Software platforms that help organizations identify, assess, and manage cybersecurity risks through structured, automated, and repeatable processes.
They provide visibility into threats, streamline compliance, and enable data-driven decisions that strengthen security posture and business resilience.
Key capabilities include threat and vulnerability analysis, risk scoring and dashboards, framework mapping, remediation planning, continuous monitoring, and automated reporting.
Top solutions include Cynomi, LogicManager, Resolver, RiskWatch, Archer, AuditBoard, OneTrust, Riskonnect, ProcessUnity, and MetricStream. Each supports a different stage of maturity in cyber and enterprise risk management.
Cynomi is purpose-built for MSPs and MSSPs, automating risk and compliance management at scale. Acting as a CISO Copilot, it standardizes workflows, generates action plans, and enables service providers to deliver consistent, expert-level cybersecurity services efficiently.
As cyber threats grow more sophisticated, organizations and managed security service providers (MSSPs) increasingly rely on risk management solutions and tools to efficiently identify, assess, and mitigate vulnerabilities. In this guide, we’ll explain what risk management software is, explore its key advantages and capabilities, and highlight the top risk management tools for 2025 to help you choose the right solution for your needs.
What Are Cyber Risk Management Platforms?
Modern cybersecurity operations rely on structure and repeatability. Cyber risk management platforms provide a centralized way to identify, analyze, and prioritize risks across systems, assets, and business units. They replace fragmented spreadsheets with standardized, data-driven processes that ensure every risk is documented, measured, and tracked.
With cyber risk management software, organizations gain a single environment to assess vulnerabilities, assign risk scores, map controls to frameworks, and monitor the status of mitigation activities. The result is a consistent, auditable process for maintaining a clear view of the organization’s exposure.
For enterprises, these platforms centralize risk and compliance in one system, enabling teams to manage multiple frameworks through a shared control library and unified workflows. For MSPs and MSSPs, they also enable scalable management of multiple clients, ensuring uniform methods, centralized oversight, and structured reporting across accounts.
Many cyber risk assessment platforms incorporate automation and analytics to support ongoing evaluation, updating risk registers as new data emerges, and simplifying reporting for internal or client use.
In short, risk management platforms form the backbone of a mature cybersecurity program, turning risk identification and documentation into a systematic, repeatable discipline that supports governance and informed decision-making.
Key Advantages of Using Cyber Risk Management Platforms
Using risk management platforms transforms how organizations and service providers handle cyber risks. These platforms move teams from reactive, manual processes to proactive, data-driven management, helping them identify what matters most, act faster, and demonstrate measurable improvement in their security posture.
Below are some of the core advantages organizations and service providers gain from using dedicated risk management software:
1. Improved Visibility Into Risks
Centralized dashboards consolidate risk data from multiple systems, giving teams a clear view of their organization’s threat landscape. This visibility makes it easier to spot high-impact risks, track their status, and communicate exposure levels across departments or clients.
2. Faster Mitigation and Response
Automation streamlines risk scoring, prioritization, and task assignment, reducing the time between identifying a vulnerability and resolving it. By standardizing workflows, organizations can respond faster and prevent minor issues from escalating into costly incidents.
3. Simplified Compliance and Reporting
Risk management software aligns security controls with compliance frameworks such as ISO 27001, NIST, SOC 2, and HIPAA. It automates evidence collection and reporting, ensuring that audit preparation and regulatory updates are always current and consistent.
4. Strategic Cybersecurity Planning
When risk data is presented through clear metrics, security becomes a business enabler rather than an obstacle. These platforms help leadership teams connect risk exposure to business objectives, prioritize investments, and allocate resources based on real impact.
5. Executive-Ready Dashboards and Insights
Boards and executives often need quick, understandable overviews rather than technical deep dives. Risk management platforms offer visual dashboards that translate complex security metrics into business language, supporting informed decisions, transparency, and client communication.
Key Capabilities of Cyber Risk Management Platforms
Naturally, risk management software platforms vary in their capabilities, features, depth, and functionality. The most effective solutions combine automation, analytics, and visibility to give organizations and the MSPs or MSSPs supporting them a comprehensive, real-time view of cyber risk.
