
Few take cybersecurity as seriously as the United States Department of Defense (DoD), especially in 2025. While most organizations are exposed to various cyber threats, state-sponsored attackers target the suppliers and providers in the American defense supply chain.
For cybersecurity service providers, this presents both a challenge and an opportunity. This fact is especially true considering the DoD’s hefty annual budget, which has grown from $700 billion to $850 billion in the past three years. That’s a lot of income for thousands of contractors and subcontractors who will need to align their cybersecurity strategies with the DoD’s requirements —a standard known as the CMMC. The optimal way to achieve compliance is using a CMMC compliance checklist.
What is CMMC, and what should MSPs and MSSPs know about it?
The Cybersecurity Maturity Model Certification (CMMC) is a formal certification that applies to all US Department of Defense (DoD) contractors and subcontractors in the defense supply chain. These vendors are referred to as the defense industrial base (DIB), including private sector institutions, partners, vendors, contractors, subcontractors, and individuals that access and handle Federal Contract Information (FCI) and Controlled Unclassified Information (CUI).
The CMMC model aids stakeholders in assessing the compliance of the IT systems of service providers (DIB) with relevant cybersecurity standards and best practices. While most organizations have some kind of cybersecurity policy that adheres to data privacy regulations and cybersecurity industry standards, the CMMC requires contractors (and the service providers in their supply chain) to re-classify the defense contract data they store or process according to the CMMC standard.
The rule for CMMC 2.0 compliance (CFR 32) will come into effect on October 1st, 2026, for all MSPs, MSSPs, and all other contractors in the DoD supply chain. While this seems like a distant deadline, CISOS must begin the certification process sooner rather than later to ensure they can implement all the necessary cybersecurity controls and policies to comply with CMMC.
CMMC Compliance Levels
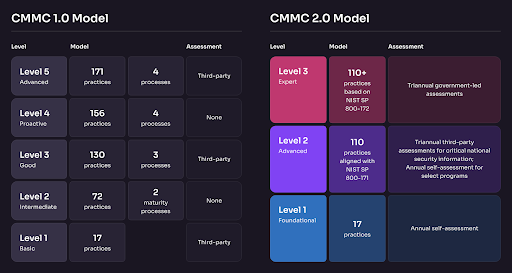
The CMMC is a tiered model, with each level including different requirements according to the type of sensitive information the subcontractor handles. Complying with different maturity levels also costs different amounts of money and affects the length and complexity of the certification process.
Level 1: Basic Safeguarding of FCI
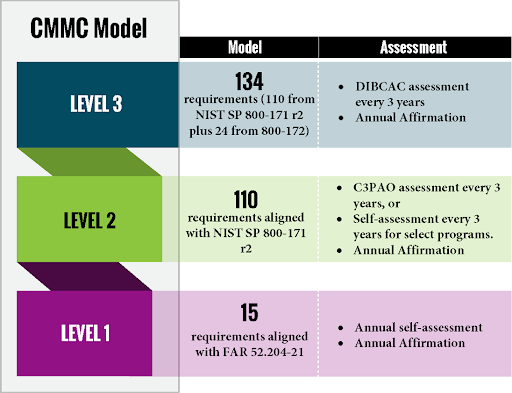
The most basic level of CMMC applies to organizations that only handle Federal Contract Information (FCI) and is aligned with the 15 cybersecurity requirements in the Federal Acquisition Regulation (FAR) 52.204-21.
This level entails meeting foundational cybersecurity practices like strong passwords, access management policies, etc. Companies looking to comply with CMMC Level 1 will be required to perform annual self-assessments for compliance verification.
Level 2: Broad Protection of CUI
The second level of the CMMC applies to organizations that handle Controlled Unclassified Information (CUI) and involves meeting the 110 security controls outlined in NIST SP 800-171.
CMMC Level 2 compliance demands more robust and advanced cybersecurity policies. It focuses on enhancing cybersecurity practices like incident response planning, secure software development practices, and automatic data encryption.
Depending on the type of information processed, transmitted, or stored on the contractor or subcontractor information systems, compliance with this level of the CMMC may require the company to undergo a third-party assessment every three years by accredited CMMC Third Party Assessment Organizations (C3PAOs). Organizations may sometimes be allowed to submit a self-assessment instead, depending on their contract.
Level 3: Higher-Level Protection of CUI Against Advanced Persistent Threats
The highest CMMC level is designed for corporations that handle CUI and are at risk of being targeted by Advanced Persistent Threats (APTs), which include state-sponsored attackers targeting critical defense supply channels.
To comply with CMMC Level 3, organizations first achieve a full Level 2 status. Then, you can add 24 additional and enhanced security controls from NIST SP 800-172. This process usually means integrating advanced tactics to strengthen cybersecurity postures, such as monitoring, pen testing, and others.
Organizations seeking Level 3 CMMC compliance must undergo these assessments every three years by the Defense Contract Management Agency’s Defense Industrial Base Cybersecurity Assessment Center (DIBCAC). This requirement is different from the Level 2 triennial assessments, which C3PAOs carry out.
Your Link in The Supply Chain: The CMMC Compliance Mandate for MSPs and MSSPs
MSPs and MSSPs that provide digital services to the DIB become parts of the defense supply chain themselves the moment they handle CUI or FCI. If your clients are looking to comply with CMMC, your business must comply with the same (or higher) level of CMMC compliance.
