What does it take to be a full-fledged vCISO?

vCISO services are rapidly gaining traction among MSPs and MSSPs for their high-margin potential. While CISOs are in high demand, their expertise is scarce, which is why organizations often turn to vCISO services to bridge the gap to ensure they maintain robust security measures. Offering flexible, outsourced cybersecurity leadership that delivers significant value at a lower cost, a vCISO can reduce the risk of cyberattacks and protect sensitive information.
Not only do vCISOs help fill a growing need for organizations in need of strategic cyber services, but for service providers they provide differentiation and profit opportunities. These include recurring consulting revenues, upselling services as a result of newly discovered security gaps, and other highly-requested services. For MSPs and MSSPs, transitioning to offer comprehensive vCISO services is a strategic move that offers profit and efficiency if done right. However, transitioning to offering full-fledged vCISO services can be challenging.
Explore the full guide to master comprehensive vCISO services, and keep reading to gain top tips to make the transition seamless and profitable.
What is a vCISO?
Organizations increasingly face complex and evolving cybersecurity challenges but often lack the in-house expertise to tackle these issues. A vCISO provides the critical leadership needed to navigate these risks and strengthen cyber resilience. Whether it’s to address a shortage of skilled security professionals or to ensure robust cybersecurity strategies, a vCISO offers expert guidance tailored to the unique needs of the business.
A vCISO offers flexible, high quality cybersecurity leadership on a part-time or contract basis, bringing specialized expertise that can be challenging to find in-house, to ensure an organization’s cyber resilience. Instead of hiring a full-time CISO, businesses can subscribe to vCISO services for expert C-level cyber-assistance. vCISOs help prevent breaches, reduce risks, and mitigate attack consequences by building comprehensive cybersecurity programs.
Why More and More MSPs and MSSPs are offering vCISO services:
- They enable service providers to effectively meet their clients’ increasing demand for proactive cyber resilience, aligning their services with the growing market need
- They offer the potential to grow recurring revenues by expanding into a new customer base with strategic services
- They help service providers differentiate themselves
- They are an excellent vehicle from which to upsell additional cybersecurity services to existing customers who identify security gaps as a result of these offerings
- Those offering the complete range of vCISO services can charge a lot more while delivering highly valued services that earn word of mout
What do vCISO services include?
While vCISO service offerings can vary widely from client to client, here is a list of minimum services to offer:
Risk Assessment & Management
- Initial Risk Assessment: Most vCISO engagements begin with a risk assessment to understand the organization’s current cybersecurity posture.
- Ongoing Risk Management: This involves identifying, analyzing, and prioritizing risks based on the organization’s risk appetite and managing ongoing risk and remediation.
- Comprehensive Asset Management: Effective risk management aligns with business goals and requires identifying all systems, endpoints, and users to discover threats such as unpatched systems, weak passwords, and misconfigurations.
Strategy setting
- Developing Strategies: A thorough risk assessment enables the development of effective strategies to counter current and future threats.
- Aligning with Business Priorities: Cybersecurity strategies must align with business priorities and financial realities, setting a roadmap for short-term, mid-term, and long-term actions.
- Guiding Policy Creation: This roadmap guides policy creation for all employees and IT professionals, helping the organization address critical threats and tackle immediate cybersecurity issues.
Protection
- Implementing Controls: vCISOs must be proactive in remediating threats by implementing controls such as multi-factor authentication (MFA), strong password policies, firewalls, and anti-virus software.
- Protecting Assets: They also protect endpoints, data, networks, and emails through tools like endpoint detection and response (EDR) and email protection, as well as practices like vulnerability scanning and patch management.
Continuity planning
- Disaster Recovery (DR): Goes beyond backups, incorporating alternative data centers and infrastructure to ensure swift recovery from disruptions.
- Business Continuity (BC): Includes organizational and human elements, such as drills and personnel relocation plans, to ensure comprehensive preparedness.
- Guidance on BC and DR: The vCISO provides guidance on BC, DR, data protection, retention, archiving, and disposal.
Training & Security Awareness
- Comprehensive Training: Cybersecurity training should cover employee and executive security awareness, as well as advanced training for technical personnel.
- Partnering with Vendors: Partnering with a vendor for security awareness training, including phishing simulation tests, helps assess and improve employee resilience against malicious URLs and attachments.
- Continuous Improvement: IT and security personnel should undergo regular training and certification in threat detection, access management, and vulnerability management.
Compliance and Governance
- Aligning to Large Organization Needs: Large organizations impose their compliance frameworks and standards on any vendor they are selecting.
- Adhering to Standards: SMBs are often asked to show evidence they can fulfill applicable regulations and security frameworks like PCI-DSS, HIPAA, GDPR, ISO, CIS, NIST, and SOC 2.
- Avoiding Disruptions: vCISO providers can help SMBs align to these requirements and avoid significant disruptions in terms of time, money, and resources.
Incident response
- Initial Response: vCISOs manage the initial response to cyberattacks within the first 24-48 hours.
- Developing Plans: After addressing immediate threats, they develop a cybersecurity incident response plan, assign roles within the IT and cybersecurity teams, and engage third parties for remediation and recovery.
- Regular Drills: Regular incident response drills and table-top exercises are crucial for preparedness.
Third-party management
- Managing Risks: vCISOs manage security risks posed by third parties, including supply chain partners, SaaS vendors, and cloud providers.
- Defining Privileges: They ensure these connections do not become breach points by defining narrow access privileges and requiring multi-factor authentication for login.
