Cybersecurity is everyone’s business. Compliance requirements, investor demands, and data breaches are just a few drivers pushing SMEs and startups to hire MSPs and cybersecurity consultants. Their InfoSec teams are often understaffed and fail to keep up with the shifting threat landscape and regulation.
Experiencing a successful data breach can effectively destroy a business, and breaches now cost companies an average of $4.45 million – a sum that’s increased by 15% over three years.
Estimating the likelihood of an end client falling victim to a successful data breach is no easy feat. A systematic and analytical approach is required to assess the cyber risk that can threaten their organization, and one way MSPs/MSSPs can accomplish this is by using a dynamic risk assessment template.
What is a Cybersecurity Risk Assessment Template?
A cybersecurity risk assessment (CSRA) or IT security risk assessment template is a systematic process to identify, evaluate, and prioritize potential vulnerabilities in an organization’s IT systems. Cybersecurity risk assessments are also part of the requirements for security measures in regulatory and industry standards such as HIPAA, ISO 27001, FISMA, NIST, SOC, and others.
From a service provider’s perspective, a cybersecurity risk assessment is part of the onboarding process for new customers and a regular part of InfoSec operations that helps uncover gaps in a client’s security posture. Cybersecurity risk assessments are invaluable in promoting a proactive approach to breach prevention and information protection, especially in highly regulated sectors like finance and healthcare.
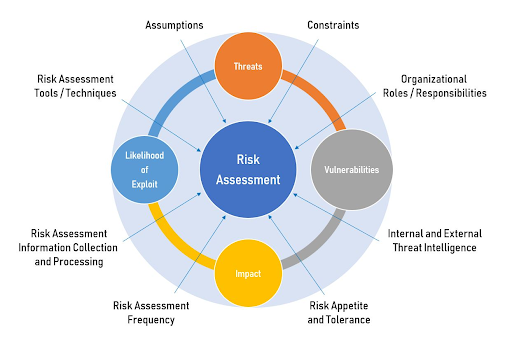
What threats does a cybersecurity risk assessment protect against?
Incompliance
Failure to comply with regulations and industry cybersecurity standards can create massive gaps in MSP/MSSP clients’ cybersecurity postures, leading to regulatory fines and loss of business revenue for those who fail to adhere to the ever-changing requirements of regulators and cybersecurity leaders.
Third-party Risk
From compromised open-source libraries used in corporate software to SaaS misconfigurations, third-party vendors risk giving strangers unauthorized access to MSP/MSSP clients’ potentially sensitive information.
Poor Data Protection Measures
Gaps in sensitive data protection mechanisms and systems can expose customer data and sensitive information to third parties accidentally or maliciously.
Why do you need a cybersecurity risk assessment template?
Using a comprehensive cybersecurity risk assessment template to customize the risk assessment process for your clients is a straightforward approach to quickly adding this service to your portfolio. The predefined structure of cybersecurity risk assessment templates also makes it easier to produce documentation and audit trails in formats required by regulators, like security policies. Plus, it facilitates effective communication of the risk assessment process through familiar report formats.
It’s important to note that for your cybersecurity risk assessment template to remain relevant and effective, you must invest time and resources in continuously updating it in line with future threats and vulnerabilities and re-evaluating the score values assigned to certain risks or vulnerabilities in your template. This measure will enable you to offer your customers an up-to-date evaluation of their organizational attack surface and a comprehensive view of their cybersecurity risk posture.
The Crucial Risk Assessment Template for Cybersecurity
A robust risk assessment template is built as a categorized process that you should execute at regular intervals. It’s worth noting that this template is not based on any particular cybersecurity framework or guidelines but rather provides a holistic step-by-step checklist for performing a crucial risk assessment. The steps are as follows:
1. Describe the Purpose
The purpose of risk assessment is heavily affected by whether it is an initial or a subsequent assessment. For example, while an initial risk assessment aims to establish a baseline of cyber risk or identify cyber threats, a reassessment may be initiated as part of a risk response to re-evaluate the effectiveness of current security controls.
2. Define the Scope
Before beginning any risk assessment process, you must set the boundaries and clearly define what is included. It entails identifying the systems, environments, software, hardware, cloud infrastructure, and processes that will be evaluated and audited for cyber security risk.
By clearly defining the scope of the cybersecurity risk assessment, you ensure that you effectively allocate resources to deliver valuable insights and actionable recommendations to stakeholders. Establishing the scope of the risk assessment process will also help determine the timeline and timeframe for its implementation.
