On August 8, NIST unveiled the draft for the updated NIST CSF framework. This new version includes several important changes designed to make the framework more effective and adaptable to the evolving cybersecurity landscape. David Primor, CEO of Cynomi, delves into the key changes in this new version and analyzes their potential significance and impact on the cybersecurity landscape.
A Brief Reminder: NIST CSF
NIST CSF is a powerful and popular cybersecurity framework for managing cybersecurity posture and reducing risk. It offers strategies, guidelines and best practices that guide organizations across the entire cybersecurity lifecycle: from identification to recovery. NIST CSF also aligns with various industry standards and is accepted by government agencies and leading organizations, further bolstering its credibility.
Thanks to its scope, structure, flexibility and scalability, NIST CSF has become one of the most popular and widely-adopted cybersecurity frameworks across organizations. While originally designed to protect critical infrastructure companies, NIST CSF is used by companies of different sizes (SMBs, mid-market, enterprise) and across verticals. Today, NIST CSF is considered a vital tool and an essential baseline for organizations worldwide when developing their cybersecurity programs.
What’s New in NIST CSF 2.0?
On August 8th, the National Institute of Standards and Technology (NIST) published a draft of version 2.0 of the CSF. The new draft includes a number of groundbreaking changes designed to make the framework more effective and adaptable to the evolving cybersecurity landscape. Let’s delve into the most important ones.
NIST CSF: Now Suitable for All Organizations
As mentioned, the NIST CSF framework was designed with a focus on safeguarding critical infrastructure. This includes organizations from national security, healthcare, finance, and similar industries. However, NIST has recognized that the challenges of cybersecurity are not confined to just these sectors; they are ubiquitous and impact organizations of all types and sizes.
Recognizing this universality, NIST has adapted the framework to be more inclusive, extending its applicability to all organizations, regardless of their industry or scale. NIST CSF 2.0 is a universally applicable guide that can help any organization improve its cybersecurity measures. Now, there’s no reason for any organization to hesitate before using this valuable resource for enhancing their security plans.
Practical Implementation Examples
While the NIST CSF framework continues to operate at a high level, NIST 2.0 has taken a significant step to bridge the gap between theory and practice. “Implementation Examples”, which are notional examples of action-oriented processes, help guide organizations on how to implement the framework. They help explain how the CSF’s guidelines, principles and best practices can be translated into actionable steps.
Before this addition, organizations might have found the framework’s recommendations to be somewhat abstract and hard to implement. Now, with these examples, the framework is easy to understand. Organizations essentially have a clear roadmap to follow.
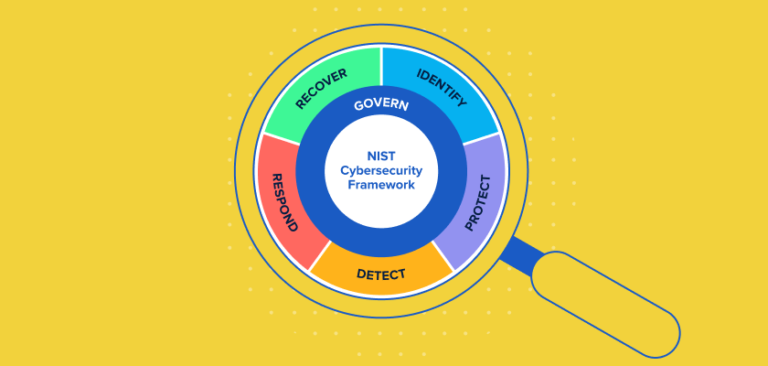
The Newest Function: Govern
Until now, the NIST Cybersecurity Framework comprised five core functions: Identify, Protect, Detect, Respond, and Recover, which were the gold standard for cybersecurity practices. These functions became so standardized they were widely adopted not only within the context of NIST, but also in various other frameworks and industries.
The recent addition of a sixth function—Govern—marks a significant evolution in the framework. This new function aims to delve deeper into the organizational and business context, taking into account elements such as risk management strategy and supply chain risk management, as well as the delineation of roles and responsibilities across the organization and the need for policy creation.
In my opinion, the inclusion of “Govern” is a bold move and a commendable step forward. Governance in cybersecurity is often the linchpin that holds all other functions together. It ensures that there is a coherent strategy and that everyone in the organization, from the top-level management to the operational staff, is aligned in their cybersecurity efforts.
My primary strategic security advice to any organization is to involve the management or CEO in cybersecurity discussions and decision-making. The level of commitment and oversight that comes from active management involvement and having a business-led cybersecurity strategy can be a gamechanger, setting the stage for a more robust and effective cybersecurity posture.
Supply Chain Risk Management
The emphasis on supply chain risk management in the updated framework is both timely and crucial. While the concept was present in earlier versions, its significance has been amplified, as supply chain vulnerabilities have increasingly become a target for cybersecurity attacks. The decision to give supply chain risk management greater focus is the right thing to do. It equips companies with the necessary guidance and tools to better understand, assess, and mitigate this complex and evolving risk, strengthening their overall cybersecurity posture.
Secure Software Development
Software development is the cornerstone of many organizations’ operations, making software development security critical. Therefore, the updated framework’s more rigorous requirements for secure software development are very welcome.
How to Implement NIST CSF 2.0
NIST aims to assist organizations in implementing this cybersecurity framework by offering adaptable profiles and prioritizing framework outcomes. This approach is highly logical as it allows for a tailored application of the framework to meet the unique needs of different organizations. However, the customization and prioritization process is best done by professionals with a deep understanding of the framework. These experts can focus on continuous assessment, prioritization, and review of cybersecurity measures.
For CISOs
With this updated framework, CISOs can more accurately determine their organization’s cybersecurity profile and develop a risk-based plan. This enhances the robustness of their cybersecurity measures, efficiently and rapidly.
For SMBs and Mid-Market
For SMBs and mid-market companies, framework-based platforms that use the NIST methodology could become a compelling solution for NIST CSF adaptation. These organizations often lack the in-house expertise needed to fully implement and manage the NIST cybersecurity framework. By leveraging platforms that are designed around the NIST methodology, these companies can more easily align their cybersecurity practices with industry standards, saving effort and time.
For MSPs and MSSPs
MSPs and MSSPs also stand to gain significantly from the updated NIST framework. The new insights and methodologies incorporated into the latest version offer a more holistic approach to cybersecurity risk management and make it easier to understand and implement. By integrating these advancements into their service offerings, MSPs and MSSPs can deliver more accurate and efficient risk assessments. They can also deliver more effective and up-to-date cybersecurity plans, tailored to the specific needs of their clients.
By making accurate and timely use of the new framework correctly, MSPs and MSSPs can enhance their value proposition while gaining a competitive edge in the market. Their clients, in turn, benefit from the most robust, adaptive, and cutting-edge cybersecurity strategy that aligns with recognized best practices, improving their overall security posture while optimizing resource allocation.
For Cynomi Users
We were incredibly enthusiastic about the new updated version of the NIST framework, so much so that we are taking proactive steps to already implement and map it within our Cynomi platform. This allows our partners and customers to become rapidly acquainted with the updated framework in a straightforward and easy-to-use manner, and to start leveraging the framework’s benefits and the dozens of new tasks it now includes, even before its formal publication.
Essentially, we are providing users with a unique opportunity to get a head start on enhancing their cybersecurity posture based on the new NIST CSF. It can also help them provide informed feedback to NIST on this draft, which NIST is accepting throughout November 4th. We’re thrilled to be the first platform to adopt and offer this excellent updated framework to our user community.