments and regulatory bodies to lead the charge and mandate improvements across the field. A lack of vigilance doesn’t just put MSP/MSSP clients on attackers’ radars—it also negatively impacts their bottom line and reputation. NIS2 compliance requirements are the latest framework to sweep the EU, updating existing policies as threats evolve and introducing innovative new best practices.
What are the NIS2 compliance requirements?
The Network and Information Security (NIS2) directive is a set of regulations designed to enhance cybersecurity across the European Union. It builds on the original NIS1 directive but with a broader scope and stricter requirements.
NIS2 requirements vary depending on the nature of your client’s organization, however, they generally include:
Risk Management
- Conduct comprehensive risk assessments.
- Implement measures to prevent, detect, and respond to cyber threats.
- Establish incident response plans.
- Manage supply chain risks.
Cybersecurity Measures
- Enforce strong access controls and identity management.
- Protect network and system integrity.
- Implement robust data protection measures.
- Ensure business continuity and disaster recovery.
- Regularly update software and systems.
Governance and Accountability
- Provide adequate resources and training for all employees.
- Report significant incidents to the relevant national authorities within 24 hours.
- Cooperate with authorities in case of incidents.
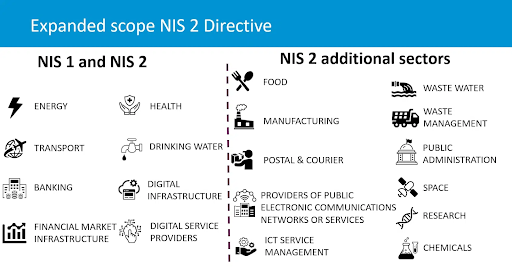
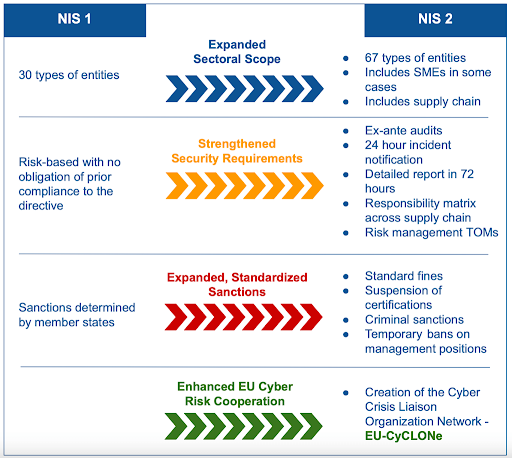
How are the NIS2 requirements different from NIS1?
| NIS1 | NIS2 | |
| Scope | Energy, transport, banking, and healthcare. | Public administration, space, food production, and manufacturing. |
| Risk Management and Security Measures | Basic cybersecurity requirements for OES (Operators of Essential Services). | Enhanced cybersecurity requirements, encompassing risk management, incident response, supply chain security, and encryption protocols. |
| Incident Reporting Requirements | Report incidents that had a significant impact on the continuity of essential services. | Incidents must be reported to national authorities within 24 hours of detection, followed by a detailed report within 72 hours. |
| Accountability and Governance | Limited focus on governance, mainly requiring organizations to appoint a point of contact for cybersecurity matters. | Top-level management must be involved in cybersecurity decision-making with an emphasis on accountability. Penalties for non-compliance include significant fines and personal liability charges. |
| Penalties for Non-Compliance | Member states imposed penalties for non-compliance, but the rules and enforcement varied widely across the EU. | Penalties across member states are more consistent, and severe sanctions for non-compliance are imposed, up to 10 million euros or 2% of an organization’s global turnover. |
| Supply Chain Security | Supply chain security is left largely to the discretion of individual organizations. | Mandates that organizations assess and manage risks throughout their supply chains. |
| Coordination and Cooperation | Focused on improving cybersecurity at the national level. | Establishes a European Cyber Crises Liaison Organization Network (EU-CyCLONe) to improve crisis management and response coordination across the EU. |
How to Know if You Need NIS2 Compliance
NIS2 is relevant for a wide range of companies across the EU. However, it applies primarily to industries deemed essential for society’s everyday functioning, such as:
- Energy (like electricity and gas)
- Transport (e.g., air and water)
- Banking
- Water supply
- Digital infrastructure (including cloud)
- Healthcare
Other important industries under the NIS2 umbrella include:
- The postal service
- Food sector
- Waste management
- Critical manufacturing (e.g., medicines and chemicals)
- Digital services (e.g., social media)
- Public safety-related research and development.
