A cybersecurity risk assessment template is a structured, repeatable framework that guides organizations through identifying, analyzing, and prioritizing risks to their data, systems, and digital operations. Rather than starting from scratch or relying on scattered spreadsheets, it provides a consistent way to evaluate threats, document vulnerabilities, and determine how to best mitigate them.
Unlike traditional IT risk assessments, which tend to focus narrowly on technical systems, a cybersecurity risk assessment goes broader. It encompasses not only infrastructure and applications but also human factors, policies, and third-party dependencies – everything that can impact an organization’s security posture.
This article explores the core components of an effective cybersecurity risk assessment template and explains how to use it.
Why Cybersecurity Risk Assessment Templates Matter
For MSPs and MSSPs managing multiple clients, manually assessing each environment from scratch is unsustainable. A cybersecurity risk assessment template brings structure and speed to this process, transforming complex evaluations into repeatable, scalable workflows.
The template provides a centralized, data-driven method to identify vulnerabilities, score risk levels, and define mitigation priorities. That consistency not only improves accuracy but also strengthens client trust. Every assessment looks professional, aligns with recognized frameworks, and clearly shows progress over time.
For service providers, this shift delivers tangible business outcomes:
- Efficiency at scale – Reduce assessment time from days to hours by standardizing questions, scoring models, and report formats.
- Faster onboarding – Apply a proven structure to new clients immediately, without re-creating documentation or workflows.
- Clear, quantifiable results – Leverage uniform scoring and risk matrices to benchmark and track improvement.
- Compliance readiness – Map findings directly to frameworks like NIST, ISO 27001, SOC 2, HIPAA, and CIS Controls, eliminating manual cross-referencing.
- Client confidence – Deliver reports that highlight risk exposure and remediation progress in an easy-to-digest visual format.
Key Elements of an Effective Cyber Risk Assessment Template
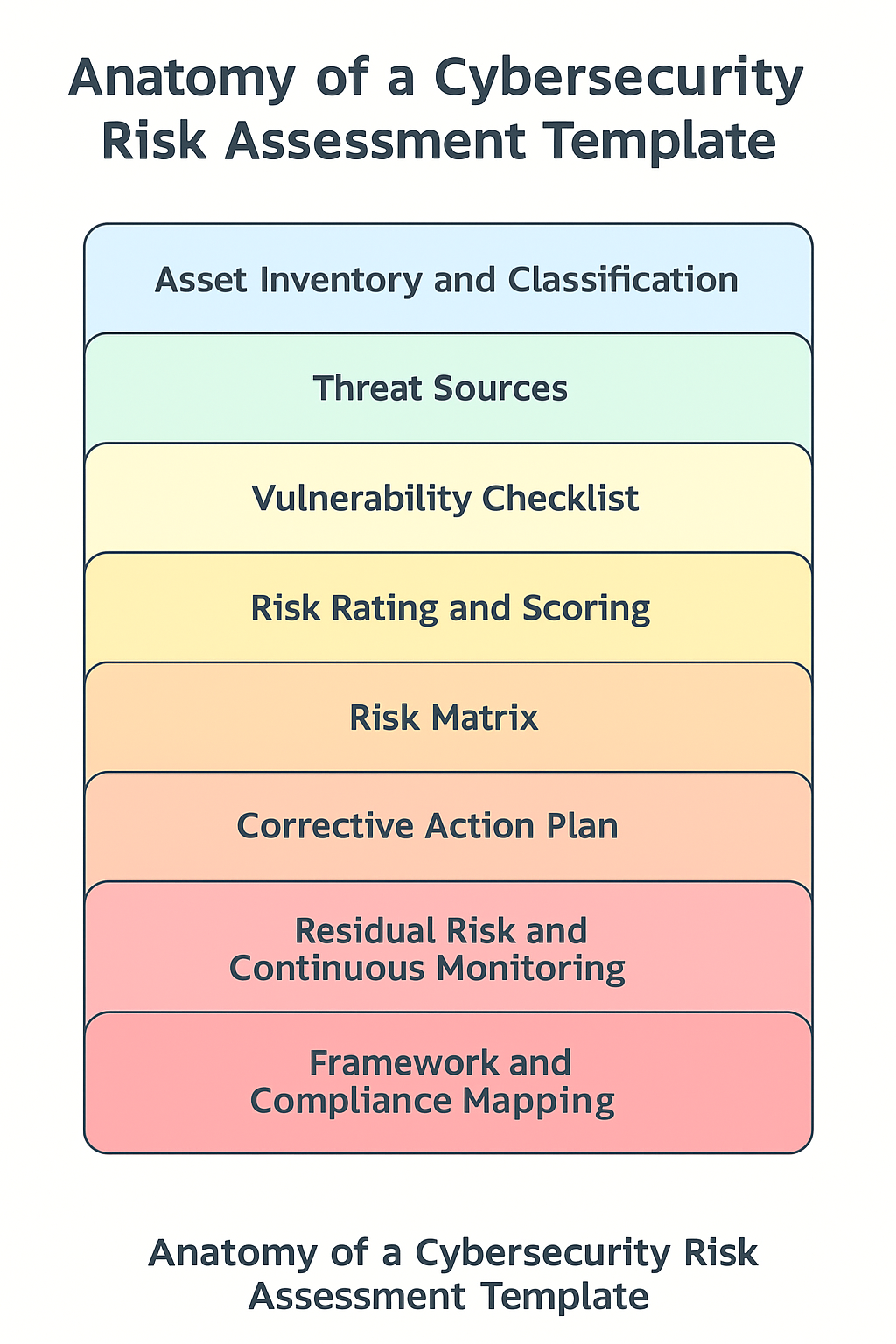
A strong cyber risk assessment template turns complex cybersecurity analysis into a clear, structured process. It ensures that every important element, from asset inventory to remediation, is captured in one consistent format. Download our full Risk Assessment Template.
Whether you’re an MSP performing assessments for multiple clients or an internal security team reviewing your own environment, these are the essential components every effective cybersecurity risk assessment template should include:
