
It’s no longer a question of if an attack will happen but when. Imagine waking up to find your client’s data locked behind a ransomware paywall or seeing their website is down due to a Distributed Denial of Service (DDoS) attack.
What were once worst-case scenarios are now common disasters, so it’s unsurprising that the annual average cost of cybercrime is predicted to hit more than $23 trillion by 2027. As a result, many MSPs and MSSPs are turning to robust incident response tools to support them in detecting, investigating, and responding to security incidents efficiently.
What are incident response tools?
Cybersecurity incident response tools are programs designed to help you identify, assess, and counteract threats. They reduce the time threats remain hidden and mitigate their impact as early as possible. MSPs and MSSPs use incident response tools as part of their MSP software toolkit to rapidly respond to security incidents across multiple clients, improving trust and ensuring security.
Advantages of Using Incident Response Tools
- Rapid Incident Detection: Incident response tools offer real-time monitoring and alerting capabilities, allowing MSPs/MSSPs to detect threats quickly. This early detection is crucial for preventing potential damage and maintaining the trust of your clients.
- Incident Prioritization: The tools can sort events and match severity, allowing better handling of critical issues before they escalate into huge problems. Prioritization is essential even in the early stages of risk assessment and incident forecasting.
- Streamlined Communication: Incident response tools often include features that facilitate effective communication between the IR team and stakeholders. It ensures everyone is informed about the situation and understands their roles and responsibilities.
- Automation: Automate incident responses to reduce the number of tasks and responses that IT teams need to complete. Hence, you can handle more incidents with the same effort and your current resources.
