
It’s 2 a.m., and you receive a dreaded email about an unfolding cybersecurity incident causing chaos for one of your clients. Security alerts often pierce the silence of the night because threat actors don’t stick to a 9-5 schedule.
The scenarios that trigger a formal incident response process are diverse, including data breaches, detecting ransomware and other malware, or denial of service (DoS) attacks. Though stressful and demanding, such scenarios are day-to-day realities in the world of cybersecurity (and you probably wouldn’t work in the industry if you didn’t thrive under these high-pressure situations, right?).
However, with companies taking an average of 69 days to contain a breach, something is clearly wrong with incident response (IR) across the board. Swift action, coordination, and clarity start with a dedicated incident response tools policy.
What is an incident response policy template?
An incident response policy template outlines procedures and responsibilities in the event of a cybersecurity incident to ensure consistency and effectiveness in handling those incidents. It’s all about what tasks the response team should do and who should do those tasks in the event of a cybersecurity incident. This type of framework usually comes as a comprehensive checklist or a spreadsheet.
The main benefit is that it provides a basic structure for building a more customized policy. You can customize the document based on specific needs, like regulatory requirements or your client’s risk profile. The people who action the document include anyone involved in incident response, whether that’s a SOC team, senior leadership, a dedicated IR team, or public relations.
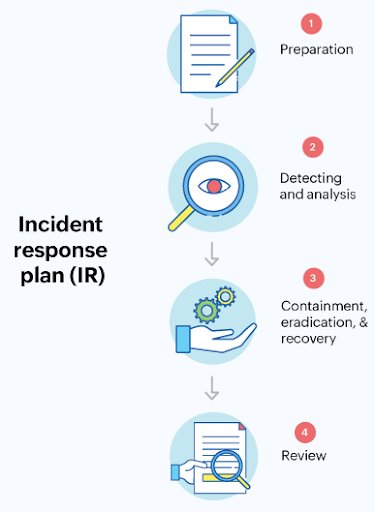
3 Examples of Incident Response Frameworks
Incident response frameworks are collections of best practices on which MSPs can base incident response policies (and plans). Here are three examples to consider if you’re making a policy or policy template.
1. NIST CSF
The NIST Cybersecurity Framework (CSF) is a set of guidelines and best practices developed by the U.S. National Institute of Standards and Technology (NIST). NIST CSF helps companies of all sizes design, implement, and manage an effective incident response strategy tailored to their risk profile. It consists of three main components:
- Framework Core: A set of cybersecurity activities, outcomes, and references organized into five functions: Identify, Protect, Detect, Respond, and Recover.
- Framework Implementation Tiers: A set of levels that describe the degree to which an organization’s cybersecurity practices align with the CSF.
- Framework Profiles: Snapshots of an organization’s current cybersecurity posture and target state, which can be used to prioritize improvement efforts.
2. SANS Institute
The SANS Institute offers a detailed Incident Response cheat sheet and process that InfoSec professionals widely use. This framework is structured around six phases:
- Preparation: To establish a foundation for incident response before an incident occurs.
- Identification: To detect and recognize signs of a potential security incident.
- Containment: To limit the spread and damage of an incident.
- Eradication: To remove the incident’s root cause and eliminate any remaining threats.
- Recovery: To restore affected systems and services to normal operation.
- Lessons Learned: Analyzing the incident, identifying areas for improvement, and updating incident response plans.
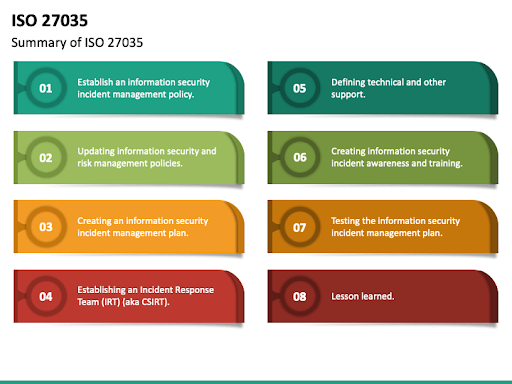
3. ISO/IEC 27035
ISO/IEC 27035 is an international standard for incident management that provides a structured and planned approach to detecting, reporting, and assessing information security incidents. It outlines principles for incident management, including establishing an incident response team, implementing an incident management policy, and following processes throughout the incident life cycle.
Why You Need an Incident Response Policy Template
Standardization and Consistency
An incident response or risk assessment template helps maintain consistency in how relevant personnel manages cybersecurity incidents, regardless of when or where they happen.
