
Cybersecurity compliance isn’t just a set of rules—it’s a moving target that keeps changing just when you think you’re catching up. Frameworks like NIST 800-171 may seem like an overwhelming addition to your existing compliance repertoire, but they’re crucial. One misstep can lead to millions in damages, lost contracts, or even legal trouble.
By 2025, cybercrime damages are expected to hit $10.5 trillion. That’s not just a number—it’s our reality. Ignoring compliance today isn’t just risky; it’s like leaving the door wide open for financial catastrophe. In the U.S., the average cost of a data breach stands at $9.36 million, making it the most expensive country to suffer a breach.
MSPs/MSSPs are constantly working to keep clients secure. Understanding the mysteries and intricacies of NIST 800-171 compliance is essential so you can confidently guide your clients through this challenging process.
What is NIST 800-171 compliance, and what’s it for?
NIST 800-171 is the standard that defines how non-federal entities should protect Controlled Unclassified Information (CUI). It’s like the rulebook on keeping sensitive government-related data safe when it’s being handled outside the government.
NIST 800-171 isn’t just for your big-time defense clients either. Small to medium businesses, subcontractors, and anyone in a supply chain handling CUI (think about all those companies dealing with government contracts) have a seat at this table.
While compliance is ultimately the responsibility of businesses, MSPs/MSSPs possess the specialized knowledge of security controls and best practices needed for NIST 800-171 compliance, putting you in a unique position to guide clients through the complexities of the framework. Compliance with NIST 800-171 isn’t as simple as ticking a box—it’s about systematically helping your clients secure their environments to protect CUI.
What is Controlled Unclassified Information (CUI)?
Controlled Unclassified Information, or CUI, is sensitive data that isn’t quite top-secret but still demands a very high level of protection, such as:
- Health records
- Research and engineering data
- Process sheets and manuals
- Law enforcement records
It could include anything from blueprints to internal communications—basically, if the government doesn’t want it widely accessible but it’s also not classified, it’s CUI.
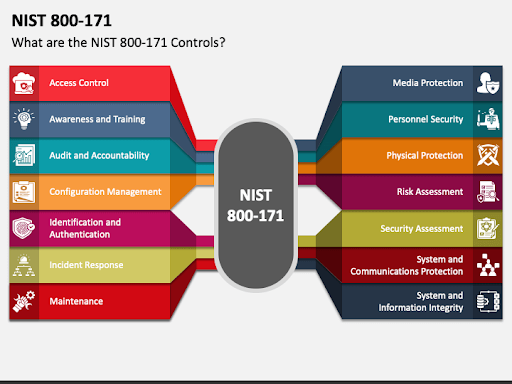
Top NIST 800-171 Requirements You Need to Know
Let’s dive into some of the top NIST 800-171 requirements MSPs/MSSPs should know about, and how you can describe them contextually to your clients.
1. Access Control (AC)
Your client needs to limit who has access to CUI in their organization. It sounds basic, but this control forms the foundation of security. It means defining roles, setting permissions, and ensuring that only those who need access get access.
2. Awareness and Training (AT)
Humans are the weakest link, right? This control is all about ensuring everyone—from the interns to the CEO—knows how to handle CUI properly. Regular training on phishing scams, best practices, and incident response can mean the difference between a small issue and a full-blown disaster for your clients.
3. Audit and Accountability (AU)
Audit logs are like your client’s network surveillance cameras, tracking who accessed what, when, and for how long. Like a good detective story, these logs help piece together what happens if something goes wrong.
4. Configuration Management (CM)
Configuration management means your clients should keep systems documented and secure. There should be no ad-hoc changes or one-off settings that someone decided were a good idea at the time—everything needs to be standardized and tracked. Controlled environments are secure environments.
5. Incident Response (IR)
Having an incident response plan means your client isn’t scrambling when things hit crisis mode. It means knowing what steps to take, who to inform, and how to minimize damage.