Key Features to Look For in an Incident Response Tool
- Real-time monitoring and alerts enable early threat detection, allowing MSPs/MSSPs to respond quickly and minimize potential damage.
- Incident management and prioritization allocate resources efficiently to highlight the most pressing security concerns.
- Automated response capabilities take care of initial threat and dynamic risk assessments, notification, and mitigation.
- Detailed reporting and analytics, plus comprehensive reporting and analytics features, help MSPs/MSSPs understand the nature and impact of security incidents.
- Integration with other security tools improves operational functionality.
Essential Questions to Ask Before Choosing an Incident Response Tool
- Does the tool integrate with your existing security infrastructure?
- What level of automation does the tool provide for incident detection and response?
- How scalable is the tool to meet your growing needs?
- What type of reporting and analytics capabilities does the tool offer?
- What is the total cost of ownership, including licensing, maintenance, and support?
Top 10 Incident Response Tools
1. Splunk Enterprise Security
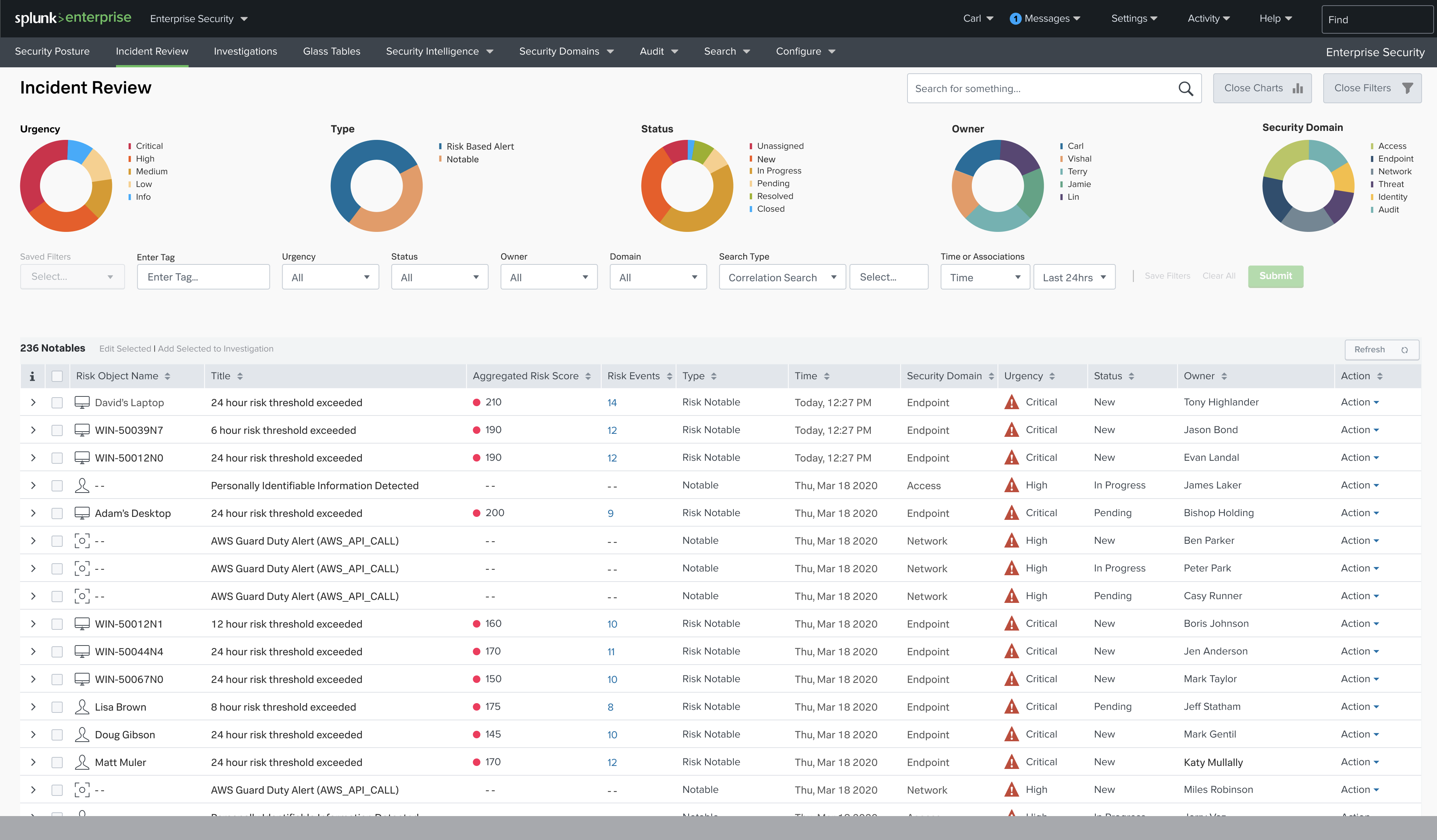
Splunk Enterprise Security is a comprehensive platform designed for security teams to quickly detect, investigate, and respond to advanced threats.
Features
- Real-time monitoring.
- Offers structured workflows and tools for investigations.
- Integrates with external threat intelligence sources to enhance threat detection capabilities.
- Uses machine learning to identify patterns and anomalies indicative of security threats.
- Provides customized dashboards and reports to visualize security posture and incident trends.
Best for: MSPs/MSSPs of all sizes looking for real-time monitoring features.
Pricing: Splunk offers flexible pricing models to suit various business needs.