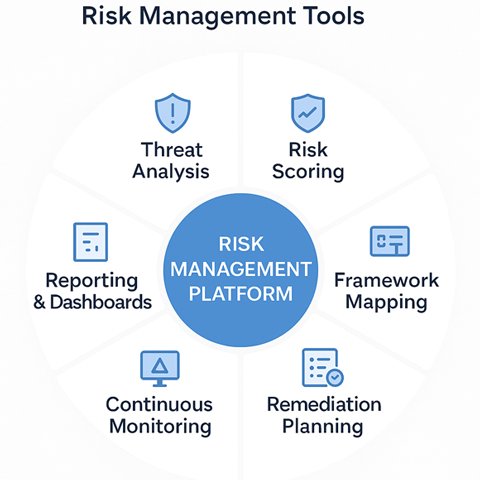
Below are the key capabilities to look for when evaluating a risk management platform:
1. Threat and Vulnerability Analysis
A strong foundation of any platform is its ability to identify and classify potential threats and vulnerabilities. Effective tools aggregate data from scanners, asset inventories, and external threat feeds to provide a clear picture of where exposures exist and how they relate to business-critical assets.
2. Risk Scoring and Dashboards
Modern platforms quantify risk using scoring models that assess both likelihood and impact. Visual dashboards display real-time risk posture across assets, departments, or clients, making it easier to prioritize remediation and communicate trends.
3. Policy and Framework Mapping
Compliance alignment should be built in. The best risk management platforms automatically map risks, controls, and mitigation activities to frameworks such as NIST, ISO 27001, SOC 2, HIPAA, and PCI DSS. This ensures that every control is connected to the right standard and that gaps are easy to identify.
4. Risk Treatment and Remediation Planning
Once risks are identified and scored, the platform should guide users through treatment planning, defining actions, assigning owners, and tracking progress. Clear remediation workflows enable accountability and transparency across technical and business teams.
5. Continuous Monitoring and Alerts
Top platforms don’t stop at one-time assessments. They enable continuous monitoring of assets and vulnerabilities, automatically updating risk scores and notifying stakeholders when changes occur, ensuring real-time awareness of new threats or compliance deviations.
6. Automated Reporting and Documentation
Generating reports for leadership, auditors, or clients can be time-consuming. Automated reporting capabilities turn complex datasets into easy-to-understand visuals and summaries, saving hours of manual work while ensuring consistency and accuracy.
Advanced Capabilities (Nice to Have)
Leading risk management platforms go beyond basic risk tracking. They incorporate advanced technologies and integrations that enhance precision, speed, and scalability.
Here is a list of (very) nice-to-have advanced features:
- AI-Driven Risk Prediction
Machine learning models analyze historical and contextual data to forecast emerging risks, helping organizations address issues before they escalate. - Third-Party Risk Integration
Integration with vendor databases and TPRM modules allows organizations to assess supplier risk within the same system, ensuring a holistic view of the extended attack surface. - Scenario and Impact Modeling
Advanced analytics simulate potential incident scenarios, calculating financial or operational impact and guiding investment prioritization. - Multi-Tenant Management for MSSPs
Enables MSSPs to manage multiple client environments from one dashboard, maintaining standardized processes, aggregated reporting, and customized client portals. - API and Ecosystem Integrations
Open APIs allow seamless connectivity with vulnerability scanners, SIEM tools, ticketing systems, and cloud environments, ensuring data remains synchronized across the security stack.
Top Risk Management Solutions for 2026
Choosing the right risk management solution is essential for effectively identifying, prioritizing, and mitigating cybersecurity risks.
Below are ten leading risk management solutions for 2025 that are empowering teams to strengthen resilience and deliver measurable security outcomes.
1. Cynomi
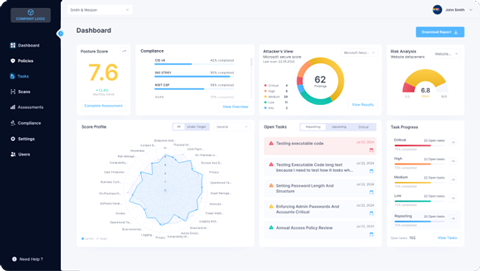
Main Features:
- AI-driven vCISO platform
- Automated risk and compliance assessments
- Framework mapping and remediation planning
- Reporting automation and progress tracking
- Multi-tenant management for MSPs/MSSPs
Best For: MSPs, MSSPs, and consultancies delivering scalable cybersecurity and compliance services.
Pricing: Contact sales for a custom quote.
The Verdict:
⭐⭐⭐⭐⭐ The leading vCISO platform for MSPs and MSSPs, Cynomi automates and standardizes cybersecurity management to efficiently scale client services.