To determine if your clients need to comply, ask yourself the following questions:
- Do they provide essential services or critical infrastructure?
- Are they part of an essential digital supply chain?
- Are they operating in the EU or providing services to EU citizens?
If the answer is yes to all of these questions, then NIS2 is the way to go for cyber resilience and compliance.

What’s the impact of NIS2 compliance requirements on your business?
Complying with NIS2 offers several benefits for your clients beyond avoiding penalties.
- Increased Trust: Clients and partners are more likely to trust a business that adheres to strict cybersecurity standards.
- Competitive Advantage: Companies that are NIS2 compliant may have an edge over competitors who are not, especially when bidding for contracts.
- Resilience: NIS2 compliance ensures your clients are prepared to handle and recover from cyber incidents, minimizing downtime and financial losses.
- Regulatory Alignment: Compliance with NIS2 helps businesses align with other international cybersecurity regulations.
5 NIS2 Compliance Requirements You Need to Make a Priority
1. Management Accountability and Leadership Involvement
Unlike the previous NIS Directive, NIS2 explicitly holds company management accountable for cybersecurity compliance. Non-compliance could lead to personal liability for executives, including suspension from their duties.
Executives may be looking to outsource the responsibility of NIS2 compliance to an MSP/MSSP, but they remain liable for any negligence that results from non-compliance. Your job is to protect executives by ensuring their organization remains compliant.
Stakeholders need help understanding the significance of cybersecurity measures. Otherwise, they will be reluctant to assign the necessary resources. Frequent cyber security training for management is the only way to maintain a security-aware culture throughout an organization.
2. Comprehensive Risk Management Strategies
Article 21 of NIS2 mandates that organizations implement a comprehensive risk management strategy. Your strategy for clients must include technical, operational, and organizational measures to manage network and information systems risks.
Any risk management strategy starts with a risk assessment and concludes with a risk mitigation plan to maintain acceptable risk levels. Since you’re likely to perform many risk assessments, it’s best to develop a checklist you can use to gather information from your clients. Your checklist should be reviewed and updated periodically based on what worked best. Alternatively, you could use automated tools like Cynomi to perform risk assessments at scale and speed, saving you time and money.