6. Media Protection (MP)
Sensitive information doesn’t just live in the cloud. It’s on USB drives, hard copies, and sometimes even handwritten notes. Media protection is about ensuring all these forms of CUI are protected and properly destroyed when no longer needed.
7. System and Communications Protection (SC)
This NIST 800-171 requirement is about ensuring that systems communicate securely. Encryption, secure protocols, and network segmentation all play a part in protecting information from falling into the wrong hands during transmission.
8. Physical Protection (PE)
Digital security is vital, but your clients can’t forget about physical security. If anyone can walk in and plug a device into their network, all their fancy cyber defenses become useless. Physical protection includes locked doors, restricted access areas, and proper visitor monitoring.
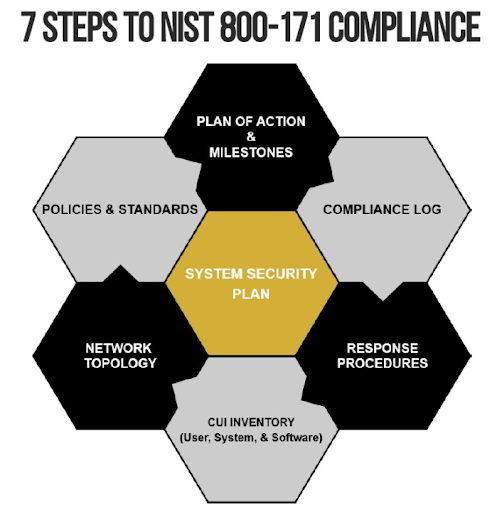
The Essential NIST 800-171 Compliance Checklist
1. Identify Your CUI
You can’t protect what you don’t know exists. Start by identifying every piece of CUI in your environment.
- Conduct a comprehensive data inventory to locate all CUI within your organization.
- Use data classification tools to tag and monitor CUI to ensure proper handling and protection throughout its lifecycle.
- Assign a dedicated team or individual responsible for maintaining an updated inventory of all CUI, ensuring constant tracking and safeguarding against unauthorized access.
2. Categorize and Prioritize Your Security Needs
Not all data is created equal. Categorize CUI based on sensitivity and prioritize protection for high-risk areas, which helps clients focus resources effectively.
- Classify CUI based on sensitivity, risk, and business impact to prioritize security measures effectively.
- Develop a matrix that identifies the most critical data assets and assign tiered security controls for each level.
- Conduct regular risk assessments to update the categorization as the nature of the data and threat landscape evolves.
3. Control Physical Access
Clients must protect the physical areas where CUI is stored or processed, which means keeping unauthorized personnel out of restricted areas, locking servers, and generally minimizing any risk of physical breach.
- Implement access controls such as biometric systems, keycard entry, or security guards for sensitive areas.
- Ensure all visitors are logged and escorted at all times within secure areas.
- Conduct periodic reviews of physical security measures, ensuring all equipment is functional and personnel are trained in emergency protocols.
4. Establish Baseline Configurations
A baseline configuration provides a secure starting point for all systems and software. It means configuring systems so they are secure by default and ensuring any changes follow a strict process.
- Define standard security configurations for all IT systems, ensuring they meet NIST 800-171 security requirements.
- Use automated tools to enforce baseline configurations and identify any deviations.
- Regularly audit configurations to confirm compliance with baseline standards, updating them as new threats emerge.
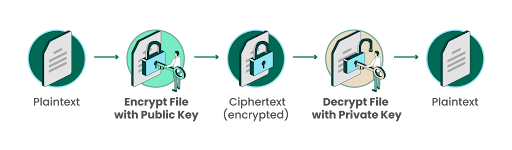
5. Encrypt Data at Rest and in Transit
Data encryption is crucial. Ensure that any CUI is encrypted both when stored and while being transferred. This helps protect against both physical theft (like lost drives) and cyber threats (such as intercepted communications).
- Deploy end-to-end encryption for data stored on devices and servers as well as data transmitted across networks.
