
From small startups to multinational corporations, no organization is immune to the all-seeing eye of hackers and cybercriminals.
By 2025, cybercrime is projected to cause global damages of $10.5 trillion, surpassing many countries’ GDP. Businesses face an average of 130 security breaches each year, with each incident potentially costing millions of dollars in recovery, lost business, and reputational damage.
Many regulations and standards, including the CIS Critical Security Controls, aim to help businesses protect themselves against cyber risks. Although these regulations provide essential guidelines for protection, implementing them can be complex and time-consuming. Hence, many organizations turn to MSPs/MSSPs to help them roll out and adhere to regulations like CIS and others.
What are CIS critical security controls?
The Center for Internet Security (CIS), a non-profit organization, created the CIS Critical Security Controls to help organizations strengthen their cybersecurity defenses. The most recent version of the Controls is V8, which was established in 2018.
The Controls offer a practical and effective roadmap to identify and address vulnerabilities, reducing the risk of cyber attacks. Implementing these controls strengthens organizations’ security postures and protects systems and data, fostering trust among stakeholders and clients.
What are CIS Implementation Groups (IGs)?
The CIS Controls are divided into three Implementation Groups (IGs) to help organizations prioritize implementation based on their size, resources, and specific risk profile. Generally, CIS recommends:
- IG1: Covers essential cyber hygiene practices to protect against common attack vectors. Designed for small and medium-sized businesses with limited cybersecurity knowledge and resources.
- IG2: Expands on IG1 with more recommendations applicable to larger organizations with complex operational environments and higher risk profiles. It’s also a step up from IG1 in terms of the resources and time investment required to implement.
- IG3: Includes safeguards and recommendations to protect against sophisticated attacks. IG3 is most relevant for organizations with mature cybersecurity programs, sensitive data, and strict regulatory requirements to follow.
Why are the CIS critical security controls important?
1. Simplified Compliance
Many industry and government regulations align with the CIS Controls, a win-win for organizations’ compliance efforts. MSPs and MSSPs can support clients in implementing the security Controls, which streamlines clients’ compliance efforts and demonstrates their commitment to security standards.
2. Proactive Risk Management