2. ASGARD Management Center
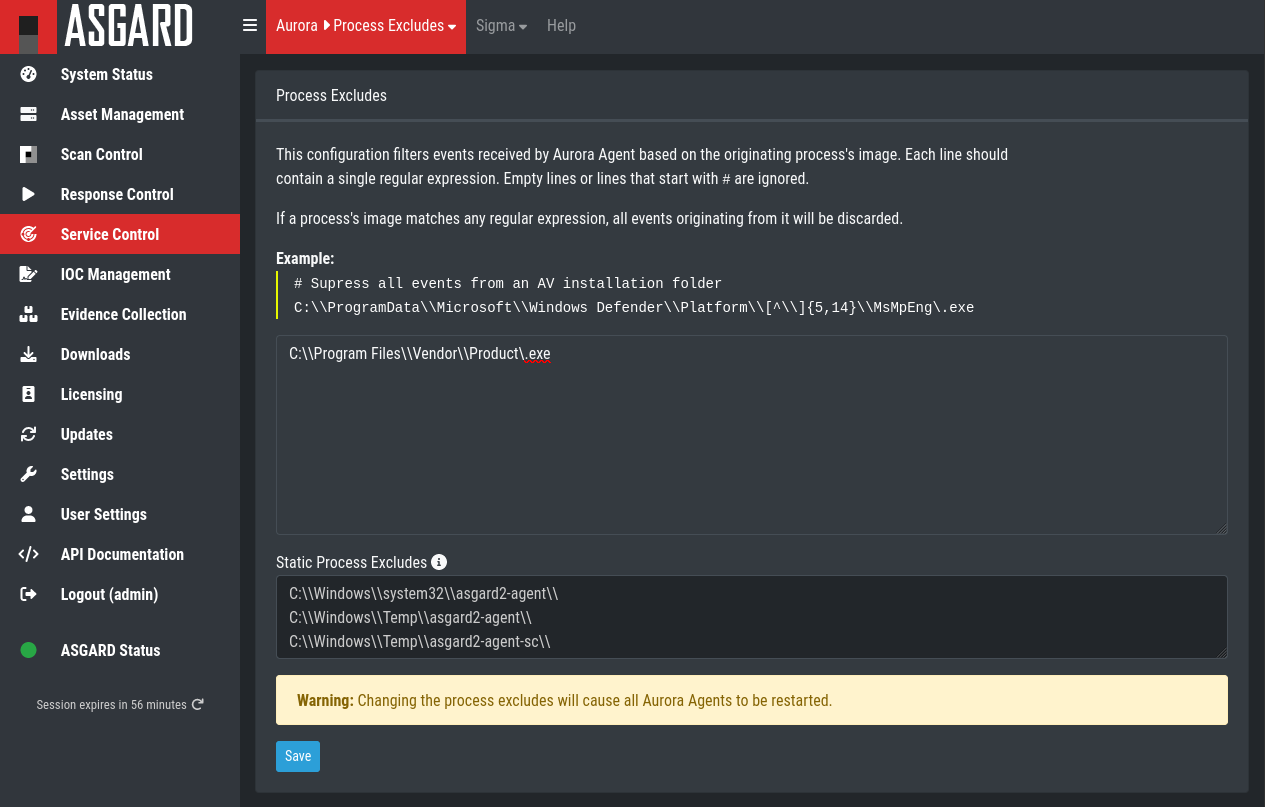
ASGARD Management Center is a lightweight endpoint detection and response (EDR) tool designed for threat detection and incident response in small to medium-sized enterprises (SMEs) and individual users.
Features
- Detects and analyzes malware behavior on endpoints.
- Monitors for indicators of compromise to identify potential security incidents.
- Conducts proactive threat hunting to identify hidden threats.
- Monitors changes in critical system files for suspicious activities.
- Enables remote forensic investigations of endpoints.
Best for: MSPs/MSSPs and individual users looking for a lightweight EDR solution.
Price: Lite products are free, and you can get other products by inquiry.
3. ManageEngine EventLog Analyzer
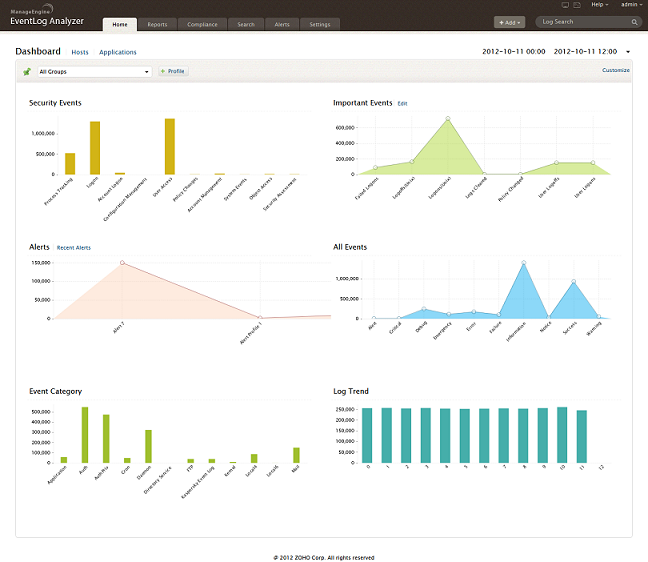
ManageEngine EventLog Analyzer is an SIEM (Security Information and Event Management) tool for comprehensive incident response management and log analysis.
