
When a vendor’s system is compromised, the ripple effects can devastate hundreds, even thousands, of companies. It’s a chain reaction—one vulnerability in a supplier’s infrastructure can lead to compromised data, halted operations, and breaches that spread like wildfire. The risk isn’t just theoretical.
In 2023 alone, there was a 70% increase in attacks executed using Remote Monitoring and Management (RMM) tools, with threat actors leveraging these platforms to gain unauthorized access to endpoints.
An organization is only as secure as its weakest link in the supply chain. But what exactly makes a vendor risk assessment effective, and how can MSPs/MSSPs ensure clients aren’t left vulnerable by third-party oversights?
What is a vendor risk assessment?
A vendor risk assessment is a structured process for evaluating a third-party provider’s security practices, systems, and operational stability. It’s essentially a deep dive into whether a vendor meets the necessary security and compliance standards to work with an organization. MSPs/MSSPs can provide a vendor risk assessment on behalf of their clients to help third-party security and compliance.
Modern businesses are interdependent. From cloud services and SaaS platforms to hardware suppliers and data processors, almost every company relies on vendors. However, those partnerships introduce risks that aren’t always obvious until it’s too late, hence the need for a vendor risk assessment.
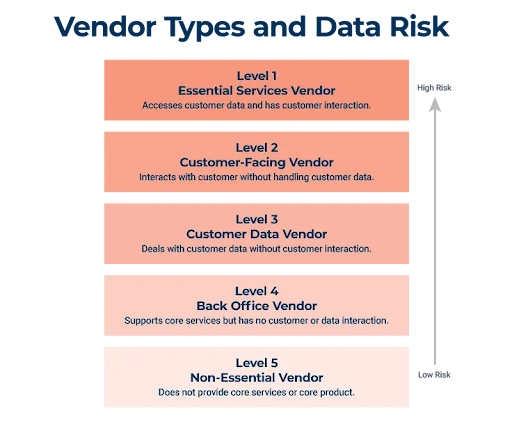
How does a vendor risk assessment work?
A vendor risk assessment workflow evaluates a vendor’s security protocols, regulatory compliance, and operational reliability. It includes reviewing their security policies, incident response plans, and history of breaches.
Here’s a simplified vendor risk assessment workflow:
- Identify Vendor Dependencies: Map out which vendors are critical to your business. The more crucial their role, the deeper the assessment.
- Evaluate Security Posture: Review the vendor’s encryption standards, firewall policies, vulnerability management, and incident response capabilities.
- Check Compliance: Ensure they meet relevant regulations like GDPR, HIPAA, or PCI-DSS.
- Assess Operational Risk: Check if they have redundancy and backup systems to ensure continuity during an outage or attack.
- Score the Risks: Based on the findings, assign a risk score to prioritize mitigation strategies or determine whether the vendor is an acceptable risk.
4 Critical Categories of Vendor Risk
While no vendor relationship is without risk, here are the categories that deserve the most attention.
| Risk Category | Description | Key Questions |
| Cybersecurity Risk | If a vendor has access to sensitive data or systems, a breach on their side can directly impact your organization. Review encryption, firewalls, patch management, and incident response capabilities. | How fast do they address vulnerabilities? Do they have real-time threat detection and containment in place? |
| Operational Risk | A disruption in essential services like cloud storage or software can cripple operations. Check disaster recovery, business continuity plans, redundancy, and uptime. | Do they have redundancy and a strong uptime record? Are their business continuity plans tested? |
| Compliance Risk | Non-compliance with regulations like GDPR, NIS2, or HIPAA can lead to fines and damage trust. Ensure the vendor meets necessary standards and holds relevant certifications. | Are they regularly audited for compliance? Do they hold up-to-date certifications for relevant regulations? |
| Reputational Risk | A vendor’s failure can tarnish your reputation. If they experience a breach or major issue, it may reflect on your client’s organization and impact public perception. | How closely is your brand tied to theirs? Could their failure impact your public image? |
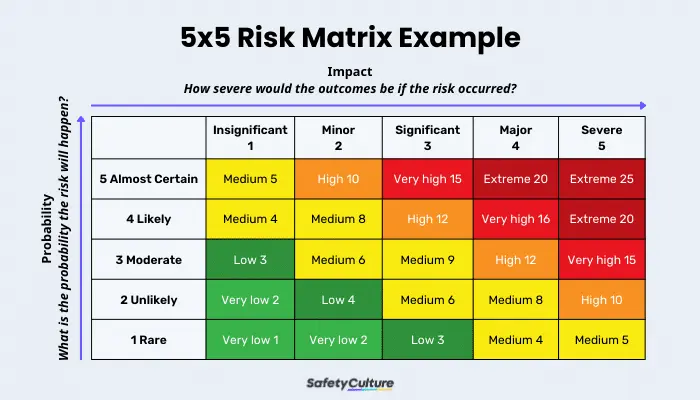
How to Calculate Vendor Risk
Calculating vendor risk isn’t about gut feelings—it’s about measurable factors determining how much exposure a vendor introduces to your organization. Here are the steps to calculate vendor risk.