Faster Response Times
With a template in place, you can quickly deploy a well-organized response to clients’ security incidents. This reduces the time it takes to address and contain threats, which can limit an incident’s impact and severity.
Improved Coordination and Communication
Cybersecurity incidents can feel like your clients are being thrown into chaos. Still, a policy template provides a level of organization by designating protocols and channels to ensure smooth communication. Also, you and your clients benefit from much-improved coordination by defining incident escalation paths, thresholds, roles, and responsibilities.
The Easy-to-use Incident Response Policy Template
It’s worth splitting the template into different phases of the incident response cycle: preparation, detection, response, recovery, and prevention.
Preparation Phase
1. Purpose and objective
Think about what you are aiming to protect within your client’s organization. This stage states the main goals of the incident response policy and establishes a clear direction on what the policy aims to achieve. By setting the tone and direction, you can better align every incident response requirement with broader security outcomes. Make this clear and engaging and ensure the objectives resonate with everyone involved in incident response.
2. Scope
The policy must cover all bases – systems, networks, data, and personnel. There’s no room for gray areas or ambiguities here, which is why it is essential to define who and what is included under the umbrella of this policy. Also, update this section often to reflect any changes in your client’s operational environment, perceived threat severity, or asset inventory. A dynamic risk assessment can be a helpful and complementary tool when it comes to deciding policy updates.
3. Roles and responsibilities
From the Incident Response Manager to the newest intern – define who does what, when, and how. Clarity reduces chaos. Everyone knowing their role reduces confusion and speeds up the response time. You can use diagrams or charts to provide clients with easy reference points and keep these descriptions as straightforward as possible.
Detection Phase
4. Definitions
What exactly constitutes an ‘incident’? Define key terms to ensure everyone in your MSP and your client’s organization speaks the same language. Consistency in terminology leads to more effective communication and better incident handling. In this stage, the industry frameworks discussed above can be useful guidelines, plus threat detection and response best practices.
5. Reporting procedures
How should incidents be reported? Whether it’s a dedicated hotline or a digital form, make it clear and accessible for every client. Quick and accurate incident reporting can differentiate between a minor issue and a costly catastrophe. The key here is simplicity: Ensure communication doesn’t hinder the response.
Response Phase
6. Response actions
A streamlined, predefined general action plan is your best defense against escalating threats. Remember that this is an incident response policy template rather than a dedicated step-by-step incident response plan, so you don’t need to go too in-depth (that’s what the plan is for). At this stage, you may decide to invest in business continuity and disaster recovery tools, or other MSP software solutions, to automate as much of the recovery process as possible.
7. Automated incident response
You can implement an automated incident response tool, such as an Endpoint Detection and Response (EDR), that will respond to an attack and contain it. A best practice is establishing a threshold for alerts when an incident is detected and classified so you know there are no false alarms.
Recovery Phase
8. Communication plan
Incident response communication means reporting security events through the appropriate management channels, both internally and externally. Communication is just as important in the recovery phase as during the initial response – except that here, it becomes a concern beyond those involved in the actual response.
In recovery, communication is all about defining who to update, what to say, and when to say it. It isn’t just for your team – it’s also for client stakeholders and possibly the public. Pre-drafted messages and designated spokesperson training will streamline this process and prevent miscommunication.
Prevention and Post-Incident Review Phase
9. Review and improvement
After an incident:
- Take a deep dive into what happened and why. The template should include a review process that kicks in after neutralizing the immediate threat.
- Set out a few questions to answer about each incident, such as what its root cause was, how well the communication plan functioned, and what could’ve been improved.
- List some security metrics to capture after each incident, such as response time, downtime incurred, the number of systems impacted, or financial loss.
- Review and update policies regularly to keep them relevant to your changing security posture.
Provide Automated and Customizable Policies With Cynomi
An incident response policy template is an excellent starting point for streamlining and improving your IR process. However, despite their framework-esque approach, templates need much work, regular updates, and customization to create and remain effective. They become particularly challenging in an MSP/MSSP context when you have multiple clients to juggle and limited internal resources.
With Cynomi, you can bypass the lengthy process of crafting and updating IR policies manually. The platform generates a customized incident response policy for clients at onboarding, provides ongoing performance assessments, and integrates actionable tasks directly linked to the policy. Cynomi will demonstrate your clients’ policy progress and provide scoring you can monitor over time. You can access the Cynomi IR policy in one click, connect tasks assigned to individuals, and edit it.
Request a demo today to see how Cynomi can help you enhance and scale your service offerings.