The Business Impact Analysis Template for Download

There’s a sweet spot in cybersecurity that sits between the technical and business sides of the coin. The link between cybersecurity and wider business goals calls for an analysis that mitigates risks and unlocks opportunities for businesses to thrive (securely) in a digital-first world.
Clients need to understand this interplay to effectively reduce the risk of incurring skyrocketing breach costs. The latest findings put this cost at $4.88 million per data breach, an increase of 10% in just a year.
Using a detailed business impact analysis (BIA) template, MSPs and MSSPs can identify areas where security enhances operational performance, aligns with compliance requirements, and directly contributes to clients’ long-term business success.
What is business impact analysis from an InfoSec perspective?
Business impact analysis in cybersecurity focuses on identifying how cybersecurity threats could impact business operations, everyday activities, and financial stability. It’s about identifying opportunities to add value through changes in security processes, technological solutions, or higher-level structures.
By supporting clients through BIA-related tasks, MSPs/MSSPs can add more value through security services and provide tailored and strategic insights. When MSPs/MSSPs take a proactive, customized approach to BIA, they can help clients build a security posture that is reactive and strategically positioned to support growth, compliance, and resilience.
What is a business impact analysis template?
MSPs/MSSPs can use a business analysis template as a structured guide to assessing a client’s security needs and their interplay with broader business goals. The template aims to prepare clients for possible operational disruptions that are not only caused by cyber threats—it can also cover incidents like natural disasters, power outages, and a loss of key suppliers.
Some business impact analysis templates are based on established cybersecurity frameworks like NIST, ISO 27001, or CIS Controls, which ensures that your analysis considers best practices relevant to your client’s industry.
What are the advantages of a business impact analysis template?
Better Collaboration
The template ensures that IT and business leaders in your client’s organization speak the same language by defining security objectives in business terms, which fosters smoother communication and cooperation.
Optimizing Client Costs
Without a structured BIA template, clients might end up with multiple overlapping tools or services that provide redundant functions. A template allows MSPs/MSSPs to evaluate the client’s current technology stack, identify gaps and redundancies, and recommend only the truly necessary solutions for business resilience.
Shifting Cybersecurity Left
Having a template is a great way to embed security into the foundation of clients’ business processes and IT operations. This proactive approach helps in catching potential operational disruptions before they turn into larger, more costly problems that detract from the ability to achieve wider business goals.
Standardization and Repeatability
Delivering consistent, high-quality security services across various clients is essential for MSPs/MSSPs. The template ensures that each security assessment, plan, and implementation follows a structured, repeatable approach.
The Business Impact Analysis Template for Download
1. Define Business Objectives
Before diving into security measures, you must understand the client’s business resilience goals (e.g., growth, compliance automation, risk reduction, etc.) and how security fits into those targets. Hold discussions with C-suite executives to understand key business goals, business-critical systems, and operations.
Critical questions at this stage include:
- Which people or departments are the owners of business-critical processes?
- What internal points of contact should the BIA take note of?
- What external points of contact should the BIA take note of?
- Which systems do the business-critical processes depend on? (E.g., payroll software.)
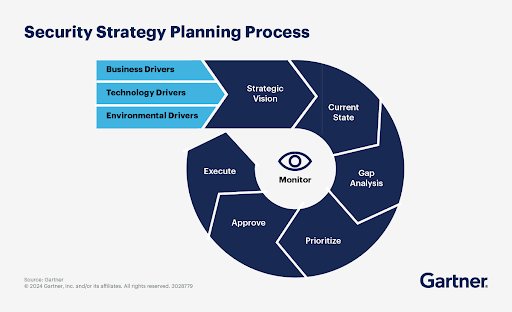
2. Identify Resource Requirements
This step involves evaluating all the resources needed to get your client’s business up and running again. For example, you may require:
- Stakeholders or key employees.
- Systems and software.
- Data, assets, or business records.
A best practice is to rank these resources in order of priority, considering which are the most important for business continuity and recovery initiatives.
3. Outline Systems Functionality
At this stage, you can analyze your client’s systems, including the architecture and any essential technical considerations, particularly any information relevant to recovery processes and protocols. The description could include backup procedures and physical risks (e.g., servers located in a high-risk flood area).