- Categorize Vendors by Criticality: Not every vendor requires the same level of scrutiny. Categorize vendors into tiers based on how critical they are to your client’s operations and the sensitivity of the data they handle.
- Use a Risk Scoring Framework: Adopt a scoring framework to evaluate vendors based on multiple risk factors, such as financial stability, compliance, data governance, and history of breaches. A simple risk management table or scorecard can provide a quick overview of vendors with the highest risk.
- Identify High-Risk Areas: Focus on high-risk areas such as how vendors manage their own cybersecurity protocols, what data they have access to, and what contingencies they have in place to deal with incidents.
- Perform Continuous Monitoring: Vendor risk isn’t static. Continually monitor vendors to ensure their security posture remains robust and aligned with your client’s risk tolerance.
8 Essentials Every Vendor Risk Assessment Must Contain
1. Vendor Security Policies
Security policies are where it all begins. If a vendor doesn’t have robust internal security policies, they’re a liability waiting to happen. But don’t settle for vague assurances on behalf of your clients—ask for specifics.
- How do they manage access control?
- What encryption standards do they use?
- Are their data retention policies aligned with industry best practices?
You want to see documented policies that detail everything from how they secure endpoints to how they handle data deletion. If their policies are incomplete or outdated, it’s a red flag that they’re not taking cyber risk and security seriously.
2. Incident Response Plan
It’s not a matter of if a breach will happen but when. That’s why the vendor’s incident response plan is critical.
- How quickly can they detect and react to a breach?
- Do they have the necessary tools and expertise to contain the damage before it spreads?
You’re looking for a detailed, tested response plan that includes clear roles, responsibilities, and workflows. The plan should specify how incidents are logged, escalated, and resolved.
3. Compliance Certification
Regulations like SOC 2, ISO 27001, and PCI-DSS aren’t just acronyms to throw around. They represent hard evidence that a vendor has their act together when it comes to security. Certifications show that the vendor has undergone rigorous audits and adheres to specific security standards.
But don’t stop at checking for certifications in the vendor risk assessment—make sure they’re up-to-date and relevant to your client’s industry. If a vendor can’t produce these certifications, you’re rolling the dice on their compliance status, and that’s a risk no business can afford.
4. Risk Scoring
Not all risks are created equal, and neither are vendors. A solid risk scoring framework helps you quantify the level of risk each vendor presents. It isn’t just about assigning a number—it’s about understanding where a vendor’s weak spots are and how likely they are to impact your client’s organization.
A risk score simplifies decision-making, allowing you to prioritize which vendors need deeper scrutiny or immediate risk mitigation. Whether they’re handling your client’s core infrastructure or just a secondary service, a risk score helps you measure their potential impact.
5. Business Continuity Plan
If a vendor goes down, you need to know they have a plan in place to keep things running. That’s where a business continuity plan (BCP) comes in as part of your vendor risk assessment. Evaluate how they plan to maintain operations during an outage, natural disaster, or cyberattack.
Do they have redundancy built into their infrastructure? Is there a tested backup plan for their critical systems and services? The absence of a solid BCP is a sign that even a minor disruption could become a major operational risk for your client’s business.
6. Third-Party (or Fourth-Party) Risk
Vendor risk doesn’t stop with the vendor. The vendor is likely relying on other third parties, and any gaps in their security practices will come back to haunt your client. This is often called “fourth-party risk.” A breach in the vendor’s supply chain could have just as much impact on your client’s operations as a direct breach of the vendor itself.
Make sure the vendor is vetting their suppliers and has stringent security requirements in place for subcontractors and service providers. If they’re lax in managing their third parties, your client will be exposed to risks they never accounted for.
7. Financial Health Check
A vendor’s financial stability is just as important as their technical prowess. After all, if they experience financial distress, your client could be left scrambling for replacements—or worse, face service interruptions. Look at their financial statements and key indicators of stability, such as revenue growth, debt levels, and profitability. Are they in a position to provide long-term support? If a vendor is financially unstable, their service reliability could drop, creating gaps at critical moments.
8. Data Handling Practices
The way a vendor manages your data is a direct reflection of how they value security. You want to know exactly how they store, transfer, and dispose of your data. Are they encrypting data at rest and in transit? Do they have strict policies around data access and deletion? If they handle sensitive or regulated data, this becomes even more critical. Vendors should have transparent, documented practices that align with your organization’s data security requirements. Anything less puts your data—and your reputation—at risk.
Bringing It All Together: Vendor Risk Assessments with Cynomi
Managing vendor risk at scale can feel overwhelming. The sheer number of vendors most organizations rely on means a manual approach to risk assessment is impractical. This is where Cynomi’s AI-powered vCISO platform comes in. Cynomi automates the process of conducting risk assessments, allowing MSPs and MSSPs to provide tailored, comprehensive risk assessments for multiple clients at scale. By leveraging Cynomi, you save time and gain a deeper, real-time understanding of the unique risk profile of each client.
Request a demo to learn how our platform can help you automate and optimize vendor risk assessments, enabling you to deliver this service at scale to your client base.
