A third-party risk management (TPRM) solution is software that identifies, assesses, and manages risks from vendors and partners.
They reduce vendor risks, streamline onboarding, and support compliance readiness.
Onboarding workflows, customizable questionnaires, continuous monitoring, and remediation planning.
Top picks include Cynomi, OneTrust, RiskRecon, Prevalent, ProcessUnity, Venminder, Panorays, Bitsight, Nvendor, and UpGuard.
It embeds vendor risk into a vCISO platform for MSPs/MSSPs, with multi-tenant design and automated scoring.
As modern organizations rely on a growing web of vendors and partners, vendor risk management is no longer optional; it’s a business-critical priority. Third-party risk management solutions, also referred to as TPRM platforms, help identify, monitor, and mitigate vendor threats while ensuring compliance and operational resilience. This article explores what TPRM software does, its benefits, and the top tools for 2026.
What Is a Third-Party Risk Management Solution?
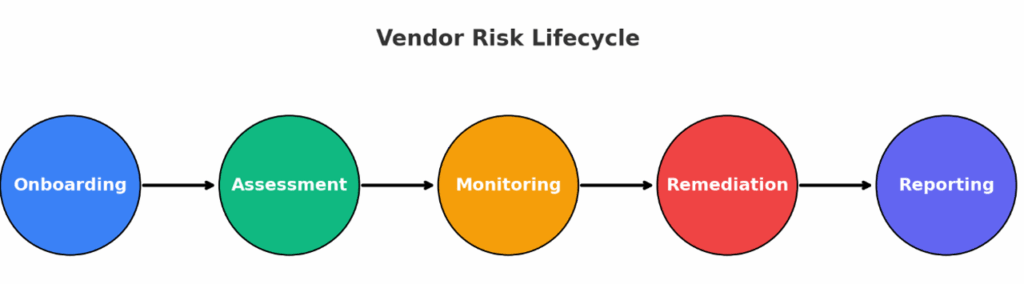
A third-party risk management solution, also called third-party risk management software or a TPRM solution, is designed to help organizations identify, evaluate, and reduce risks introduced by external vendors, suppliers, and partners. As companies depend on an expanding ecosystem of third parties to deliver products and services, these relationships create new vulnerabilities that can lead to data breaches, compliance gaps, or reputational damage.
Unlike manual spreadsheets and fragmented processes, a TPRM platform centralizes vendor oversight into one structured system. It allows security and compliance teams to follow consistent workflows for evaluating vendors, maintaining evidence, and tracking issues.
In short, third-party risk management provides a standardized, repeatable approach to managing vendor risk, helping organizations build trust, maintain compliance, and strengthen their overall cybersecurity posture.
The Benefits of Using Third-Party Risk Management Solutions
Adopting a third-party risk management solution delivers measurable advantages across security, compliance, and operations. By shifting away from manual spreadsheets and fragmented processes, organizations gain structure, visibility, and speed in managing vendor-related risks.
Key benefits include:
- Streamlined vendor due diligence
TPRM platforms standardize the way vendors are assessed before engagement. Automated workflows and pre-built templates replace manual questionnaires, reducing time and ensuring consistent evaluations across the supply chain. - Faster onboarding processes
Efficient due diligence shortens onboarding cycles, allowing businesses to start working with vendors sooner without sacrificing security. - Improved audit readiness
Audit trails, stored documentation, and evidence collection are built directly into the platform. This ensures organizations can quickly demonstrate compliance with frameworks such as SOC 2, HIPAA, ISO/IEC 27001, or PCI DSS when required. - Centralized risk data
Instead of scattered files and emails, all vendor information: risk scores, assessments, policies, and remediation steps, lives in one central dashboard. This enables management to view the entire vendor ecosystem at a glance. - Always-on monitoring
Risks don’t stop after onboarding. Leading TPRM tools provide ongoing monitoring of vendor security posture and compliance status, generating real-time alerts for changes or new threats.
Key Features to Look For in TPRM Tools
To ensure a strong return on investment, when evaluating third-party risk management tools, organizations should look for features that simplify vendor oversight while aligning with industry compliance requirements. The most important capabilities include:
- Vendor onboarding and due diligence workflows
Built-in templates and automated workflows help security and procurement teams evaluate vendors consistently. This eliminates ad-hoc processes and ensures that no critical checks are skipped before granting access to sensitive systems or data. - Customizable risk questionnaires
Every industry faces different risks. Strong TPRM platforms let organizations tailor vendor questionnaires to specific compliance frameworks, geographic regulations, or industry standards such as SOC 2, HIPAA, or ISO/IEC 27001. - Continuous monitoring and scoring
Third-party risks evolve quickly. Leading cyber-focused tools provide real-time monitoring, often leveraging external security-rating feeds, attack-surface scans, and automated scoring. - Risk remediation planning
Identifying vendor risks is only half the challenge. Managing them is just as important. The best third-party risk management solutions offer centralized remediation workflows that assign tasks, set deadlines, and track resolution progress across internal teams and vendors.
