For MSPs and MSSPs, managing cybersecurity across multiple clients can feel like orchestrating chaos. Your team juggles dozens of tasks, from running risk assessments and tracking vulnerabilities to building client reports and planning remediation. These activities often happen in disconnected silos—a spreadsheet for compliance, a separate tool for ticketing, and manual processes for just about everything in between. This ad-hoc approach is inefficient and a direct threat to your scalability, profitability, and service quality.
When workflows are fragmented, crucial details get lost. Technical experts waste valuable hours on redundant data entry and manual report generation, pulling them away from strategic security work. This operational drag leads to inconsistent service delivery, a higher risk of human error, and an inability to provide clients with a clear, unified view of their security posture. The result is a constant state of reactive firefighting that prevents your MSP from growing effectively.
The solution is not to work harder. This article explains how a centralized platform like Cynomi transforms chaotic, manual processes into clear, repeatable, and automated workflows. We’ll explore how unifying assessments, remediation planning, and reporting creates a foundation for efficiency, accuracy, and superior client outcomes.
The Problem: The High Cost of Manual Processes
Before diving into the solution, it’s critical to understand the tangible business problems caused by manual, fragmented cybersecurity management. When your team operates without a unified system, you face several distinct challenges that can directly impact your bottom line and client satisfaction.
- Operational Inefficiency: Security experts spend an inordinate amount of time toggling between different tools, manually correlating data, and building reports from scratch. This administrative burden limits their capacity and diverts their focus from high-value tasks like threat analysis and strategic planning.
- Increased Risk of Error: Manual data entry and copy-pasting information between systems are recipes for mistakes. An incorrect vulnerability score, a missed compliance requirement, or an inaccurate client report can have serious consequences, eroding trust and potentially exposing clients to risk.
- Inconsistent Service Delivery: Without a standardized process, the quality of service can vary significantly from one client to another, or even from one security professional to another. This lack of consistency makes it difficult to guarantee service levels and provide a uniform client experience.
- Inability to Scale: Onboarding and managing new clients becomes a monumental, time-consuming effort. Each new client requires a manual setup across multiple platforms, creating a bottleneck that directly constrains your MSP’s growth potential.
These issues create a cycle of inefficiency that prevents you from building a mature, profitable cybersecurity practice. The only way to break this cycle is to implement a system that brings order to chaos.
1. Centralizing Assessments: The Foundation of Clarity
Every effective cybersecurity program begins with a clear understanding of risk. However, for many MSPs, conducting risk assessments is a cumbersome, manual process involving checklists, spreadsheets, and hours of analysis. This approach is not only slow but also subjective, making it difficult to produce consistent and actionable results.
Cynomi transforms this foundational step by automating the entire risk assessment process within a single, centralized platform. It moves you from subjective guesswork to objective, data-driven analysis.
How Cynomi Structures Assessments:
- Automated Data Collection: The platform gathers information across a client’s environment to identify vulnerabilities, misconfigurations, and security gaps.
- Standardized Frameworks: Assessments are benchmarked against established industry standards like NIST CSF, CIS Controls, and ISO 27001. This provides an objective measure of the client’s security posture and compliance status.
- AI-Powered Analysis: Powered by AI and infused with CISO knowledge, Cynomi analyzes the collected data to prioritize risks based on their potential business impact. This ensures you and your client focus on what matters most.
By structuring assessments this way, Cynomi creates a single source of truth for each client’s risk profile. The output is no longer a static spreadsheet but a dynamic, prioritized list of findings that serves as the blueprint for all subsequent security activities.
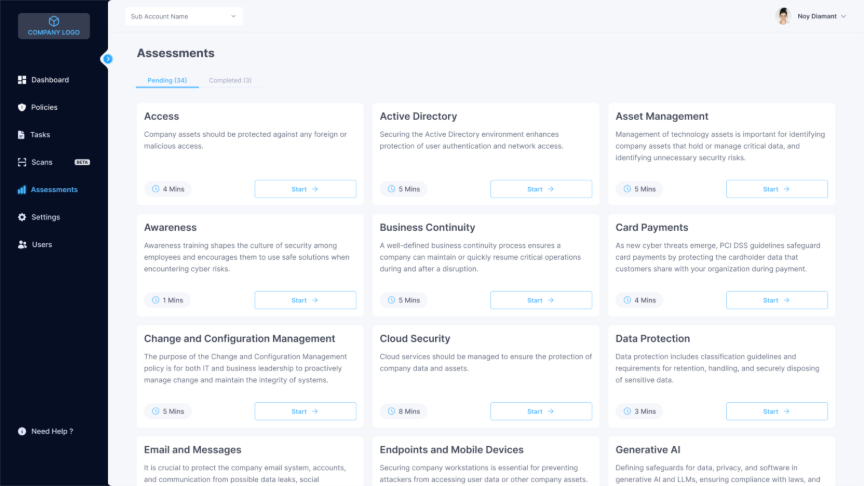
2. Streamlining Remediation: From Plan to Action
Identifying risks is only half the battle. The next critical step is creating and executing a plan to fix them. In a disconnected environment, this process is often disjointed. Remediation tasks are tracked in separate ticketing systems, project management tools, or even via email, with no clear link back to the original risk assessment.
