
Did you know that the number of data breaches in 2023 was a whopping 72% higher than in 2021? Static defense mechanisms that worked a few years ago are clearly struggling to keep up with the agility of today’s cyber attackers. This means your cybersecurity defenses are probably already outdated merely days or weeks after you’ve implemented new controls. That’s the breakneck speed at which cyber threats are evolving today.
No longer can we rely on set-and-forget security measures – the ever-evolving nature of threats demands dynamic risk assessments to help MSP/MSSPs and your clients stay one step ahead.
What is a Dynamic Risk Assessment?
A dynamic risk assessment (DRA) is a continuous, iterative process that identifies, evaluates, and manages risks in settings where conditions frequently change. Unlike static risk assessments, which rely on historical data to provide a one-time snapshot, dynamic risk assessments continuously adapt to new threats and changing operational conditions.
DRAs are designed for decision-makers and professionals like CISOs who manage high-risk situations on a regular basis and use the latest data to steer decision-making.
What is the difference between a risk assessment and a dynamic risk assessment?
The main distinction between standard and dynamic risk assessments is their response to change and uncertainty. Traditional risk assessments are usually carried out at set times – annually or semi-annually – and assume that the work environment and external factors stay constant over time.
In contrast, dynamic risk assessments are fluid and evolving to capture the nuances of changing environments. They involve an active approach, where changes in the internal and external setup and in the regulatory environment prompt immediate updates to risk management table practices. Hence, dynamic risk assessments are particularly effective in unpredictable or high-risk settings where adaptive risk mitigation strategies are required for safety and compliance (like cybersecurity, critical infrastructure, and supply chain management).
What are the Goals of a Dynamic Risk Assessment?
- Improve response times to emerging threats and incidents.
- Ensure continuous safety and compliance even under variable and unpredictable circumstances.
- Maintain the relevance of risk management practices by aligning them with the current state of the environment, avoiding reliance on outdated information.
- Increase efficiency in using resources and reducing downtime by focusing efforts where they are most needed, based on the latest assessments.
Why Do You Need to Perform a Dynamic Risk Assessment?
Detect Threats in Real-Time
Constantly monitor your network for signs of unusual activity and scan for emerging and known security threats. Quickly identify any potential breaches or vulnerabilities to prevent attackers from exploiting them.
Anticipate Future Threats
Data analytics helps you examine trends in cyber attacks and gather insights from recent security incidents. This analysis enables you to foresee and thwart future threats by building robust defense systems.
Optimize Resources
You can evaluate the risk levels across different parts of your network to effectively allocate your cybersecurity resources. A dynamic risk assessment helps you focus on areas with the highest risk or critical vulnerabilities to maximize the impact of your security investments and manpower.
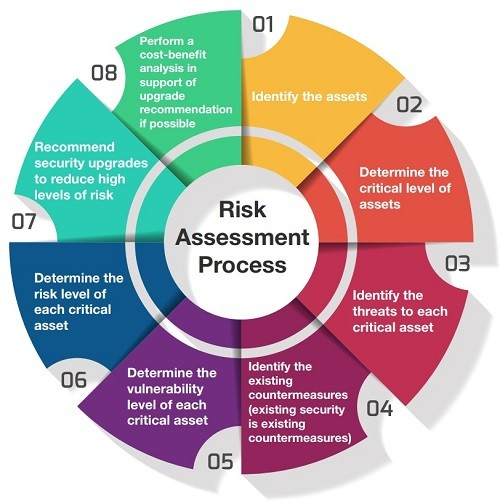
8 Essential Components Every Dynamic Risk Assessment Must Have
1. Situation Evaluation
Situation evaluation involves analyzing the current environment and operational conditions to identify the current state of risks. It provides a baseline against which you can measure future changes and threats.
Implement systems and tools that continuously monitor your operational environment, such as:
- Network Monitoring Tools – Keep an eye on your network traffic and performance and alert you to any unusual activity that might suggest a security breach or equipment failure.
- Intrusion Detection Systems (IDS) – Designed to detect unauthorized access or strange behaviors by analyzing traffic patterns and matching them to known attack signatures.
- Cybersecurity Analytics Platforms – Analyze data from your cybersecurity systems to spot potential threats or vulnerabilities and provide insights based on both historical and real-time data throughout your network.
2. Asset Inventory
Develop a detailed inventory that includes physical assets, software applications, digital data, and network resources. Each asset should be cataloged with information on its location, responsible personnel, and role in business operations.
You can also employ automated asset discovery tools that continuously scan your network and update the asset inventory in real time. It is especially useful for tracking digital assets, such as virtual machines or cloud services, that can change frequently.
