Top Security Policies
Navigating NCSC CAF: What MSPs Need to Know in 2025

The NIS 2 Directive: Impact on MSPs, MSSPs and Their Clients

What the 2024 CrowdStrike Incident Means for MSPs/MSSPs
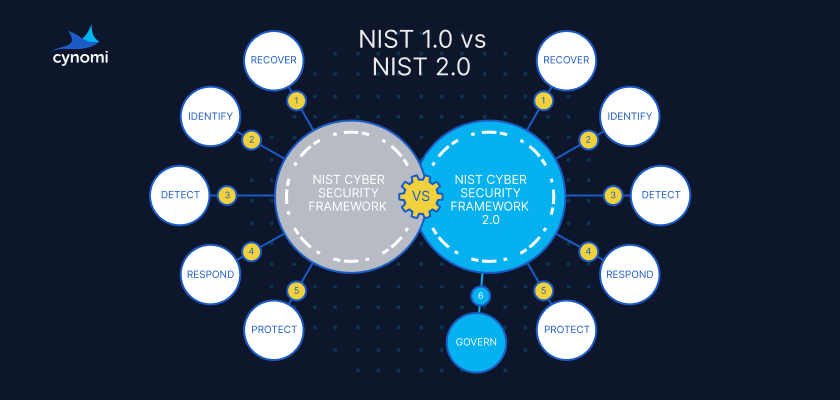
What MSPs & MSSPs need to know about NIST 2.0, in 4 questions

Understanding CMMC 2.0: What MSPs & MSSPs Need to Know

Managed Service Providers Must Step Up to Help Their Customers Minimize Generative AI Risk

Top IT Security Policies to Implement: Cybersecurity Awareness

Top IT Security Policies to Implement: Email Security