Features
- Collects and correlates logs from various sources to identify security incidents.
- Monitors events in real-time for immediate threat detection.
- Provides automated incident detection and response capabilities.
- Generates compliance reports to meet regulatory requirements.
- Monitors user activity to detect anomalies and insider threats.
Best for: Suitable for MSPs/MSSPs of all sizes looking for an integrated SIEM solution for incident response and log management.
Price: Offers three pricing plans: Free, Premium, and Distributed.
4. BlackPoint Cyber SNAP-Defense
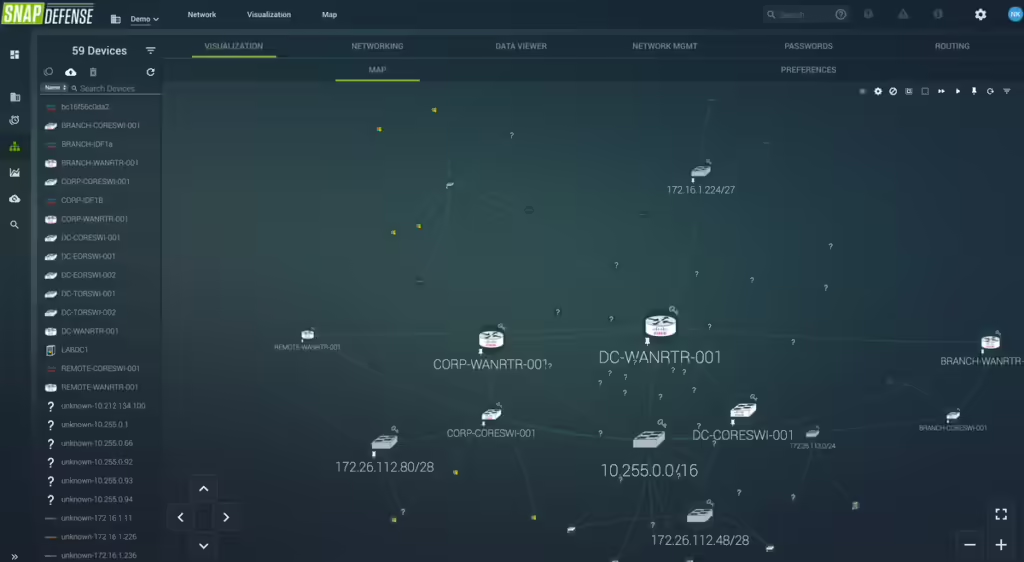
BlackPoint Cyber SNAP-Defense is a managed detection and response (MDR) solution that provides proactive cybersecurity protection through real-time threat detection and response capabilities.
Features
- Real-time security monitoring.
- Rapid response to security incidents with automated actions.
- Use behavioral analysis to identify anomalous activities and potential threats.
- Conducts detailed forensic analysis to understand the scope and impact of security incidents.
Best for: MSPs/MSSPs seeking an MDR solution combining automated threat detection and expert-driven incident response capabilities.
Price: By inquiry.