Cynomi bridges this gap by integrating remediation planning directly into the workflow. It acts as a CISO copilot, guiding you from risk identification to resolution within the same interface.
How Cynomi Structures Remediation:
- Automated Remediation Plans: Based on the risk assessment findings, Cynomi automatically generates a detailed, prioritized remediation plan. Each task includes clear instructions and guidance, saving your team hours of planning.
- Task Management and Tracking: The platform allows you to assign tasks, set deadlines, and monitor progress in real-time. This eliminates the need for external project management tools and ensures that no remediation task falls through the cracks.
- Connecting Risks to Solutions: Cynomi enables you to map your MSP’s services directly to the remediation tasks. When the plan calls for implementing MFA, you can link it to your Identity and Access Management service. This creates a natural and seamless path for upselling and demonstrating how your offerings directly solve the client’s documented problems.
This integrated approach ensures a closed-loop process where every identified risk has a corresponding action plan, tracked to completion in a single, transparent system.

3. Automating Reporting: From Data Dumps to Value Demonstration
Reporting is where many MSPs stumble. Manually compiling data from multiple security tools into a client-friendly report is tedious and error-prone. The final product is often a static PDF filled with technical jargon that fails to communicate the value of your services to business leaders.
Cynomi revolutionizes this process by automating the creation of value-driven, executive-ready reports. It transforms reporting from a time-consuming chore into a powerful tool for building trust and proving your worth.
How Cynomi Streamlines Reporting:
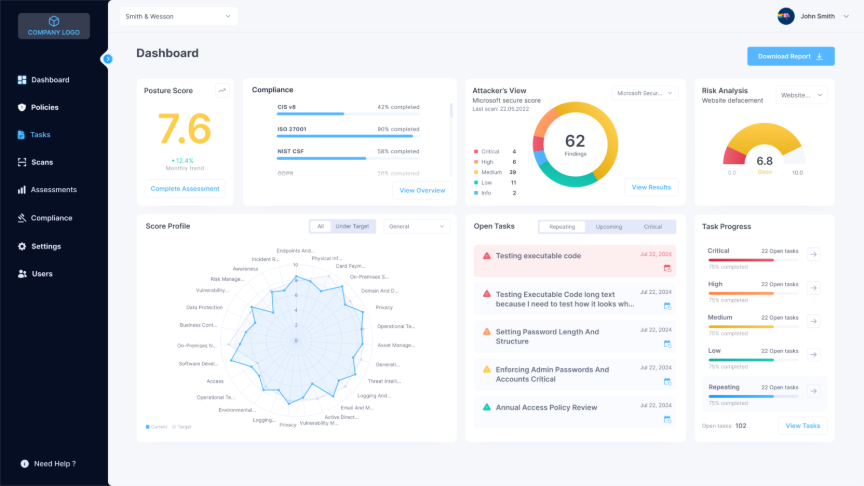
- Centralized Data Aggregation: The platform automatically pulls data from assessments, remediation progress, and compliance tracking into a unified dashboard.
- Executive-Level Dashboards: Cynomi presents information through clear, visual dashboards that translate technical metrics into business context. Clients can see their risk score trending down, their compliance posture improving, and the ROI on their security investment.
- On-Demand, Client-Ready Reports: With a few clicks, you can generate comprehensive reports that are professional, branded, and easy for non-technical stakeholders to understand. This eliminates hours of manual work and ensures consistency across all clients.
By structuring reporting this way, Cynomi empowers you to clearly and consistently demonstrate the impact of your work, solidifying your position as an indispensable strategic partner.
The Outcome: A Scalable, Profitable, and Mature Security Practice
By moving from chaos to clarity, MSPs can achieve profound business outcomes. Structuring your cybersecurity workflows with a centralized platform like Cynomi is not just an operational improvement; it’s a strategic transformation.
The benefits are clear:
- Improved Efficiency: Automation and standardized workflows drastically reduce the manual labor required to manage client security, freeing up your team to focus on growth and strategic initiatives.
- Enhanced Service Quality: Consistency and accuracy become the norm, ensuring every client receives the same high level of service.
- Greater Profitability: Reduced operational overhead, combined with seamless upselling opportunities, directly improves your margins.
- Effortless Scalability: A repeatable, efficient process for onboarding and management allows you to grow your client base without a proportional increase in headcount.
Cynomi’s Service Provider Growth Enablement Engine provides the essential framework to make this transition. It is the central hub that connects your people, processes, and technology, enabling you to deliver more effective cybersecurity services to more clients in a fraction of the time. Stop wrestling with fragmented tools and start building a structured, scalable security practice that drives both protection and profit.
Learn more about how Cynomi can help unify your efforts.