The CIS Controls emphasize preventive risk management rather than reactive, helping your clients stay ahead of emerging threats and minimize potential damage. MSPs/MSSPs can leverage this proactive approach to differentiate themselves from competitors as trusted security advisors.
3. Cost Savings
The CIS Controls can help your clients avoid costly downtime, legal fees, and reputational damage by preventing security incidents and data breaches. Highlighting these potential cost savings can attract budget-conscious clients and demonstrate the return on investment of security services.
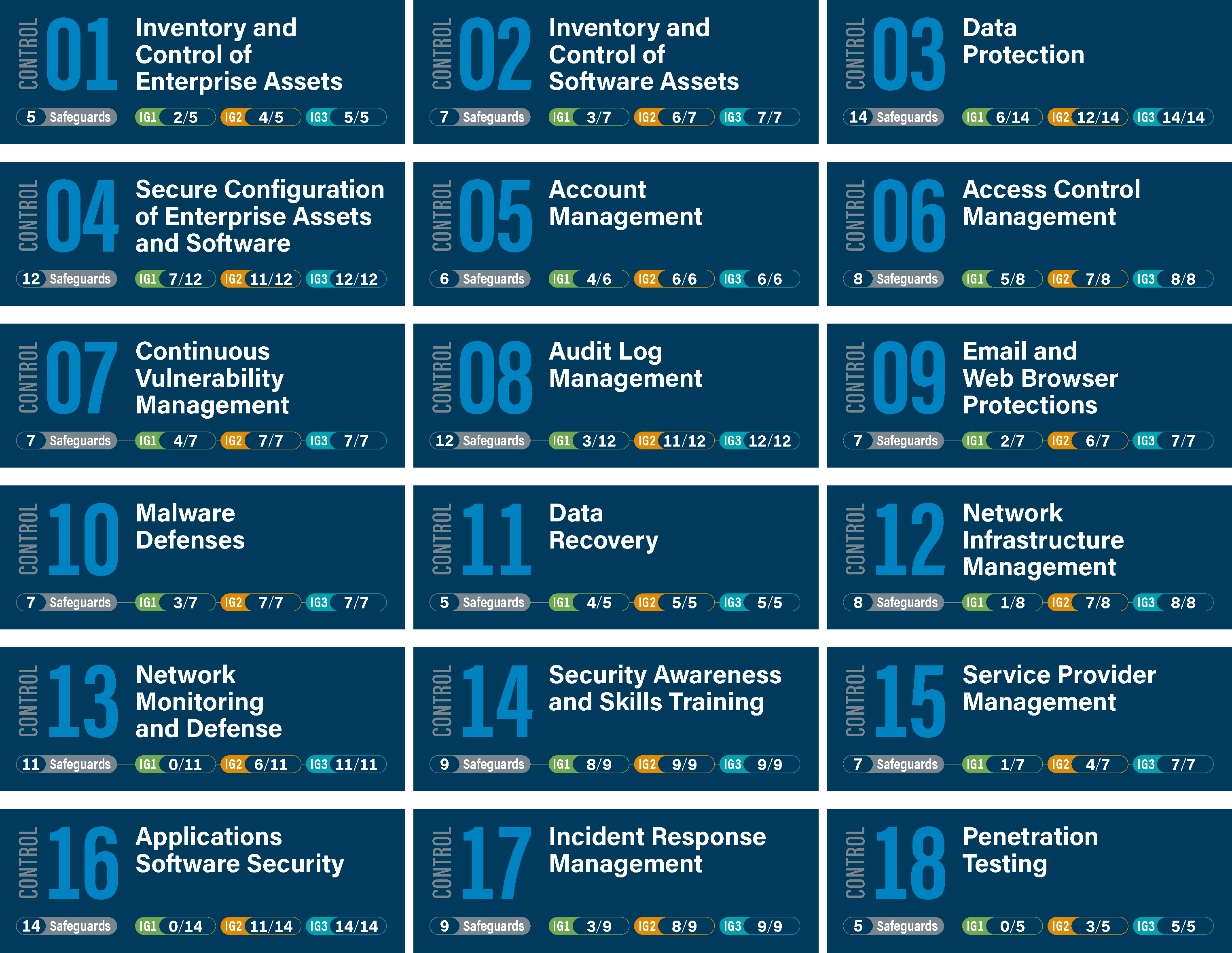
The 18 CIS Critical Security Controls Listed
1. Inventory and Control of Enterprise Assets
Knowing what’s on your client’s network is the first step in protecting it. You can actively manage all hardware and software assets on your client’s network, ensuring that only authorized devices and software are given access. Automated asset discovery tools can help maintain an up-to-date inventory, and regular software installation audits are also necessary to remove unauthorized applications.
2. Inventory and Control of Software Assets
Next up, you need to actively manage all software on the client’s network so that only authorized software can be installed and executed. Application whitelisting can prevent unauthorized software from running. Of course, keeping software patched and up-to-date mitigates vulnerabilities that attackers could exploit.
3. Data Protection
You can advise clients to encrypt sensitive data at rest and in transit, which adds a layer of security that makes it difficult for attackers to access the data even if they gain access to the system. Implementing strong access controls is also a go-to to prevent unauthorized access.
4. Secure Configuration of Enterprise Assets and Software
Your clients must establish and maintain secure configurations for all authorized devices and software, including developing and enforcing configuration standards for operating systems, applications, and network devices. As an MSP/MSSP, you can regularly audit configurations to ensure compliance with these standards and help identify any misconfigurations attackers could exploit.
5. Account Management
You can guide your clients in assigning and managing the authorization and authentication of all accounts, such as strong password policies. Implementing multi-factor authentication (MFA) adds an extra layer of security by requiring users to provide multiple forms of identification before accessing sensitive systems or data.
6. Access Control Management
Clients should control access to critical assets based on the least privilege and need-to-know principles. Role-based access control (RBAC) can restrict access based on job function. Plus, MSPs/MSSPs can regularly review and update clients’ access permissions to ensure access remains appropriate as roles and responsibilities change.