5. Cisco SecureX
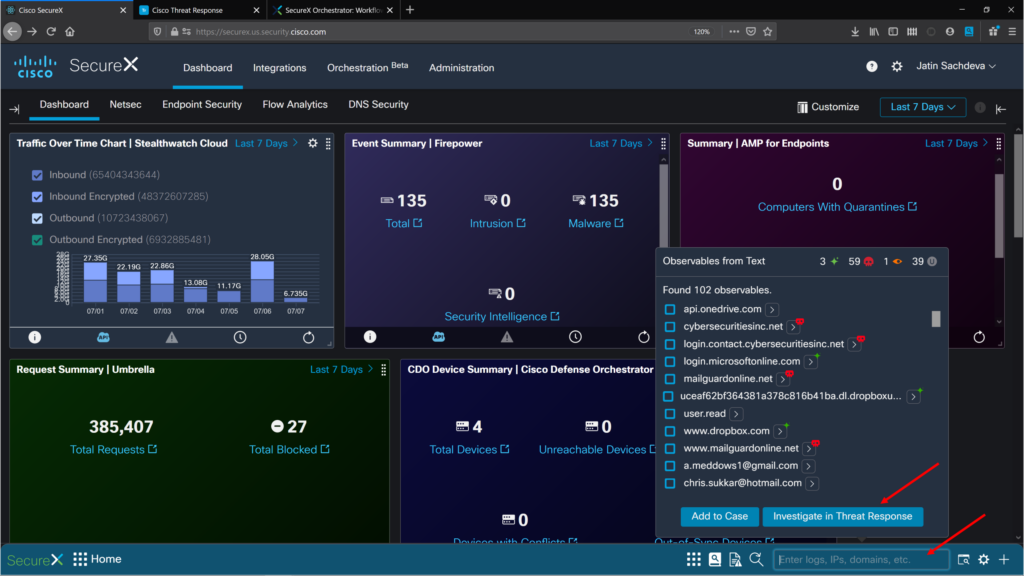
Cisco SecureX is an integrated security platform that provides unified visibility, automation, and orchestration across your clients’ security infrastructure.
Features
- Centralized visibility across network, endpoint, cloud, and applications.
- Automates response workflows and orchestrates security operations.
- Integrates with threat intelligence feeds for enhanced threat detection.
- Enables fast incident investigation and response through automated actions.
Best for: MSPs/MSSPs looking for a centralized dashboard to manage security operations, threat detection, and response capabilities.
Price: By inquiry.
Top 5 Incident Response Services
6. ArcticWolf CyberSOC
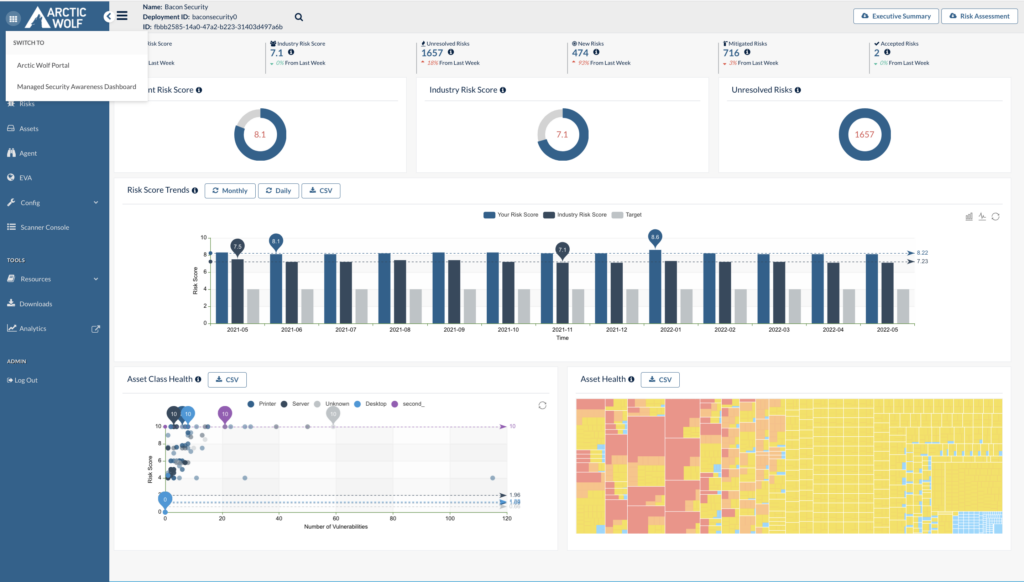
ArcticWolf CyberSOC is a managed detection and response (MDR) service that provides comprehensive cybersecurity protection by combining human expertise with machine intelligence.