Click to read Cynomi reviews.
2. LogicManager
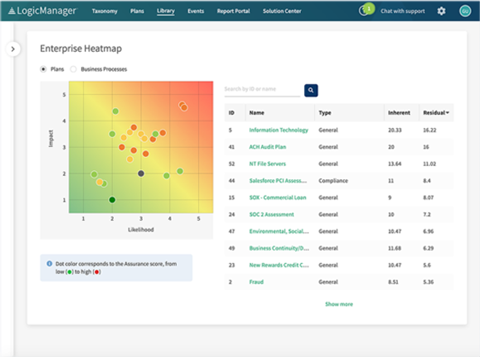
Main Features:
- Centralized GRC management
- Enterprise risk dashboards
- Workflow automation and audit trails
- Customizable control libraries
- Built-in reporting templates
Best For: Mid-size to large enterprises seeking an integrated approach to governance, risk, and compliance.Pricing: Contact sales for a custom quote.
The Verdict:
⭐⭐⭐⭐A trusted GRC platform offering structured, organization-wide visibility and streamlined compliance management.
Click to read LogicManager reviews.
3. Resolver
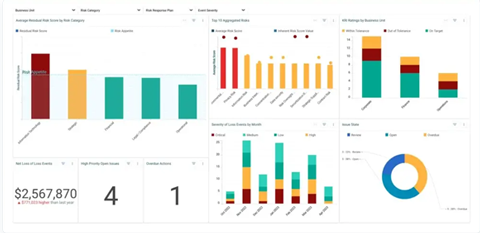
Main Features:
- Incident and risk tracking in a single, cloud-based platform
- Customizable dashboards and data visualizations
- Workflow automation and configurable approvals
- Risk heat maps and analytics for trend analysis
- Centralized reporting across risk and control domains
Best For: Large enterprises and compliance-driven organizations.Pricing: Contact sales for a custom quote.
The Verdict:
⭐⭐⭐⭐ A flexible, analytics-driven solution that unifies incident and risk data for more transparent decision-making.
Click to read Resolver reviews.
4. RiskWatch
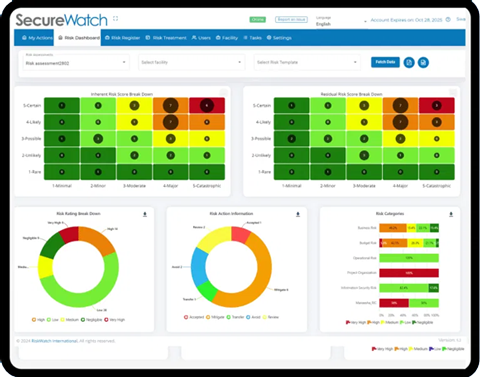
Main Features:
- Real-time risk dashboards
- Pre-built templates for frameworks like NIST, ISO, and HIPAA
- Automated risk scoring and prioritization
- Evidence management and audit tracking
- Compliance reporting tools
Best For: Highly regulated industries such as healthcare, finance, and energy.
Pricing: Contact sales for a custom quote.
The Verdict:
⭐⭐⭐ A simple, template-driven platform ideal for fast, standardized risk assessments in compliance-heavy sectors.
Click to read RiskWatch reviews.
5. Archer
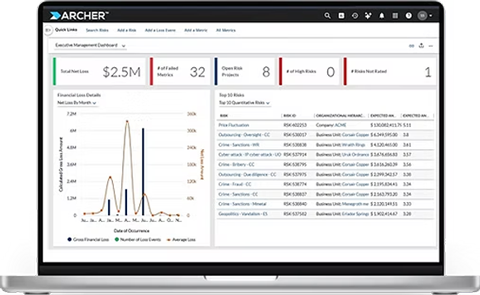
Main Features:
- Enterprise risk cataloging and register management
- Integrated risk scoring
- Governance and audit management
- Policy and compliance tracking
- Advanced reporting and analytics
Best For: Large enterprises with established GRC programs and mature risk teams.Pricing: Contact sales for a custom quote.
The Verdict:
⭐⭐⭐⭐A long-standing enterprise GRC leader known for deep configurability and broad risk management coverage.
Click to read Archer Technologies reviews.