4. Requirements Gathering and Prioritization
Gather detailed security requirements based on the business objectives and input from stakeholders. These requirements should address regulatory needs, technical needs, and the specific risks that the business faces.
Conduct workshops with stakeholders to gather detailed requirements, including regulatory compliance needs (e.g., GDPR, HIPAA). Use a prioritization matrix to rank the importance of different security requirements based on factors like risk, cost, and business impact.
Prioritize security initiatives based on risk assessment and business priorities. Use a Gantt chart or project management tool like Smartsheet to lay out timelines for each initiative. Therefore, your client can allocate resources (e.g., budget, personnel, tools) to each phase of the roadmap.
5. Conduct a Current State Analysis (As-Is Assessment)
An “as-is” assessment outlines the client’s current security posture. Before proposing any new security measures related to the business impact analysis, you must have a clear understanding of where the client is at. At this stage, it’s a good time to conduct a security audit using tools to assess vulnerabilities or gaps.
Also, review existing security policies, procedures, and compliance with relevant regulations. Generic security solutions won’t provide the best protection, and the wrong tools could be a waste of resources. Therefore, you can provide a detailed comparison of different solution options to present to client stakeholders, including pros, cons, and costs.
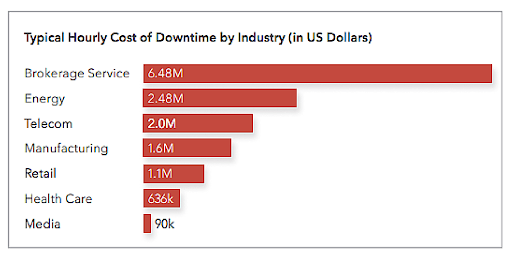
6. Predict the Cost of an Outage
In this step, MSPs/MSSPs can predict the impact of downtime on your client’s business. As cost is a significant concern for businesses of all sizes, separating outage impacts into cost-based categories is a good place to start. The cost amounts can vary from client to client, but the following categories are a good place to start:
- Severe
- Moderate
- Minimal
7. Estimate the Downtime
Now you’ve helped your client identify potential financial losses from an outage, you can include downtime estimates in the business impact analysis template. You can collaborate with client stakeholders to predict downtime based on a few factors:
- Recovery point objective (RPO): The maximum amount of data loss an organization is willing to tolerate after a disaster or other event. It’s expressed as a time period, usually the time since the most recent reliable backup.
- Recovery time objective (RTO): The maximum acceptable amount of time that a system or application can be down following an outage or disruption before it starts to have a significant negative impact on the business.
- Maximum tolerable downtime (MTD): The absolute maximum amount of time that a business process or system can be unavailable before it causes irreparable harm or unacceptable consequences to the organization. Essentially, it’s the point of no return—after this time, the organization may not be able to recover.
8. Define and Track Security Metrics
Establish key performance indicators (KPIs) and metrics to measure the effectiveness of security initiatives. These metrics should track both technical security (e.g., number of vulnerabilities reduced) and business outcomes (e.g., compliance status, risk reduction). This step is essential for allowing the client to measure the impact of security efforts, demonstrate ROI, and enable ongoing improvements based on measurable data.
Cynomi Helps You Create a Business Impact Analysis Template
A business impact analysis template can require a huge amount of manual work, but it’s a necessity for MSPs/MSSPs who want to best serve their clients. With Cynomi’s vCISO platform, you can roll out new services to clients without additional time or resource investment, including risk and compliance assessments, gap analysis, tailored policies, strategic remediation plans, and cybersecurity planning and management.
Cynomi’s automated vCISO platform combines proprietary AI algorithms with knowledge from some of the world’s best CISOs, enabling MSPs/MSSPs to offer more services without having to find new hires with the rare combined skillset of security prowess and business analytical skills.
With Cynomi, you can conduct audits and risk assessments in the platform at a fraction of the time and cost it would require for an employee. Being skilled at these assessments is one of the most critical parts of conducting a business impact analysis.
Cynomi automatically generates a tailor-made set of security policies based on the assessment and provides built-in intuitive and tailored questionnaires for each client. Cynomi also includes a built-in customer-facing reporting suite, making it easy to show the risk assessment results and progress to your clients.
Download the template here.