Features
- 24/7 monitoring of network traffic and endpoints for threats.
- Real-time detection and response to security incidents.
- Proactive searching and scanning for vulnerabilities and hidden threats.
- Analyzes user and entity behavior to detect anomalies.
Best for: MSPs/MSSPs seeking a managed cybersecurity service that combines human expertise with AI-driven analytics.
Price: By inquiry.
7. Cysiv SOC-as-a-service
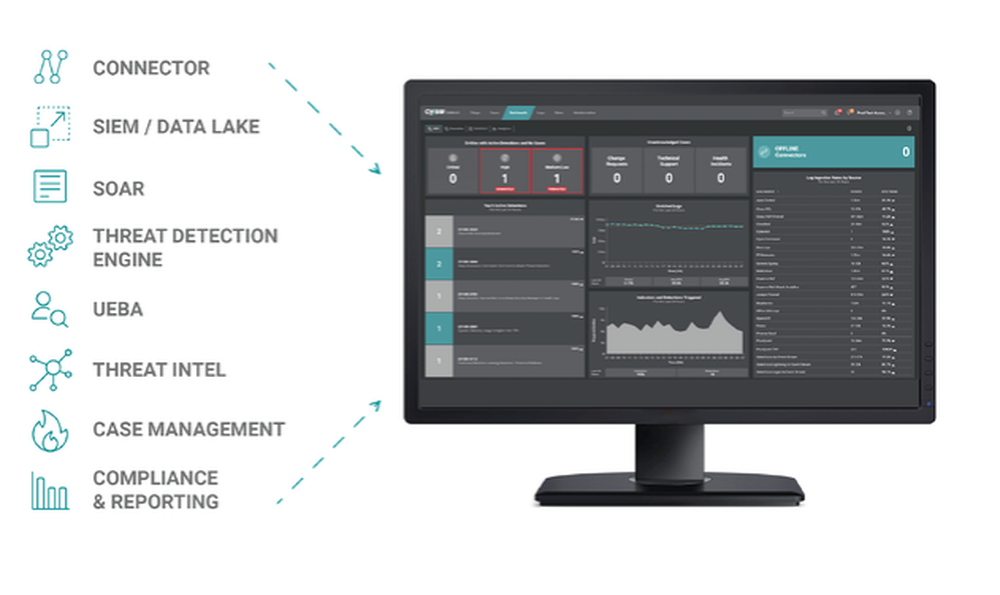
Cysiv SOC-as-a-service is a managed security operations center (SOC) solution that provides continuous threat monitoring, detection, and response capabilities.
Features
- Continuous monitoring of security events and incidents.
- Real-time detection and response to security threats.
- Integration with threat intelligence feeds for enhanced detection capabilities.
- Conducts detailed forensic analysis of security incidents.
- Generates compliance reports based on security events and incidents.
Best for: MSPs/MSSPs looking for 24/7 threat detection and response without an in-house SOC.
Price: By inquiry.
8. Heimdal XDR
Heimdal XDR (Extended Detection and Response) is a managed cybersecurity solution that detects and responds to advanced threats across endpoints and networks.
Features
- Monitors and responds to threats in real-time.
- Provides comprehensive EDR capabilities to detect, investigate, and remediate endpoint threats.
- Analyzes network traffic to identify anomalies and potential security breaches.
- Uses automated workflows to streamline the incident response process.
- Uses external threat intelligence to enhance the detection and understanding of new and emerging threats.
Best for: MSPs/MSSPs looking for a managed XDR solution that combines endpoint and network security.
Pricing: By inquiry.
