![The Essential Information Security Policy Template [XLS Download]](https://cynomi.com/wp-content/uploads/2024/12/The-Essential-Information-Security-Policy-Template-XLS-Download-1-1-768x366.png)
Juggling cybersecurity for multiple clients is an uphill climb for MSPs and MSSPs. Each client has their own vulnerabilities, compliance pressures, and risks. But by creating an effective information security policy (ISP) template, you gain a consistent starting point to deliver tailored solutions without reinventing the wheel every time.
The risks are growing every year. IBM reports the average total cost of a data breach hit $4.45 million in 2023, and healthcare breaches cost even more—an eye-watering $10.93 million on average. MSPs/MSSPs can step in with solutions that keep your clients out of those statistics. With the right template, you can help clients shore up their defenses and prove your value as their trusted security partner while reducing your team’s time on repetitive tasks.
What is an information security policy template used for?
An information security policy (ISP) template is more than a starting point; it’s the foundation for creating effective, client-specific policies. The ISP lays out the protocols and processes needed to protect sensitive information, systems, and networks from internal missteps and external threats.
An information security policy template aims to help your clients establish clarity and consistency in their security practices. By leveraging a proven framework, you can ensure clients address key risks, meet regulatory requirements, and build a security-conscious culture. Templates also allow you to standardize processes across diverse client portfolios, saving time while maintaining quality.
While every business can benefit, templates are especially useful for SMBs, which often lack the in-house expertise to develop effective policies, and for industries like healthcare, finance, and technology, where compliance is under constant pressure.
Reasons Why You Need an Information Security Policy Template
Creating tailored security policies for every client doesn’t have to feel like reinventing the wheel every time. ISP templates offer a smarter way to deliver consistent, high-quality policies while streamlining your workflow:
- Save Time While Staying Consistent: Starting from scratch for every client? It’s not sustainable. A template gives you a solid framework to quickly build tailored policies without sacrificing quality or consistency.
- Simplify Compliance: Compliance is critical and complicated from GDPR to NIST 800-53 and ISO 27001. Templates bake in regulatory best practices, making it easier for you to align policies with client requirements, reduce audit stress, and avoid costly penalties.
- Reduce Security Risks: An ISP template addresses common vulnerabilities, such as unpatched systems, phishing threats, or weak access controls. By building these safeguards into a client’s security framework, you reduce their risk exposure while reinforcing a proactive security posture.
- Build Trust and Credibility with Clients: Delivering professional, tailored policies shows clients you’re serious about their security. It’s a simple but effective way to deepen trust, strengthen relationships, and open the door for expanded service offerings.
The Essential Information Security Policy Template
Developing a robust information security policy template requires careful attention to several key components. Here are the critical sections your template should include.
1. Purpose and Scope
This section sets the foundation for the policy by defining its objectives and the areas it covers. It answers two critical questions: why the policy exists and what it applies to. Policies can become ambiguous without a clear purpose and scope, leaving security gaps that attackers can exploit.
Top Tips
- Use asset discovery tools to list all systems and data sources in the client’s IT environment. Add specific details to give context. For example, laptops with access to financial systems must use full-disk encryption.
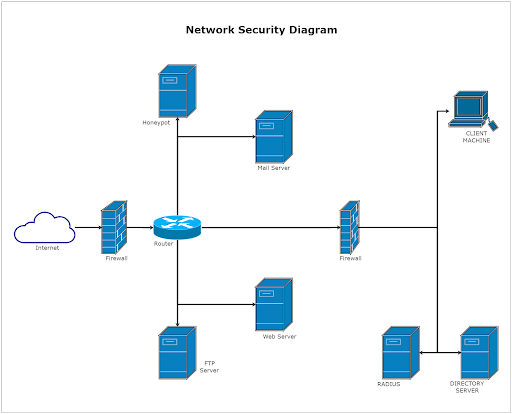
- Add a network diagram (see the image below) or flowchart to clarify what’s in scope. Highlight areas like cloud resources, third-party integrations, and remote devices.
- Use client-specific language to make the policy feel tailored rather than generic.
- Be explicit about what the policy does not cover.
2. Roles and Responsibilities
If no one knows who’s accountable, security tasks can get overlooked. This section defines exactly who’s responsible for each security task, from managing systems to responding to incidents. Clear roles mean no overlap, confusion, or excuses when something goes wrong.
Top Tips
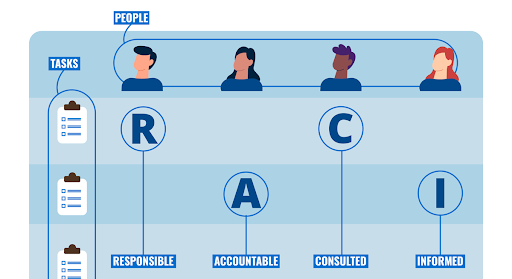
- Use a RACI Matrix (Responsible, Accountable, Consulted, Informed) to map every security task to the right role. For example, the IT team is Responsible for applying patches, the CISO is Accountable, and leadership is Informed once it’s done.