3. Vulnerability and Security Gap Assessment
This component zeroes in on any gaps in security measures, systems, and processes that could leave room for breaches or other security incidents. For example, the theft of 10.6 million MGM customer records in September 2023, or the $51 million dollar ransom demand made by the Dark Angels hacking group to Johnson Controls in exchange for decrypt keys and deletion of stolen data.
Use automated vulnerability scanning tools that frequently scan your networks and systems for known vulnerabilities. Keep your scanners up-to-date with the latest definitions and configure them to perform scans at regular intervals. Schedule regular penetration tests to simulate attacks on your systems and identify vulnerabilities and the potential impact of an exploit in a controlled environment.
4. Cyber Risk Prioritization
Cyber risk prioritization sorts identified risks based on their likelihood and potential impact, enabling your MSP/MSSP to focus resources and security measures on your clients’ most critical threats first.
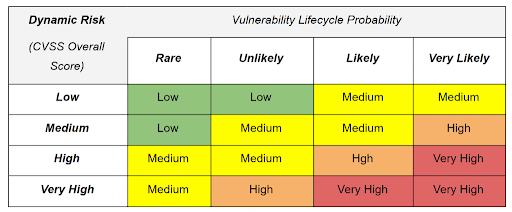
Establish a clear risk matrix for evaluating the severity and likelihood of each cyber threat. These criteria should be based on factors such as the potential financial loss, impact on MSP/MSSP business operations, legal implications, and effect on reputation.
Secondly, you can leverage threat intelligence platforms to gather real-time data about emerging threats and use the information to continually reassess and reprioritize risks based on the current threat landscape.
5. Impact of Data Losses and Data Breaches
This aspect of a DRA analyzes the potential consequences of data breaches and losses, including financial, reputational, and regulatory impacts. Understanding impact allows you to gauge the severity of different types of data breaches and plan mitigation strategies accordingly.
Create detailed scenarios of possible data breaches and losses to understand the range of potential impacts. These scenarios should consider factors like the types of data affected, the extent of the breach, and how sensitive the data is.

Ensure that the impacts of data breaches are integrated into business continuity planning for your clients – including specific recovery steps and strategies to mitigate the effects of data losses.
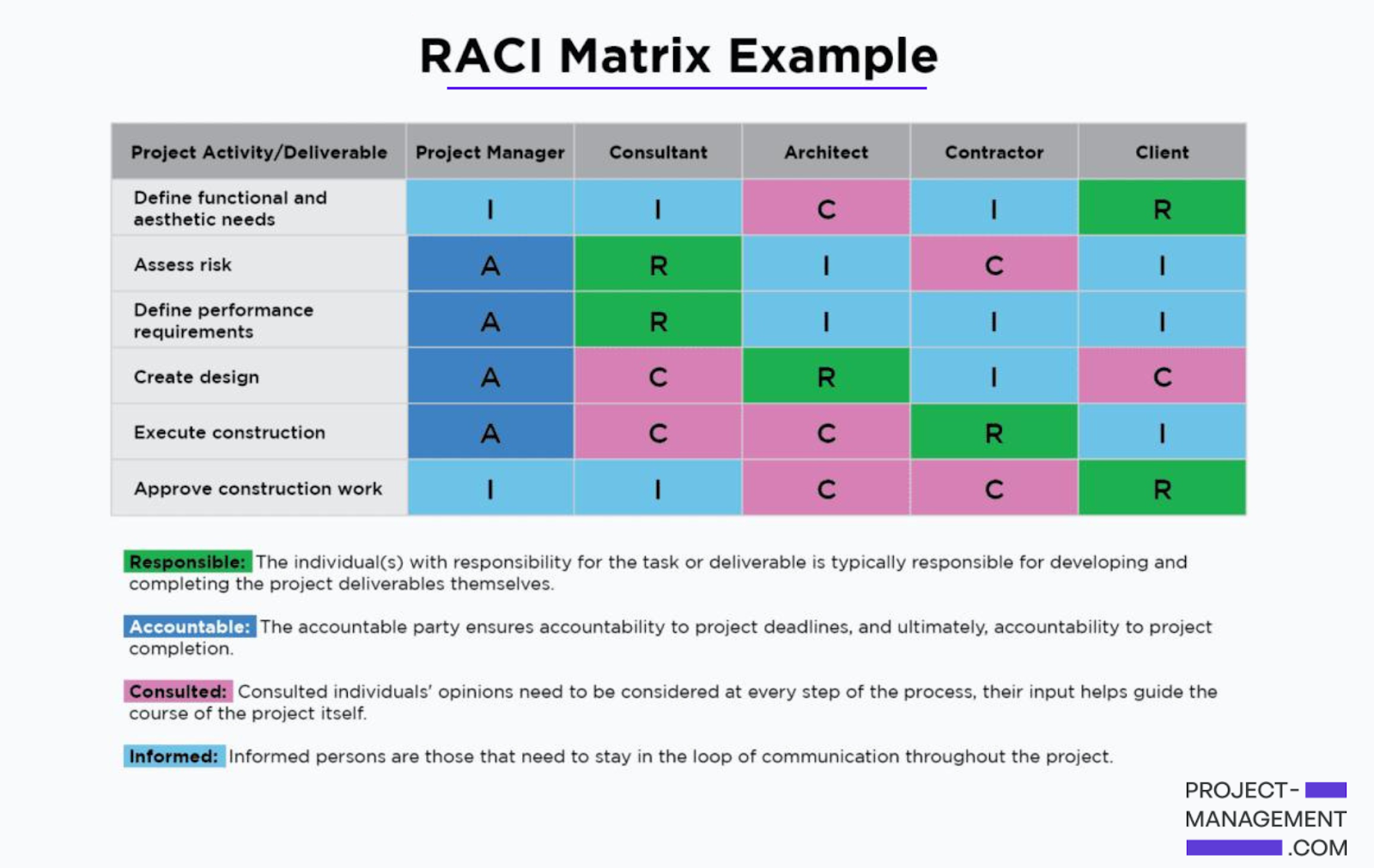
6. Identifying Roles and Responsibilities
You can clearly set out who manages different aspects of risk within your MSP/MSSP, enabling every team member to understand their specific tasks related to risk assessment tools, management, and response.
Create a RACI (Responsible, Accountable, Consulted, and Informed) matrix to delineate roles and responsibilities across different teams and departments. It should include:
- Who is responsible for monitoring threats.
- Who makes intervention decisions, and who implements those interventions.
Establish clear communication channels and protocols so everyone knows how and when to report risks and how updates and decisions are communicated within the team.
7. Resource Allocation