9. Sophos
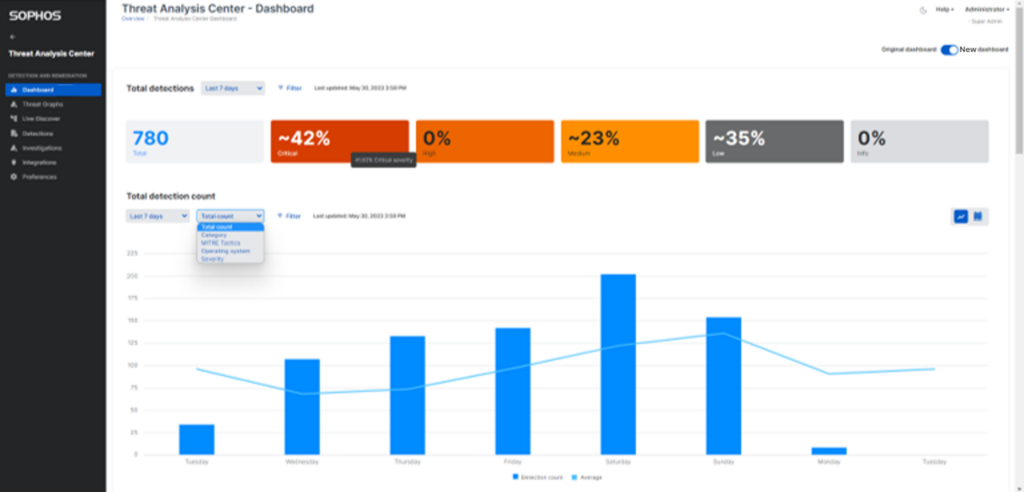
The Sophos incident response service is offered in two forms: a retainer service and a rapid response service. The retainer service provides clients with immediate access to a team of incident response experts, and the rapid response option is designed to monitor threat occurrence.
Features
- Immediate identification and neutralization of active threats.
- 24/7 access to a team of security experts.
- Discounted pricing on fixed-fee incident response services.
- Compatible managed detection and response (MDR) service providing 24/7 monitoring.
- Remediation guidance.
Best for: Smaller MSPs/MSSPs looking for a hands-off approach with their IR vendor. With Sophos, you can pay a subscription and not worry about IR for a whole year.
Pricing: The incident response retainer service is an annual subscription, and other pricing is by inquiry.
10. Check Point Incident Response
Check Point Incident Response is a service that helps MSPs/MSSPs respond to cyberattacks. It includes a hotline, forensic analysis, and recommendations to improve security controls.
Features
- 24/7 hotline enables you to contact the team at any time.
- Continuous forensic system analysis.
- Extensive documentation and best practices guidance provided.
- Remediation recommendations offered using real-time data.
- Custom security controls, including custom signatures, traffic and attack analysis, rule-based protection activations, customized protections, and third-party systems and service provider protection.
Best for: MSPs/MSSPs looking for peace of mind through 24/7 incident response hotline availability.
Pricing: By inquiry.
Build Your Incident Response Policy
Each tool discussed above offers unique features to help you detect, respond to, and mitigate security incidents effectively. However, managing incident response can be complex and resource-intensive. MSPs/MSSPs often struggle with high operational costs, scalability constraints, and the need for specialized cybersecurity expertise. This is where Cynomi can make a significant difference.
Cynomi is an automated vCISO platform that combines proprietary AI algorithms with CISO-level knowledge. It provides a built-in incident response policy template to support your incident response, compliance, and security efforts. Our platform performs automated readiness assessments for each of your clients, then creates actionable plans and clear policies with a prioritized task list to help MSPs/MSSPs achieve compliance while tracking client progress.
Offering incident response as part of your comprehensive set of services is a must for growing and scaling your MSP/MSSP business. Cynomi supports policy creation and provides clear reporting to help you communicate progress to clients and stakeholders, prove value, and generate upsell opportunities.
Discover how Cynomi can enhance your incident response strategies by scheduling a Demo today.