- Build a checklist of must-haves for third parties and add these requirements into vendor contracts to avoid future headaches. It might include secure file transfers (SFTP or encrypted alternatives) and minimum patch frequency.
3. Key Security Policy Statements
Compliance and Auditing
A compliance and auditing policy specifies the discovery, development, proactive management, and ongoing governance of your client’s cybersecurity program. It applies to all assets, business processes, and functions within the organization.
Cloud Security
A cloud security policy establishes security requirements and controls for managing and accessing cloud services and protecting your client’s data and assets. It provides clear guidance to stakeholders about their responsibilities and applies to all employees, contractors, and third-party users.
Business Continuity
A business continuity plan provides guidance, tools, and procedures that allow clients to survive a disaster and re-establish normal business operations. This policy outlines a baseline disaster recovery plan that describes the process of safely recovering IT systems, applications, and data.
Vulnerability Management
MSPs/MSSPs can conduct vulnerability and risk assessments by scanning the client’s network and creating a list of identified vulnerabilities with recommendations for mitigating them. You can use an external scanner like Cynomi’s. A vulnerability assessment includes a scan of the company network and assets, a gap analysis, risk prioritization, and a remediation roadmap.
Incident Response
The purpose of an incident response policy is to clearly define roles, responsibilities, actions, and procedures for responding to and investigating security incidents and data breaches. It applies to all the client’s assets and employees.
4. Access Controls
While some policies, like social media usage or remote work guidelines, might vary depending on the client’s preferences, access control is foundational. Without it, your clients risk insider threats, accidental data leaks, or hackers gaining unauthorized access. Include this in the template to guarantee a clear framework for granting, managing, and monitoring access to systems, networks, and data.
Top Tips
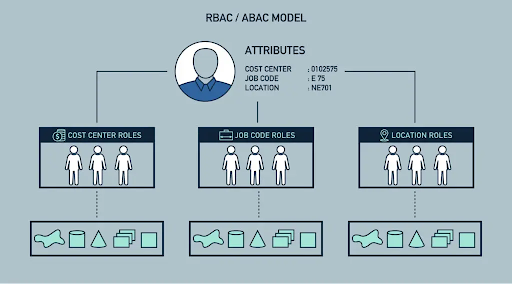
- A step-by-step process for setting up Role-Based Access Control (RBAC) that aligns access permissions with job functions. For instance, HR staff need access to payroll systems but not code repositories.
- Implementing Multi-Factor Authentication (MFA) for all critical systems. Recommend tools or hardware tokens for enhanced protection.
- Conducting quarterly access audits to remove outdated permissions and detect “privilege creep.”
5. Enforcement
You want this section to clearly outline how policies are enforced, compliance is monitored, violations are handled, and steps are taken to address repeat offenders. However, to maintain trust among employees and clients, make sure the enforcement guidelines are fair, transparent, and consistent.
Top Tips
- Highlight potential liabilities for breaches caused by negligence.
- Specify how compliance is tracked through automated tools like SIEM platforms or regular audits.
- Be specific about what happens when the rules aren’t followed. Minor infractions, such as repeated login failures, could result in mandatory retraining. Serious violations, like unauthorized access to restricted data, might warrant an immediate suspension of access and a formal investigation.
- Include escalation steps for recurring violations, such as notifying leadership or requiring additional security measures for offenders.
6. Policy Review and Updates
A template that isn’t reviewed regularly quickly becomes outdated. You want your clients to stay equipped to update their policies to address new threats, technologies, and compliance changes. For MSPs and MSSPs, this section provides the structure to keep policies relevant and actionable over time.
Top Tips
- Specify a review cadence and details of who is responsible for approving updates. It can be tied to major changes in the client’s infrastructure, like adding a new SaaS tool or adopting a hybrid cloud setup.
- Include guidance on who should approve updates, such as the CISO or a security steering committee, and how those approvals are documented.
- Provide a section to track changes, with details like version numbers, update dates, and the rationale for modifications.
Moving Beyond Templates with Smarter Security from Cynomi
An information security policy template is the bridge between consistency and customization in an increasingly complex threat landscape. It provides the foundation for tackling client challenges like compliance pressures, evolving risks, and operational inefficiencies. But a static template can only take you so far. The true value lies in your ability to adapt policies to each client’s specific risks and requirements.
Cynomi makes managing client security easier, smarter, and faster for MSPs and MSSPs. Its automated vCISO platform handles audits, risk assessments, and policy creation in a fraction of the time and cost it would take for an employee. Cynomi offers more than just automation—it is also precise. The platform uses AI built on expertise from top CISOs to craft policies specific to each client’s risks, compliance needs, and operations. Instead of relying on cookie-cutter templates, you get policies that feel like they were written just for them.
See how Cynomi’s automation can elevate your security services by scheduling your demo today.