![The Definitive Cyber Security Policy Template [XLS Download]](https://cynomi.com/wp-content/uploads/2024/12/The-Definitive-Cyber-Security-Policy-Template-XLS-Download-1-768x366.png)
Aside from information security professionals and techy teams, few people actually think about cyber security while doing their jobs. Other departments may not share the enthusiasm to prioritize security, so clients sometimes struggle to close the iron gates and keep cyber threats at bay.
53% of employees are worried about their organization suffering a cyber attack, and over 34% admit their shortcomings could expose their employer to a data breach. MSPs/MSSPs have a responsibility to guide clients on where these gaps lie, and a great way to do so is by formalizing security requirements in a standardized cyber security policy template for each client.
What is a cyber security policy template, and what is it used for?
A cyber security policy template is a document that provides a comprehensive set of guidelines and procedures that MSPs/MSSPs can use to help their clients minimize cyber risk and protect digital assets from threats and vulnerabilities. MSPs and MSSPs often employ templates as the base for various and versatile client-specific cyber security policies.
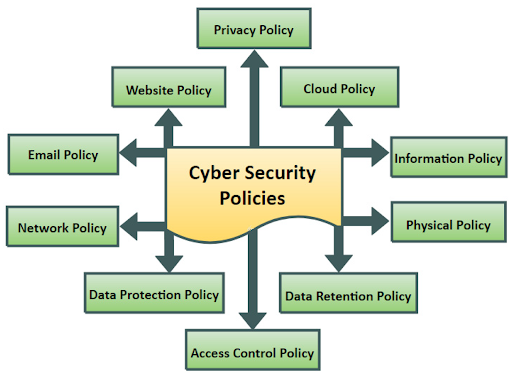
Types of Cyber Security Policies to Know
MSPs/MSSPs can implement many types of cyber security policies for clients. Here are a few examples.
- Acceptable use policy guides employees, partners, and third-party service providers in using the organization’s systems and devices without exposing them to cyber risk.
- Password security policy sets the requirements for passwords used in organizational systems and usually includes strength and complexity demands and the frequency of mandatory password changes.
- Email security policy outlines the acceptable use of corporate email systems to minimize the risks stemming from corporate email misuse or compromise.
- Access control policy defines the guidelines and rules for user and machine access to various digital assets and resources. It includes the processes for creating accounts, RBAC enforcement, network access controls, remote access, and account lock-out.
- Data protection policy guides employees in handling sensitive information like PIIs, financial data, and proprietary business information.
3 Reasons Why You Need a Cyber Security Policy Template
There are plenty of reasons why MSPs/MSSPs can benefit from a cyber security policy template.
- Save time when creating cyber security policies for clients. Instead of creating a cyber security policy from scratch for every new client, MSPs/MSSPs frequently employ customizable templates to quickly produce comprehensive cyber security policies at scale for different clients with varying needs.
- Adhere to standards and comply with regulations. A comprehensive and extensive template covers all the relevant areas of cyber security and data protection, ensuring that no aspect is overlooked or neglected when creating the cyber security policy for the specific client.
- Enhance communication between MSPs/MSSPs and clients. A cyber security policy template can help facilitate a clearer exchange of expertise between the MSP/MSSP and the client’s risk and InfoSec teams by providing a common language and unifying the methods of operation between in-house and outsourced experts.
The Definitive Cyber Security Policy Template
It’s best to divide the cyber security policy template into sections. Suppose you’re designing your policy to adhere to a certain cyber security framework (such as NIST or ISO 27001:2023). In that case, the list of sections may differ, so be sure to refer to the framework documentation to adjust your templates as needed.
Risk Assessment
Before creating a cyber security policy template, you can conduct a risk assessment and base the policy on the results. The process of assessing and quantifying cyber risk in organizations can differ in complexity and scope, and the level of detail you may wish to include in this section will depend highly on the cyber security framework employed by the client. There are various tasks that fall under the umbrella of a risk assessment:
- Asset identification entails cataloging and categorizing all the client’s information assets that are covered by the specific cyber security policy. These may include sensitive data stores, devices (from IoT sensors to on-prem servers), personnel, applications, and other assets requiring protection.
- Threat assessment is a multiphased process to identify, score, and prioritize the response to potential threats to the digital assets listed in the previous section.
- Vulnerability evaluation follows threat assessment to deliver a complete view of the client’s attack surface by analyzing weaknesses in their systems, like unpatched software, inadequate password policies, and even phishing attacks.
- Business impact analysis requires estimating the potential impact of each loss in monetary terms, accounting for reputational damage, operational disruption, and non-compliance fines.
- Risk management and mitigation include security controls, employee training, enhanced monitoring, and the purchase of additional cyber security tools and services.