6. AuditBoard
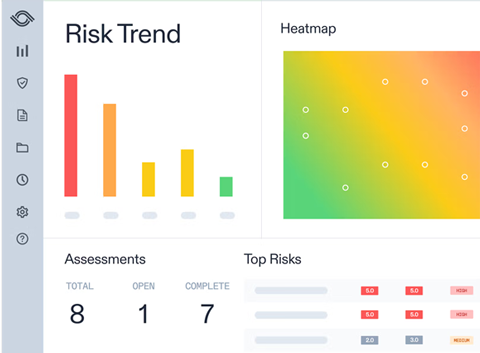
Main Features:
- Risk management and issue tracking
- Compliance and control monitoring
- Audit planning and scheduling
- Workflow automation and reporting
- Continuous risk monitoring
Best For: Mid-market to large organizations focused on audit readiness and control assurance. Its continuous monitoring capabilities make it a favorite among compliance and internal audit teams.
Pricing: Contact sales for a custom quote.
The Verdict:
⭐⭐⭐⭐ Offers a polished user experience and deep automation for audit-related risk workflows.
Click to read AuditBoard reviews.
7. OneTrust
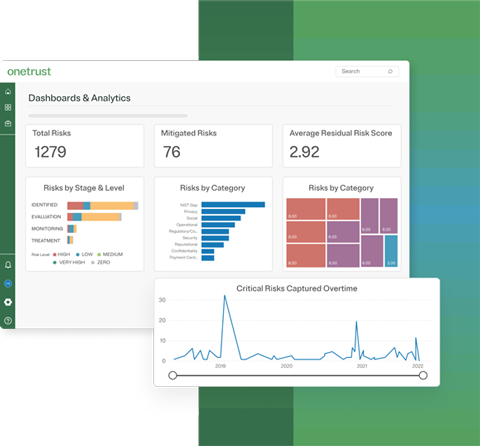
Website: onetrust.com
Main Features:
- Integrated risk and compliance management
- Privacy and data governance modules
- Third-party risk tracking
- Regulatory intelligence updates
- Automated control mapping across frameworks
Best For: Global organizations managing multiple frameworks and privacy regulations, and seeking a unified view across business and cyber domains.
Pricing: Contact sales for a custom quote.
The Verdict:
⭐⭐⭐⭐ Delivers a wide GRC portfolio that extends beyond IT risk, offering unmatched breadth for privacy, data governance, and compliance oversight.
Click to read OneTrust reviews.
8. Riskonnect
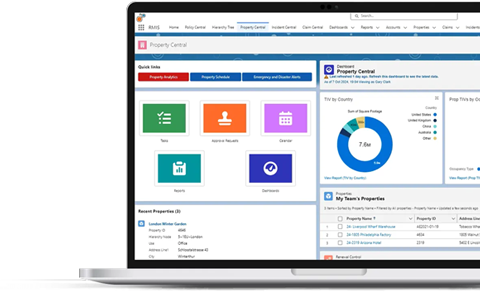
Main Features:
- Enterprise risk and compliance management
- Operational and IT risk tracking
- Claims and incident management
- Advanced analytics and reporting
- Automated workflows for remediation
Best For: Large organizations managing operational, financial, and IT risks together.Pricing: Contact sales for a custom quote.
The Verdict:
⭐⭐⭐⭐Its integration depth and strong analytics capabilities make it valuable for enterprise environments that require a unified risk ecosystem.
Click to read Riskonnect reviews.
9. ProcessUnity
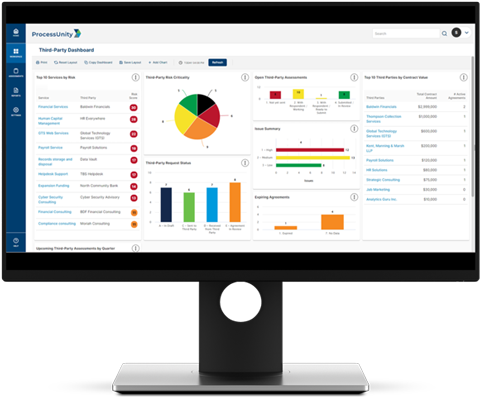
Main Features:
- Enterprise and vendor risk management
- Automated workflows and assessments
- Control and policy mapping
- Third-party monitoring and scoring
- Centralized reporting dashboards
Best For: Organizations looking to connect internal and third-party risk processes.
Pricing: Contact sales for a custom quote.
The Verdict:
⭐⭐⭐⭐A modular, scalable platform that bridges enterprise and vendor risk management for complete visibility.