That said, the CMMC compliance mandate also presents a lucrative opportunity for MSPs and MSSPs that can invest in accreditation as CMMC Registered Practitioner (RP) or Registered Provider Organization (RPO). With a relatively low entry cost (circa $5,500/year), achieving one of the higher levels of compliance for MSSPs, or even becoming C3PAOs, can open a wealth of new business opportunities.
The Essential CMMC Compliance Checklist for CISOs
As per CMMC’s program rule, all businesses in the defense industrial base should take expedited action to gauge their compliance with existing security requirements and their preparedness to comply with CMMC assessments.
The essential CMMC compliance checklist we’ve prepared for CISOs and service providers is the basis for evaluating compliance preparedness with CMMC 2.0 Level 1. Based on the FAR 52.204-21 standard and the DoD CMMC assessment guide, the checklist addresses 15 requirements under six domains. It can be used in the mandatory annual self-assessment and executive affirmation.
It is worth noting that, unlike Levels 2 and 3, CMMC 2.0 Level 1 compliance demands meeting all 15 requirements and does not offer the option to include roadmaps or plans to implement the necessary security controls. The requirements allow organizations and their MSPs/MSSPs plenty of flexibility in implementing the controls.
Without further ado, let’s dive into the checklist.
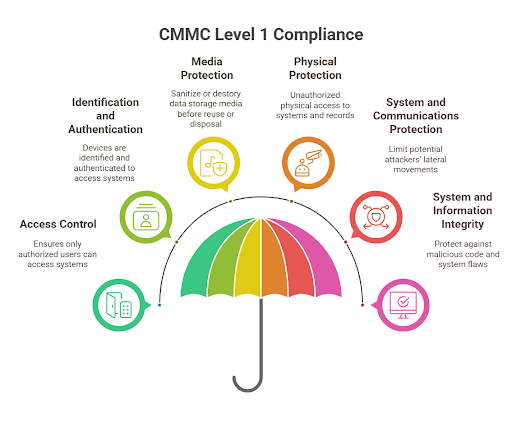
Access Control (AC)
The first domain of the CMMC cybersecurity compliance framework deals with who gets access to company information systems. It broadly defines what organizations should do to meet the criteria in three checklist items.
- Limit information system access to authorized users, processes acting on behalf of authorized users, or devices (including other information systems).
- Verify and control/limit connections to and use of external information systems.
- Control information posted or processed on publicly accessible information systems.
To meet the requirements, an organization can employ an Identity Access Management (IAM) system to manage all the users, processes, and devices that are allowed access to company systems. Ideally, the organization will implement a role-based access control (RBAC) scheme for all its systems, with least privilege principles enforced throughout the account lifetime.
Identification and Authentication (IA)
The second domain of the framework is tightly related to the first and focuses on ensuring that users, processes, and devices are identified and authenticated to access company information systems.
- Identify information system users, processes acting on behalf of users, or devices.
- Authenticate (or verify) the identities of those users, processes, or devices as a prerequisite to allowing access to information systems.
A best practice is to deploy IAM systems or centralized authentication services to ensure accounts are managed securely and are only accessible to their authorized users.
Media Protection (MP)
The media protection requirement means organizations must destroy or otherwise purge FCI from any kind of data storage media (from papers to servers) before reuse or disposal.
- Sanitize or destroy information system media containing Federal Contract Information before disposal or release for reuse.
Physical Protection (PE)
The next domain pertains to unauthorized individuals’ physical access to organizational information systems. It outlines the actions businesses should take to minimize the risk of unauthorized access to FCI records.
- Limit authorized individuals’ physical access to information systems, equipment, and the respective operating environments.
- Escort visitors and monitor visitor activity; maintain audit logs of physical access; and control and manage physical access devices.

System and Communications Protection (SC)
This domain directs CISOs to implement communication monitoring, logging, and separation of networks and system components, whether physically or virtually, to limit potential attackers’ lateral movement.
- Monitor, control, and protect communications (i.e., information transmitted or received by information systems) at the external and key internal boundaries of the information systems.
- Implement subnetworks for publicly accessible system components that are physically or logically separated from internal networks.
System and Information Integrity (SI)
Last but not least is the domain of integrity and prevention. The four requirements in this domain demand that organizations take proactive steps to ensure their information systems are safe from malicious code and potential system flaws.
- Identify, report, and correct information and information system flaws in a timely manner.
- Protect against malicious code at appropriate locations within information systems.
- Update malicious code protection mechanisms when new releases are available.
- Perform periodic scans of the information system and real-time scans of files from external sources as files are downloaded, opened, or executed.
Streamline CMMC Compliance With Cynomi’s vCISO Platform
The CMMC certification required for contractors and subcontractors in the American defense sector is necessary for anyone involved in the DoD supply chain. Our checklist includes items for the foundational level of the certification. Higher certification levels are much more costly (circa $100,000, excluding any additional investments needed to meet the standard requirements) and more complicated to conduct.
Regardless of the CMMC compliance process’s level or scope, Cynomi’s vCISO platform automates the painstakingly long stages of information gathering and streamlines CMMC compliance assessments at scale. Cynomi automates compliance assessments for multiple frameworks and delivers automatically generated tailored policies and strategic remediation plans.
MSPs/MSSPs can use Cynomi to eliminate the planning hassle and stand out in the competitive market without needing to develop in-house expertise or scale existing resources.
To learn more about Cynomi, request a demo today.