1. Asset Inventory and Classification
Every risk assessment starts with knowing what you’re protecting. This section lists all critical assets: data, devices, software applications, servers, networks, and even users. Including asset classification (e.g., critical, important, non-critical) helps prioritize resources and focus the rest of the assessment on what matters most.
2. Threat Sources
Identify the potential origins of attacks or incidents, both malicious (hackers, insiders, ransomware groups) and non-malicious (system failures, misconfigurations, human error). Mapping each threat to relevant assets provides context for later risk scoring.
3. Vulnerability Checklist
A practical cybersecurity risk assessment template includes a checklist of vulnerabilities, from outdated software and weak passwords to missing policies or misconfigured firewalls. This makes the evaluation consistent across clients and reduces human bias.
4. Risk Rating and Scoring
Once threats and vulnerabilities are linked to assets, each risk is rated by likelihood and impact. Many templates use a 1-5 scale or a qualitative matrix (e.g., low/medium/high). The resulting score quantifies the organization’s exposure and highlights areas requiring urgent attention.
5. Risk Matrix
Visualizing risk is key for communication. A color-coded matrix (often 5×5) maps each risk by likelihood and impact, helping stakeholders instantly grasp which issues pose the greatest danger. This matrix becomes a powerful discussion and reporting tool.
6. Corrective Action Plan
The goal of any cybersecurity risk assessment is to identify risks as well as address them. This section outlines the remediation strategy for each risk, including:
- Recommended control or mitigation action
- Assigned owner or responsible team
- Timeline and priority level
- Status tracking (planned, in progress, completed)
Using standard risk handling options: accept, mitigate, transfer, or avoid, keeps decision-making consistent.
7. Residual Risk and Continuous Monitoring
After controls are implemented, reassess the remaining risk to determine whether it’s now acceptable. Including this section helps demonstrate continuous improvement and compliance alignment over time.
8. Framework and Compliance Mapping
A valuable cybersecurity risk assessment example will include a mapping table that connects each identified risk to relevant regulatory or framework requirements. For example, linking “unencrypted backups” to NIST PR.DS-1 or ISO 27001 A.10.1.1 ensures assessments support compliance documentation and audit readiness.