Communication
- Strategic Direction: vCISOs manage and set the strategic direction for cybersecurity, including planning, execution, technology implementation, and policy setting.
- Alignment and Coordination: They ensure alignment between security and IT, coordinate teams, and integrate services smoothly.
- Effective Communication: A full-fledged vCISO understands the business mission, and risk appetite, and communicates effectively with top management and the board.
Providing holistic vCISO services
Each of the elements discussed offers significant value to customers and is necessary for providing effective and efficient cybersecurity. But, how can you scale your vCISO services when as mentioned earlier, qualified CISOs are few and far between at a high cost?
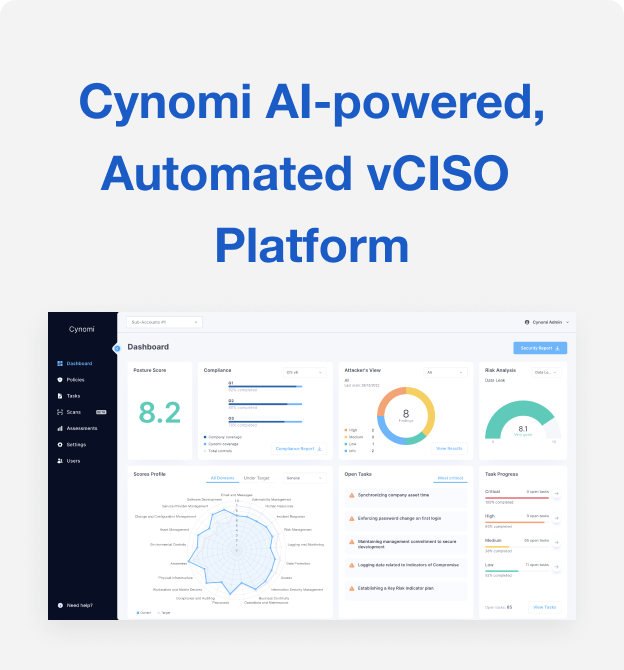
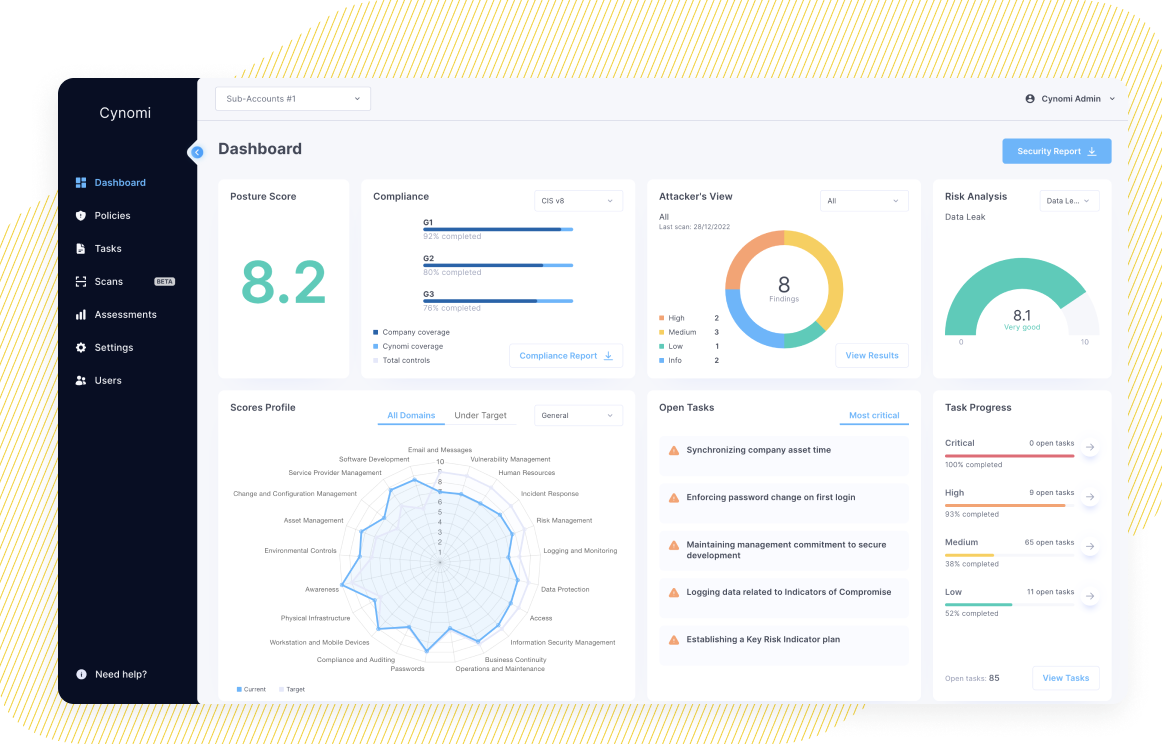
The answer: cyber security management platforms. vCISO platforms, like Cynomi, can take the MSPs and MSSPs from where they are currently, to being able to cover all aspects of vCISO services without additional resources.
To explore how you can enhance your service offerings, download our comprehensive guide and discover the steps to transition to a more robust vCISO service delivery. Understanding the essential functions of a vCISO, recognizing the upsell potential, and leveraging platforms like Cynomi will allow MSPs and MSSPs to scale their vCISO offerings efficiently and profitably.
Ready to elevate your cybersecurity services? Book a demo and discover how Cynomi can transform your vCISO offerings.