Resource allocation within the context of dynamic risk assessments involves strategically distributing organizational resources such as personnel, technology, and financial investments to areas that are most vulnerable or at greatest risk. You can:
- Assess which areas of your operation are at the highest risk of disruption or attack.
- Draw on data from your ongoing situation evaluations to pinpoint these high-risk zones.
- Allocate resources towards training and skill development for your staff to ensure they are equipped to handle the latest risk scenarios.
- Regular training sessions and updates on new threats and mitigation strategies are crucial.
8. Continuous Improvement and Feedback Loop
The continuous improvement and feedback loop is about refining and enhancing the assessment process itself. It enables your MSP/MSSP to learn from past incidents and responses, better preparing you for future clients’ challenges.
Establish clear channels for collecting feedback from all relevant stakeholders, including security teams, IT staff, management, and end-users. It could be in the form of regular meetings, surveys, or automated feedback tools embedded in your security systems. Regularly analyze the data collected from these feedback mechanisms to identify patterns, successes, and areas for improvement. Then, you can use this analysis to understand what is working and what isn’t.
Consider this scenario: Your dynamic risk assessment initially failed to recognize risks associated with a cloud-based infrastructure. A security incident highlighted the need for a more thorough assessment of potential cloud misconfigurations. As part of the continuous improvement loop, you can take corrective action to invest in targeted cloud security training and specialized tools to thoroughly scan and monitor cloud environments and misconfigurations.
How Cynomi Redefines Dynamic Risk Assessments
Dynamic risk assessments are not just a component of cybersecurity strategy – they are the backbone of proactive, informed, and effective security management. By incorporating up-to-date information, these assessments enable MSP/MSSPs to remain agile, boost operational flexibility, and speed up response times while keeping your end clients cyber resilient and compliant.
Not sure where to start setting up a dynamic risk assessment for your clients? The Cynomi vCISO platform supports risk assessment and audit processes with dynamic questionnaires and built-in scans to uncover critical vulnerabilities in externally visible IPs and URLs, including ports, protocols, encryption, and websites. The platform also provides internal scanning functionality as well as the ability to upload third-party scans, all of which are integrated into one holistic posture assessment and a prioritized remediation plan.
Cynomi redefines how MSP/MSSPs conduct dynamic risk assessments, enabling you to offer top-tier vCISO services efficiently with the resources you currently have. Cynomi does more than just pinpoint security gaps – it also helps you showcase and upsell the essential services and products needed to close those gaps and significantly improve your clients’ security posture.