3. Incident Reporting and Response Mechanisms
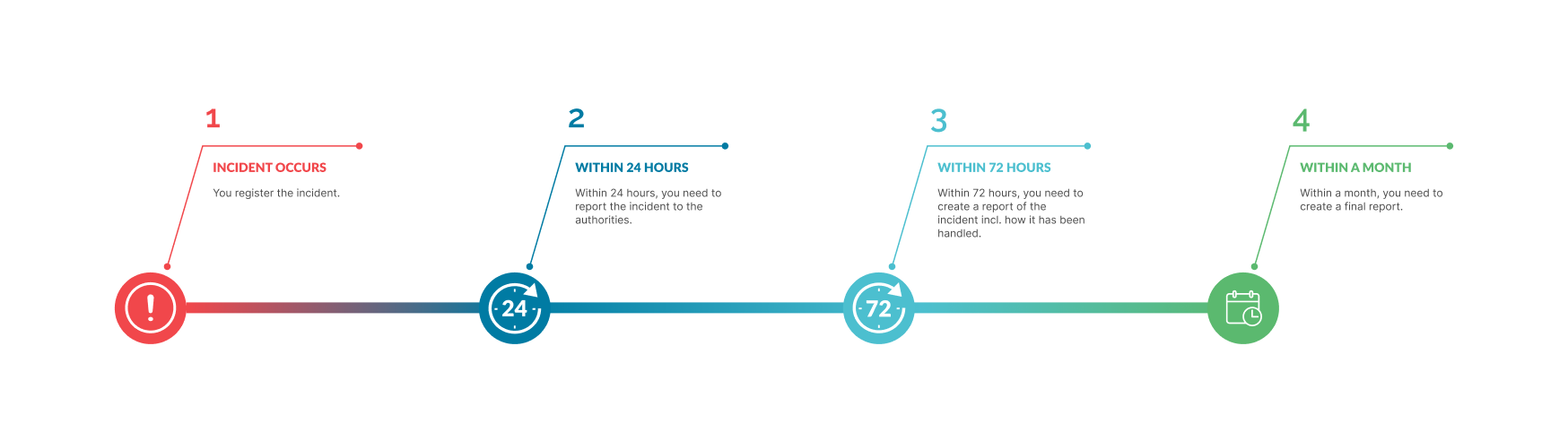
You must notify relevant authorities of significant cybersecurity incidents within 24 hours. NIS2 outlines a structured process for incident reporting, starting with an initial notification within 24 hours, an additional report within 72 hours, and finally, a complete report within a month:
- 24 Hours – The intention is to work with authorities to limit the spread of the incident.
- 72 Hours – With this report, ensure it outlines the probable cause, severity, and impact.
- 1 Month – Lastly, a detailed report of the incident, describing the type of threat, any damages to the organization, and a description of mitigation actions.
Plan and document your incident response plan and train relevant employees to execute it. You’ll likely have to participate in the later two stages of the report, but the client should prompt the initial notification and perform it as soon as possible.
Take advantage of automated tools to help generate detailed logs of your client’s assets, ensuring that you can provide authorities with comprehensive data about an incident should it occur.
4. Supply Chain Security Management
Software supply chain may be the biggest threat to your client’s compliance. With over 90% of organizations using cloud services, every one of your clients is potentially vulnerable.
When selecting cloud service providers, performing due diligence and investigating compliance with those services is crucial. Take care to enforce two-factor authentication, password rotation, and account expiration, or use a single-sign-on service.
Employees can sign up for cloud services without informing anyone; this is shadow IT. Cyber security training is the only way to combat shadow IT, so schedule periodic seminars to raise awareness and protect your clients.
5. Regular Cybersecurity Training and Awareness Programs
Cybersecurity training and awareness across all levels of an organization are critical aspects of NIS2 compliance. Human error remains one of the leading causes of cybersecurity breaches. You can mitigate shadow IT, phishing, malware, exposed passwords, and weak security protocols by informing clients of the dangers and how to spot them.
Encourage your client to foster a culture of cybersecurity awareness where employees feel empowered to report potential threats. Therefore, they can implement regular cybersecurity training programs tailored to different roles within their organization. These programs should cover essential topics such as phishing prevention, secure password practices, recognizing suspicious activity, and bring-your-own-device policies.
Navigating NIS2 Compliance with Cynomi
As MSPs and MSSPs, you are tasked with ensuring clients comply with NIS2 and stay ahead of the curve in the ever-changing compliance landscape. Having the right tools is essential for efficiency and completeness, which is where Cynomi steps in.
Cynomi’s vCISO platform automates the manual, time-consuming work of compliance assessments, enabling MSPs/MSSps to offer comprehensive compliance assessments for multiple frameworks. Cynomi provides AI-generated policies and strategic remediation plans with prioritized tasks, making it easier for every client to close compliance gaps.
Ready to simplify NIS2 compliance? Request a demo and see how you can streamline your compliance efforts while focusing on what matters most—protecting your clients.