- Use industry-standard encryption protocols such as AES-256 for data at rest and TLS 1.2 or higher for data in transit.
- Periodically test encryption configurations and update encryption methods as needed to address emerging vulnerabilities.
6. Conduct Regular Security Awareness Training
Phishing attacks are still one of the easiest ways for attackers to get in. Regular security awareness training reduces human error and keeps everyone vigilant. Make this a continuous process, not just an annual checkbox.
- Develop phishing simulations to test employee readiness and conduct follow-up training on weak spots.
- Incorporate hands-on workshops and scenarios to better prepare employees for real-world cyber threats.
- Track and report employee progress through training modules, ensuring regular updates and refreshers to maintain vigilance.
7. Implement a Risk Management Process
Risk management means regularly assessing your environment for weaknesses and addressing them before an attacker can exploit them. Vulnerability assessments, penetration testing, and patch management all fall under this umbrella.
- Create a vulnerability management program that includes regular penetration testing and vulnerability scans.
- Prioritize risk mitigation based on potential impact and likelihood, ensuring critical vulnerabilities are addressed first.
- Maintain an up-to-date risk register to document risks, mitigations, and responsible parties for easy review and accountability.
8. Create an Incident Response Plan
When the unexpected happens, being prepared saves time and money. An incident response plan outlines how to react, contain, and recover from an incident—with as little fallout as possible. Rehearse it regularly so that everyone knows their role.
- Develop detailed playbooks for various incident types (e.g., ransomware, phishing, data breach).
- Schedule routine incident response drills and tabletop exercises to test and refine the response plan.
- Ensure key personnel and stakeholders are fully aware of their roles and responsibilities with up-to-date contact information readily available.
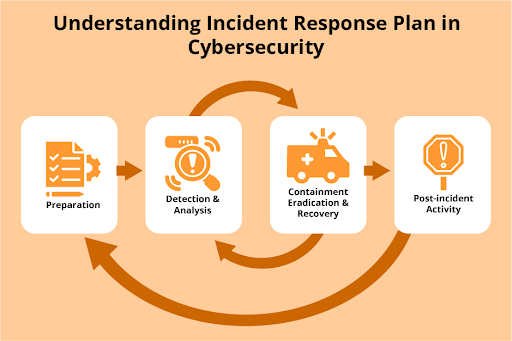
9. Maintain Audit Logs
Track and log every access to systems and CUI. These logs provide valuable information for forensic analysis in case of an incident and help prove compliance during assessments. Make sure they’re monitored and that access to logs is restricted.
- Implement a centralized logging solution that aggregates and secures audit logs from all systems and devices handling CUI.
- Set up automated workflows and alerts for suspicious activity detected in the logs, ensuring quick response to potential breaches.
- Regularly review and archive logs according to retention policies, ensuring they are available for both security investigations and compliance audits.
10. Secure Your Supply Chain
Your security is only as strong as the weakest link in your supply chain. Vet suppliers and ensure they meet NIST 800-171 requirements as well. Encourage your clients to include cybersecurity clauses in supplier agreements.
- Conduct third-party risk assessments to ensure all suppliers adhere to NIST 800-171 standards.
- Include clauses in contracts that enforce cybersecurity requirements and penalties for non-compliance.
- Continuously monitor suppliers for security incidents or changes in their security posture, addressing risks proactively.
Start Your Path to Compliance
Compliance isn’t a one-and-done deal. It’s a continuous journey that evolves as regulations change, technology advances, and threats emerge. For MSP/MSSPs, offering NIST 800-171 compliance support is more than a value-add; it’s about protecting the business and ensuring clients keep those federal contracts coming.
Cynomi’s vCISO platform is built to simplify compliance for MSPs/MSSPs, taking the manual, time-consuming work out of compliance assessments. Whether it’s mapping controls or generating policies, Cynomi helps you focus on the bigger picture—keeping clients compliant and secure while freeing you up to focus on strategic growth.
Ready to see how Cynomi can make compliance easier for you and your clients? Schedule a demo today.