Cybersecurity Risk Assessment Template Examples
There’s no single, universal cybersecurity risk assessment template that fits every organization or use case. While the basic structure: identifying assets, evaluating threats, and planning mitigation, remains consistent, templates differ in purpose, scope, and required detail depending on the frameworks and industries they’re built for.
The terminology, data fields, and evidence requirements vary between organizations focused on compliance readiness, technical defense, or vendor oversight. Understanding these differences helps you choose or adapt the right cybersecurity risk assessment template for your specific needs.
When selecting or designing your cybersecurity risk assessment template, consider these factors:
- Your primary goals, such as compliance, technical protection, or third-party assurance
- The frameworks you must align with (NIST, ISO, HIPAA, SOC 2)
- The audience – whether it’s an internal IT team, auditors, or executive stakeholders
- The desired frequency and scalability – from one-time engagements to continuous monitoring
Below are three common cybersecurity risk assessment template examples to demonstrate how templates can differ in structure and focus:
1. NIST Focused Cybersecurity Risk Assessment Template
This type of cybersecurity risk assessment example is based on the NIST Cybersecurity Framework (CSF) and SP 800-30 guidelines, widely adopted across government and regulated industries. It emphasizes structured categorization and alignment with security controls, and works best for organizations that must demonstrate regulatory compliance and maintain traceable, auditable documentation.
In this case, the template typically includes:
- Categorization of systems and assets by criticality and sensitivity
- Mapping to NIST CSF functions: Identify, Protect, Detect, Respond, Recover
- Control assessment fields tied to NIST 800-53 control families
- Likelihood and impact scoring tied to defined impact levels (low, moderate, high)
- Documentation of residual risk and corrective actions
- Continuous monitoring and a periodic reassessment schedule
2. IT and Infrastructure Focused Risk Assessment Template
An IT-focused cyber risk assessment template zeroes in on technology assets: servers, endpoints, networks, and cloud environments. It’s a practical tool for internal IT teams or service providers who need to identify, track, and prioritize risks tied directly to the technical environment. It supports continuous technical risk management and helps MSPs/MSSPs quickly show clients where technology gaps exist and how they’re being addressed.
This template generally includes:
- Asset and configuration inventories for hardware, software, and cloud services
- Threat categories such as malware, configuration drift, access misuse, or data loss
- Vulnerability tracking linked to patching status or scanner results
- A business impact column to weigh downtime, data compromise, or service interruption
- Control ownership and remediation tracking fields
- Optional integration with asset discovery or vulnerability management tools
3. Compliance and Third-Party Focused Risk Assessment Template
Many organizations today must evaluate both internal risks and those stemming from their vendors, partners, or cloud providers. A compliance-oriented cybersecurity risk assessment extends the core template with sections designed to manage regulatory and third-party exposure. This type of assessment is often used by MSPs and MSSPs offering managed compliance or vendor risk services, where demonstrating due diligence is just as important as maintaining technical security.
This version often includes:
- Framework mapping for SOC 2, ISO 27001, HIPAA, or PCI DSS controls
- Fields for vendor name, data access level, and criticality tier
- Questionnaires covering certifications, SLAs, and breach history
- Risk rating scales specific to third-party performance and data protection
- Mitigation tracking with shared responsibilities between internal and external stakeholders
- Evidence attachments for audits and compliance reports
How to Get the Most from Using A Cybersecurity Risk Assessment Template
A cybersecurity risk assessment template is a framework for continuous improvement. To maximize its impact, it needs to become part of your regular cybersecurity workflow, not a one-off project. Here’s how to make it work in practice.
Integrate It Into Your Existing Processes
Don’t treat the template as a standalone document. Embed it within your onboarding, audit-readiness, or managed security review processes. For MSPs and MSSPs, using the same cyber risk assessment template across all clients ensures a consistent experience and comparable results.
Tailor It to Your Frameworks and Industries
Different industries face different compliance obligations. Customize the cybersecurity risk assessment template by aligning its controls and scoring fields with the frameworks most relevant to your clients. This simple adjustment ensures assessments directly support your compliance deliverables.