7. Continuous Vulnerability Management
As an MSP/MSSP, it’s your responsibility to assess and remediate vulnerabilities in your clients’ systems and applications. Tools for vulnerability scanning can help you pinpoint vulnerabilities, and it’s crucial to prioritize remediation according to the risk level.
8. Audit Log Management
Collecting, managing, and analyzing event audit logs helps clients detect, understand, or recover from attacks. Therefore, MSPs/MSSPs can advise clients that centralizing log collection and storage is recommended. Log analysis tools can help identify suspicious activity indicating an ongoing or attempted attack.
9. Email and Web Browser Protections
MSPs/MSSPs must guide clients in improving threat detection of email and web vectors using strategies like email filtering and web application firewalls (WAFs). Web filtering can block access to malicious websites, preventing users from inadvertently downloading malware or exposing sensitive information.
10. Malware Defenses
Controlling malicious code installation, spread, and execution is paramount. Using antivirus and anti-malware software, keeping software patched and up-to-date, and educating users about safe computing practices can help achieve malware defense.
11. Data Recovery
MSPs/MSSPs can establish and maintain data recovery practices sufficient to restore clients’ assets to a pre-incident state. Maintaining regular backups of critical data is crucial to guarantee recovery in case of a system failure, data corruption, or cyber attack, and you should always test the backups to check their ability to restore successfully.
12. Network Infrastructure Management
Ensure that only authorized devices can access the client’s network by actively managing (tracking, reporting, and correcting) all devices. Network mapping tools can identify all network devices, including unauthorized or rogue ones. Segmenting the network helps isolate critical assets, limiting the potential damage from a security breach.
13. Network Monitoring and Defense
MSPs/MSSPs can help clients implement the Controls by maintaining comprehensive network monitoring and defense against security threats. For example, intrusion detection and prevention systems (IDPS) monitor network traffic for suspicious activity like fraud risks, alerting security teams to potential threats.
14. Security Awareness and Skills Training
Your clients must establish and maintain a security awareness program to influence employees’ behavior and equip them with the necessary skills to reduce cybersecurity risks. MSPs/MSSPs can recommend phishing simulations that assess employees’ awareness and preparedness, pinpointing areas requiring further training.
15. Service Provider Management
MSPs/MSSPs can help clients develop a process to assess, manage, and monitor risks associated with using cloud providers. Monitoring cloud provider security practices is necessary to ensure they meet your client’s security requirements.
16. Application Software Security
Clients might rely on MSPs/MSSPs to manage the security life cycle of all in-house-developed and acquired software. If so, you can guide them in using practices during software development to minimize the introduction of vulnerabilities. Before releasing the software into production, it is crucial to conduct software security testing to identify and fix any vulnerabilities.
17. Incident Response Management
MSPs/MSSPs can support clients in establishing and maintaining an incident response capability that enables a timely and effective response to detected security events. For example, you can provide an incident response plan outlining the necessary actions during a security incident and conduct regular incident response drills to ensure your client’s team is prepared to respond effectively.
18. Penetration Testing
Test the effectiveness of your client’s security controls by simulating attacks against their information systems. Strategies include conducting regular penetration tests to uncover vulnerabilities that other security measures might miss and using the results to enhance security controls and fortify the organization’s overall security posture.
Implement the CIS Controls and More With Cynomi
The threat of cyber attacks is a constant concern for businesses of all sizes. The CIS Critical Security Controls provide a comprehensive framework for organizations to strengthen their defenses and protect their valuable assets.
Cynomi’s AI-powered vCISO platform continuously analyzes your clients’ cyber profiles against the latest threat intelligence and industry frameworks, such as the CIS Controls, NIST Cybersecurity Framework, and ISO 27001. With Cynomi, MSPs/MSSPs gain the insights and tools needed to stay ahead of the curve. With automated assessments, automatic mapping of controls, customized policies, and actionable recommendations, Cynomi empowers you to deliver comprehensive cybersecurity solutions that drive business growth and instill confidence in your clients.
Book a Demo today to explore how Cynomi can help you deliver compliance assessments in line with standards like CIS and more.