Advanced Capabilities (Nice to Have)
Beyond the core functions of onboarding, questionnaires, and monitoring, advanced capabilities can make the difference between a basic compliance checklist and a proactive risk management program. When evaluating third-party risk management solutions, consider whether they also provide:
- Automated compliance mapping
Advanced TPRM platforms can automatically align vendor controls with industry frameworks such as NIST, PCI DSS, or HIPAA. This reduces manual effort for compliance teams and simplifies cross-framework reporting. - Integration with security and IT systems
Modern TPRM platforms often integrate with SIEM, GRC, and procurement systems. This ensures vendor risks are not siloed but part of the broader security and operational picture. - Risk tiering and segmentation
Different vendors carry different risks. Advanced tools automatically categorize vendors by criticality, allowing organizations to prioritize monitoring and remediation for high-risk suppliers. - Predictive analytics and benchmarking
Some solutions apply AI to forecast potential vendor risks or benchmark a supplier’s security posture against industry peers, enabling more informed decision-making. - Multi-tenant architecture for service providers
For MSPs and MSSPs managing multiple clients, multi-tenancy provides a centralized view while keeping client data securely separated. This is especially valuable for scaling third-party risk management services across a diverse customer base.
Best 10 Third-Party Risk Management Software Solutions for 2026
Choosing the right third-party risk management tool is essential for reducing vendor-related risks and meeting compliance requirements. Below are ten leading TPRM solutions for 2025 that are helping organizations streamline vendor oversight and improve security outcomes.
1. Cynomi
Main Features
- Integrated vendor risk assessments embedded in broader vCISO and compliance workflows.
- Multi-tenant architecture for MSPs/MSSPs.
- Automated risk scoring aligned to compliance frameworks.
- Centralized evidence collection, task tracking, and reporting.
Best For
MSPs, MSSPs, and compliance-centric teams that prefer a unified security + vendor risk platform rather than standalone TPRM tools.
Pricing
Contact sales for a custom quote.
The Verdict: ⭐⭐⭐⭐⭐ A compelling choice for providers wanting TPRM built into a complete security/compliance stack.
Click to read Cynomi reviews.
2. OneTrust
Main Features:
- Lifecycle automation for onboarding, assessment, and offboarding.
- Dynamic control frameworks & conditional questionnaires.
- Vendor inventory with dashboard visibility.
- Continuous monitoring and rule-based triggers for reassessments.
Best For
Large enterprises needing deep privacy, governance, and risk vendor management within one platform.
Pricing
Contact sales for a custom quote.
The Verdict: ⭐⭐⭐⭐ Strong for organizations with heavy regulatory and privacy demands.
Click to read OneTrust reviews.
3. RiskRecon
Main Features
- External, outside-in security posture assessments.
- Prioritized risk findings by severity.
- Vendor benchmarking and comparisons.
- Support for remediation workflow integration.
Best For
Security teams looking for objective external visibility into vendor risk signals beyond questionnaires.
Pricing
Contact sales for a custom quote.
The Verdict: ⭐⭐⭐⭐ Excellent for continuous external insight; works best combined with internal assessment tools.
Click to read RiskRecon reviews.
4. Prevalent (by Mitratech)
Main Features
- Vendor onboarding/offboarding, assessments, monitoring, and remediation.
- Native monitoring across cyber, business, and financial domains.
- AI assistant (Prevalent Alfred™).
- Integration via connectors.
- SLA / performance tracking.
Best For
Procurement, vendor risk, and enterprise teams needing mature end-to-end TPRM capabilities.
Pricing:
Contact sales for a custom quote.
The Verdict: ⭐⭐⭐ Feature-rich choice for mature programs, though may exceed the needs of smaller teams.
Click to read Prevalent reviews.
5. ProcessUnity
Main Features
- Full vendor lifecycle management: onboarding, assessment, monitoring, offboarding.
- Global Risk Exchange access (18,000+ attested assessments, 370,000 vendor profiles).
- AI/automation in evidence review and workflow enhancements.
- Configurable processes & control frameworks to match program maturity
Best For
Organizations that need high configurability, data augmentation via exchange, and workflow automation to scale TPRM.
Pricing
Contact sales for a custom quote.
The Verdict: ⭐⭐⭐⭐ Very strong for mature TPRM programs seeking automation, data leverage, and flexibility.
Click to read ProcessUnity reviews.
6. Venminder (an Ncontracts company)

Main Features
- Continuous vendor screening across multiple risk domains.
- Centralized intelligence and vendor performance tracking.