Use It as a Communication Tool
A well-structured cybersecurity risk assessment helps bridge the gap between technical and business stakeholders. Visual elements such as the risk matrix and scoring summaries make it easier to discuss priorities with executives and boards, turning technical findings into business-level insight.
Leverage It for Recurring Value
Rather than performing one assessment and archiving it, revisit and update the template regularly. Comparing results over time highlights trends, measures risk reduction, and proves the ROI of ongoing cybersecurity investments.
Automate Where Possible
Manual data entry slows everything down. Automating asset discovery, scoring, and reporting can reduce human error and accelerate results. Modern platforms like Cynomi take the same cybersecurity assessment template logic and digitize it, transforming a static spreadsheet into a dynamic, living system for continuous risk management.
By applying these practices, your cybersecurity risk assessment template becomes much more than documentation, evolving into a strategic mechanism for standardization, transparency, and growth.
How Cynomi Digitizes and Automates Cybersecurity Risk Assessment Templates
Completing a cybersecurity risk assessment template manually can take days, especially when managing multiple clients, tracking updates, and aligning results with frameworks like NIST or ISO 27001. Cynomi, built specifically for MSPs and MSSPs, transforms this process.
Cynomi’s vCISO platform automates and elevates every part of the traditional cyber security risk assessment template workflow. Instead of working through static spreadsheets, service providers use an intelligent, AI-powered platform that acts as a CISO Copilot, guiding users through assessments, scoring, reporting, and remediation planning, all within a single dashboard.
Here’s how Cynomi streamlines and enhances the process:
1. Automated Risk Identification and Scoring
Cynomi automatically analyzes client environments, assets, and configurations to identify potential risks. It applies built-in scoring models to instantly calculate likelihood and impact, generating dynamic heatmaps and dashboards, replacing the manual scoring tables found in most cyber risk assessment templates.
2. Built-In Framework Alignment
The platform is pre-mapped to leading frameworks, including ISO 27001, SOC 2, HIPAA, and CIS Controls. Each finding in the assessment is automatically tied to relevant control categories, ensuring compliance alignment without extra manual work.
3. Instant Remediation Planning
Once risks are identified, Cynomi generates an automated corrective action plan, prioritized by severity and impact. Each task includes guidance based on seasoned CISO knowledge, ensuring that even less experienced team members can deliver expert-level remediation recommendations.
4. Continuous Monitoring and Updates
Unlike static templates, Cynomi maintains a living risk register that evolves with each client environment. Changes in configurations, policies, or compliance requirements automatically trigger reassessments and updated risk scores, helping service providers deliver continuous visibility.
5. Multi-Client Management and Reporting
Through its multi-tenant architecture, Cynomi lets providers manage all client assessments in one place. Standardized dashboards, client-specific reports, and automated updates make it easy to scale without sacrificing quality or accuracy.
Most organizations should conduct a cybersecurity risk assessment at least once a year, or even more frequently if they experience major operational or infrastructure changes.
An IT risk assessment focuses primarily on technology systems: servers, endpoints, and network components. A cybersecurity risk assessment, by contrast, has a broader scope. It includes human behavior, policies, data governance, and third-party risks in addition to technical factors.
No single template fits every need. A healthcare provider aligning with HIPAA requires different evidence and controls than a SaaS company following SOC 2. The key is to start with a flexible cyber risk assessment template and customize it based on frameworks, data types, and compliance requirements.
A well-structured cybersecurity risk assessment template maps risks directly to framework controls such as NIST CSF, ISO 27001, HIPAA, or PCI DSS. This ensures every identified risk corresponds to a compliance requirement, simplifying audits and demonstrating ongoing due diligence.
For service providers, a standardized cybersecurity assessment template helps deliver consistent, measurable results across all clients.
Automation removes the manual burden of data entry, scoring, and reporting. With AI-powered tools like Cynomi, providers streamline workflows, reduce inconsistencies, and maintain continuous visibility into evolving risks. Automated scoring and framework mapping (NIST, ISO 27001, etc.) keep assessments current, helping MSPs and MSSPs serve more clients efficiently while maintaining expert-level quality.