Click to read ProcessUnity reviews.
10. MetricStream
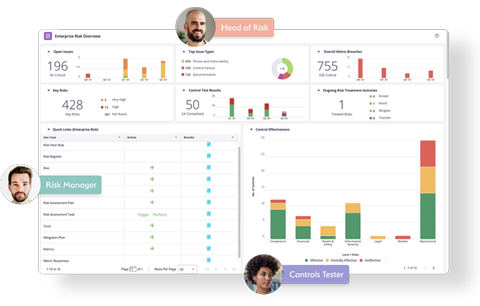
Main Features:
- Integrated GRC suite for enterprise-wide risk
- IT, operational, and compliance risk modules
- Data analytics and visualization tools
- Automated reporting and dashboards
- Regulatory and policy management
Best For: Global enterprises with complex governance and compliance structures.
Pricing: Contact sales for a custom quote.
The Verdict:
⭐⭐⭐⭐A mature GRC suite offering global organizations unified governance, risk, and compliance visibility.
Click to read MetricStream reviews.
How to Select a Risk Management Platform
Selecting the right risk management platform isn’t just about checking feature boxes; it’s about finding a cyber risk management software that fits your organization’s size, maturity, and long-term security strategy. The right choice should integrate smoothly into daily operations, scale with your needs, and deliver measurable value over time.
Here are the most important factors to evaluate before you decide:
1. Alignment With Organizational Goals
Start by defining what success looks like. Are you aiming to improve compliance readiness, streamline risk reporting, or scale managed services? The ideal platform should directly support your operational and strategic priorities, without forcing you to adapt to its structure.
2. Integration Across the Security Ecosystem
Look for a platform that connects effortlessly with your existing tools – vulnerability scanners, SIEM systems, cloud platforms, and ticketing solutions. Strong integration ensures continuous data flow and eliminates silos, creating a unified view of enterprise or client risk.
3. Depth of Insights and Reporting
Beyond dashboards, assess how well the system helps you interpret risk data. Can it generate meaningful trends, risk heat maps, and board-ready summaries? The ability to communicate risk in business terms is as critical as the data itself.
4. Framework and Control Adaptability
A good risk management platform should adapt to your regulatory environment, not the other way around. Look for flexible control libraries, multi-framework mapping, and easy customization to align with your specific industry standards and regulations.
5. Scalability and Multi-Tenant Management
For MSPs and MSSPs, scalability is a must. Multi-tenant architecture, client-level customization, and standardized workflows make it possible to deliver consistent, high-quality services across multiple customers without adding resources.
6. Usability and Onboarding Speed
Ease of use often determines adoption. Choose a cloud-based platform with intuitive workflows, guided assessments, and role-based access, allowing both experienced CISOs and junior analysts to contribute effectively from day one.
7. Total Cost of Ownership and ROI
Finally, evaluate long-term ROI, not just licensing costs. The most valuable solutions reduce manual workloads, shorten reporting cycles, and improve client engagement, resulting in measurable savings and growth opportunities over time.
How Cynomi Supports Cyber Risk Management
Cynomi enables MSPs, MSSPs, and consultancies to deliver consistent, scalable cybersecurity and risk management services without increasing headcount or complexity. Acting as a CISO Copilot, Cynomi combines automation, built-in structure, and CISO-level expertise to help service providers manage the risk management process, from assessment and scoring to remediation and reporting, across all their clients.
The platform automates risk and compliance assessments, identifying vulnerabilities, evaluating controls, and generating accurate risk scores infused with seasoned CISO knowledge. By standardizing this process, Cynomi eliminates manual, repetitive work and ensures that each client receives consistent, evidence-based results. Service providers report significant time savings, enabling them to serve more clients and allocate resources more strategically.
Beyond identifying risks, Cynomi automatically generates actionable remediation plans, complete with prioritized tasks and framework mapping for standards such as ISO 27001, SOC 2, HIPAA, and PCI DSS. This built-in structure provides a clear path toward improved security posture and compliance readiness, allowing service providers to deliver immediate value and measurable progress to their clients.
Designed specifically for MSPs and MSSPs, Cynomi supports true scalability. Its multi-tenant architecture gives them centralized visibility and standardized workflows across multiple client environments, supporting the growth of their cybersecurity offerings and the delivery of consistent, high-quality services with ease. Junior staff can confidently perform expert-level tasks thanks to the platform’s embedded CISO guidance, raising overall service quality and client trust.