- Contract, document, and vendor lifecycle management.
- Flexible packaged capabilities as vendor risk program scales.
Best For
Teams looking for continuous vendor intelligence and screening, plus vendor lifecycle oversight.
Pricing
Contact sales for a custom quote.
The Verdict: ⭐⭐⭐⭐ Solid option for organizations scaling their vendor risk intelligence and oversight.
Click to read Venminder reviews.
7. Panorays
Main Features
- Combines automated questionnaires with external attack surface analyses.
- Vendor criticality modeling and continuous posture evaluation.
- Remediation guidance and benchmarking.
Best For
Organizations looking for both internal and external vendor risk views in a unified solution.
Pricing
Contact sales for a custom quote.
The Verdict: ⭐⭐⭐⭐ Balanced between questionnaire and external visibility, useful for mid-to-large scale programs.
Click to read Panorays’ reviews.
8. Bitsight (Security Ratings + TPRM Integrations)

Main Features
- External security ratings and risk signal ingestion.
- Integration with vendor risk / GRC platforms to bring rating data into workflows.
- Benchmarking and trend visibility across vendor portfolios.
Best For
Organizations that already use or want to adopt external security ratings and augment internal TPRM systems.
Pricing
Contact sales for a custom quote.
The Verdict
⭐⭐⭐Best used as a complement to internal TPRM workflows rather than a standalone platform.
Click to read Bitsight reviews.
9. Nvendor (by Ncontracts)

Main Features
- Vendor lifecycle management and contract oversight.
- AI-assisted contract review and ongoing due diligence.
- Tailored to financial institutions and regulated entities.
Best For
Banks, credit unions, and financial services firms require formal vendor risk programs with embedded regulatory controls.
Pricing
Contact sales for a custom quote.
The Verdict
⭐⭐⭐⭐ Strong fit when vendor risk is tightly bound to regulated financial operations.
Click to read Ncontracts reviews.
10. UpGuard
Main Features
- Continuous external monitoring of vendor security posture and breach exposure.
- Automated questionnaires & posture reports.
- Breach detection across third-party environments.
Best For
Organizations looking for external visibility into vendor risk with minimal overhead.
Pricing
Contact sales for a custom quote.
The Verdict:
⭐⭐⭐ Useful for supplementing existing risk programs, though it lacks full workflow depth.
Click to read UpGuard reviews.
How to Choose the Right TPRM Platform
With dozens of third-party risk management platforms on the market, selecting the right one can be challenging. The best fit depends on your organization’s vendor landscape, compliance needs, and internal resources.
When assessing potential vendors, balance must-have features with scalability. The right third-party risk management software will not only meet your current needs but also adapt as your vendor network and compliance obligations evolve. Key factors to evaluate include:
- Vendor volume and risk tiering
Start by considering how many vendors you manage and how critical they are to your operations. High volumes of suppliers may require advanced automation and risk tiering features to prioritize the riskiest vendors without overloading your team. - Industry frameworks supported
Not every TPRM tool covers the same compliance standards. Make sure the platform supports the frameworks most relevant to your industry, whether that’s SOC 2 and ISO/IEC 27001 for tech companies, HIPAA for healthcare, or PCI DSS for payment providers. - Customization level
Every organization’s vendor risk process is unique. Look for platforms that let you customize risk questionnaires, scoring models, and workflows so they reflect your industry, regulatory environment, and risk tolerance. - Integration capabilities
A TPRM solution shouldn’t operate in isolation. Leading tools integrate with GRC systems, procurement platforms, and security technologies like SIEM or vulnerability scanners, ensuring vendor risk data flows into your broader cybersecurity and compliance ecosystem.
How Cynomi Enhances Third-Party Risk Management
Cynomi goes beyond traditional third-party risk management software by embedding vendor oversight into a broader vCISO and compliance management platform. Built specifically for MSPs and MSSPs, Cynomi provides a multi-tenant architecture that enables service providers to manage vendor risk across multiple clients without duplicating effort efficiently.
The platform delivers automated vendor risk scoring infused with seasoned CISO expertise, helping service providers quickly evaluate supplier security posture and align findings with frameworks such as SOC 2, HIPAA, and ISO/IEC 27001. This ensures that vendor assessments are not only consistent but also mapped directly to regulatory requirements.
Cynomi also supports compliance alignment and reporting, allowing service providers to demonstrate value to their clients by showing exactly how vendor risks impact compliance standing. With structured processes and automation that significantly cut manual work, teams can scale third-party risk management services without adding staff.
As a security-first platform, Cynomi treats compliance and risk management as the outcomes of robust cybersecurity practices. This gives service providers confidence that they are helping their clients reduce vendor risk, strengthen resilience, and maintain compliance, all from a single, easy-to-use TPRM platform.