Summary & Scope
The first section of your document should include an executive summary describing the policy’s content and defining its scope. This section also lists the individuals and organizations to which the policy applies, such as employees, third-party vendors, and contractors who may have privileged access to the client’s systems.
Policy Statement
This section is not mandatory, but it helps align cyber security goals and objectives across teams in the organization. Generally speaking, it can serve as a list of commitments and standards the client needs to uphold. These can include:
- Choosing and implementing an adequate cyber security framework to ensure and maintain the confidentiality, integrity, and availability of all organization information assets.
- Conducting regular cyber risk assessments and implementing adequate controls to mitigate identified risks.
- Integrate cyber security throughout all business processes and operations, including ongoing training and support for all relevant stakeholders.
- Performing regular reviews of the cyber security policy to address changes in the business and keep up with emerging threat detection and prevention best practices.
Roles and Stakeholders
For a cyber security policy template to be effective, it’s critical that everyone involved knows what to do and what their responsibilities are. This section outlines an exhaustive list of team members, consultants, executive decision-makers, and service providers relevant to the policy. Include functional responsibilities, duty separation detailing, or a table with contact information, authority, access rights, etc.
Policy 1: Access Management and Controls
You can include any specific policies in the cyber security policy template depending on the client’s requirements and goals. Some policies include password security, cloud security, and vulnerability management; in this template, we have chosen three example policies that you can use. The first is access management and controls:
- Authentication systems and controls that employ identity confirmation with password and biometric identification, including MFA and risk-based authentication.
- Authorization processes adhere to the least privilege principle and ensure users and machine accounts only access the data necessary to perform their tasks.
- Documentation, logging, and auditing to maintain records of access to sensitive data, failed login attempts, and when monitoring for suspicious activity. It is also vital for compliance audits and to provide forensic evidence when investigating a breach.
- Password security policies include password complexity requirements, reuse limitations, regular changes, and the client’s password management tools or passwordless solutions.
- Session security protects active user sessions and tokens from unauthorized access. This set of policies includes session timeouts, session monitoring, risk-based session termination, and other controls.
Policy 2: Incident Response
The second example policy we’ve chosen is incident response. Cyber incidents can happen regardless of how robust and comprehensive a client’s cyber security policy is.
Typically, MSPs/MSSPs support clients by creating an incident response policy based on existing standards (such as the NIST cyber incident response standard). This section should include:
- Incident preparation and readiness steps to establish an incident response team, dividing responsibilities and tasks, and providing relevant staff with the necessary training, tools, and resources.
- Detection and evaluation entails using tools and services to promptly detect and be alerted of security incidents, along with detailed and contextual information that helps gauge the scope and impact of the incident as it unfolds.
- Communications by listing alternative channels and methods of communication for the incident response teams and other relevant stakeholders.
- Post-mortem incident analysis to apply the lessons learned to response and mitigation strategies.
Policy 3: Backup and Disaster Recovery
Backup and disaster recovery is the third example policy we’ve chosen, and it is best planned as a separate section to incident response. The guidelines to include in this section of the cyber security policy template include:
- Backup procedures, including what systems and data stores the client should back up and how frequently, how they should be stored, and the length of time old backups should be kept and updated.
- A disaster recovery plan that describes the processes for restoring systems and data after a disruption, maintaining business operations during recovery, and prioritizing resource allocation for minimal impact on operations.
- A business continuity plan should include steps, tools, and contacts essential for the organization to continue normal operations during and after a disaster.
Regulatory Compliance
While not strictly necessary for a cyber security policy template, it’s a good best practice to include regulatory compliance. This section usually encompasses:
- Relevant compliance requirements (both mandatory and optional) for the client may include GDPR, PCI-DSS, HIPAA, NIST, SOC 2, etc.
- Security controls that the client must implement to meet regulations, such as access controls, data protection measures, data storage and processing conditions, etc.
- Documentation, plus guidelines for creating, maintaining, and updating the documentation of all activities and efforts to ensure ongoing compliance. These may include lists of policies, procedures, audit scores, and proof of adherence in the form of compliance reports.
- Auditing and reporting that identifies gaps in compliance.
Automating Cyber Security Policies at Scale With Cynomi
An effective cyber security policy template can help save time and money and speed up the process of creating a cyber security policy from weeks to days. However, with Cynomi’s vCISO platform, you can accelerate the process even further by automating the generation of a custom-tailored cyber security policy in minutes.
Cynomi automates manual and time-consuming cybersecurity management work, including asset discovery and risk assessment processes, by providing guided questionnaires and express scans to help uncover critical vulnerabilities and compile a comprehensive cyber security policy based on each client’s unique cyber risk profile.
Book a demo today to streamline and automate cyber security policies at scale with Cynomi.