3. Inventory Relevant Assets and Resources
The next step entails compiling a comprehensive catalog of all the relevant resources and assets included in the scope of the risk assessment. These include hardware, software, devices, applications, user and machine accounts, plus third-party services that may have access to sensitive information (such as payment card information, medical histories, personally identifiable information, etc).
You can prioritize each identified asset based on its importance to business operations and the potential fallout of its compromise to ensure effective resource allocation in mitigating potential risks to the critical business assets in the list.
Ensure you execute every step correctly by downloading the XLS risk assessment template.
4. Evaluate the Threat Landscape
With a clear understanding of where the critical assets of the end client organization are and who can access them, it’s time to map out the potential threats and systematic vulnerabilities that may pose a risk.
This part of the risk assessment template entails a comprehensive analysis of the potential risks that include (but are not limited to):
- Excessive access permissions
- Outdated IAM policies
- Unpatched software or firmware
- Reports of past risk events
- Threat information from cybersecurity vendors and industry groups.
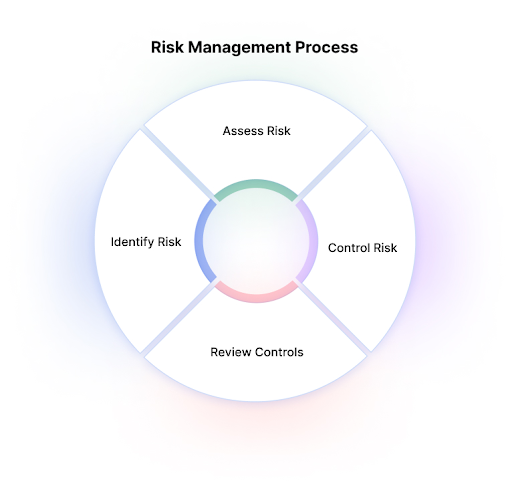
5. Determine Compromise Likelihood and Impact Radius
With an extensive catalog of your clients’ organizational assets and potential threats, you can begin to estimate the probability of attacks against them and the potential magnitude of the impact of a successfully exploited vulnerability.
At this stage, you can consider factors like threat actor sophistication, exploit availability, and the effectiveness of existing security controls to mitigate and minimize the damage of a threat event.
6. Calculate and Assign Cyber Risk Scores
With the numerical values you’ve assigned to asset sensitivity, threat event probability, and the potential impact of these events, you can calculate a risk score that will assist you in the next step: vulnerability prioritization.
7. Prioritize Vulnerability Mitigation
You likely have limited time, resources, and skills available at your disposal, so you must prioritize the most pressing issues and security gaps to address. In most cases, your team will want to start by highlighting and prioritizing the most critical and pressing issues uncovered in the cybersecurity risk assessment process and address them first.
8. Develop a Risk Handling Plan
Cybersecurity risk is unlike other types of risk in business, and there are a few common ways to address it:
- Resolve it by implementing solutions and services to prevent the security event from occurring.
- Avoid it by removing the vulnerable component from the system in favor of a more secure alternative.
- Transfer the risk to another entity, such as an MSP or insurer.
- Accept the risk associated with the vulnerability discovered when other risk-handling avenues are unavailable, or the risk score is particularly low.
9. Produce and Distribute a Cybersecurity Risk Assessment Report
The last part of your cybersecurity risk assessment process is gathering the necessary information, formatting it, and distributing it to the relevant stakeholders in your client’s organization.
This stage includes comprehensive documentation of all findings and recommendations. It will enable you to communicate the results of your risk assessment to client decision-makers who support risk responses and share the relevant information with the right personnel.
Cynomi’s Risk Assesment Process
Cynomi’s risk assessment is a sophisticated calculation done through assessments of multiple security domains and scoring based on each organization’s unique security profile. Cynomi uses proprietary algorithms and adaptive tailor-made questionnaires to build a unique cybersecurity profile for each organization. The risk assessment process is highly customized to ensure it fits the specific organization.
Each organization’s posture and risk are calculated based on that profile and compared to the desired posture of the specific organization, taking into account the organization’s parameters and characteristics, including company size, industry, geographical location, regulations and frameworks to comply with, available assets, and many more.
In other words, each organization’s posture is determined by comparing it to where it should be and not to where other organizations are (if you’re a small healthcare clinic in NY, you should be measured differently than a large law firm from Dallas).
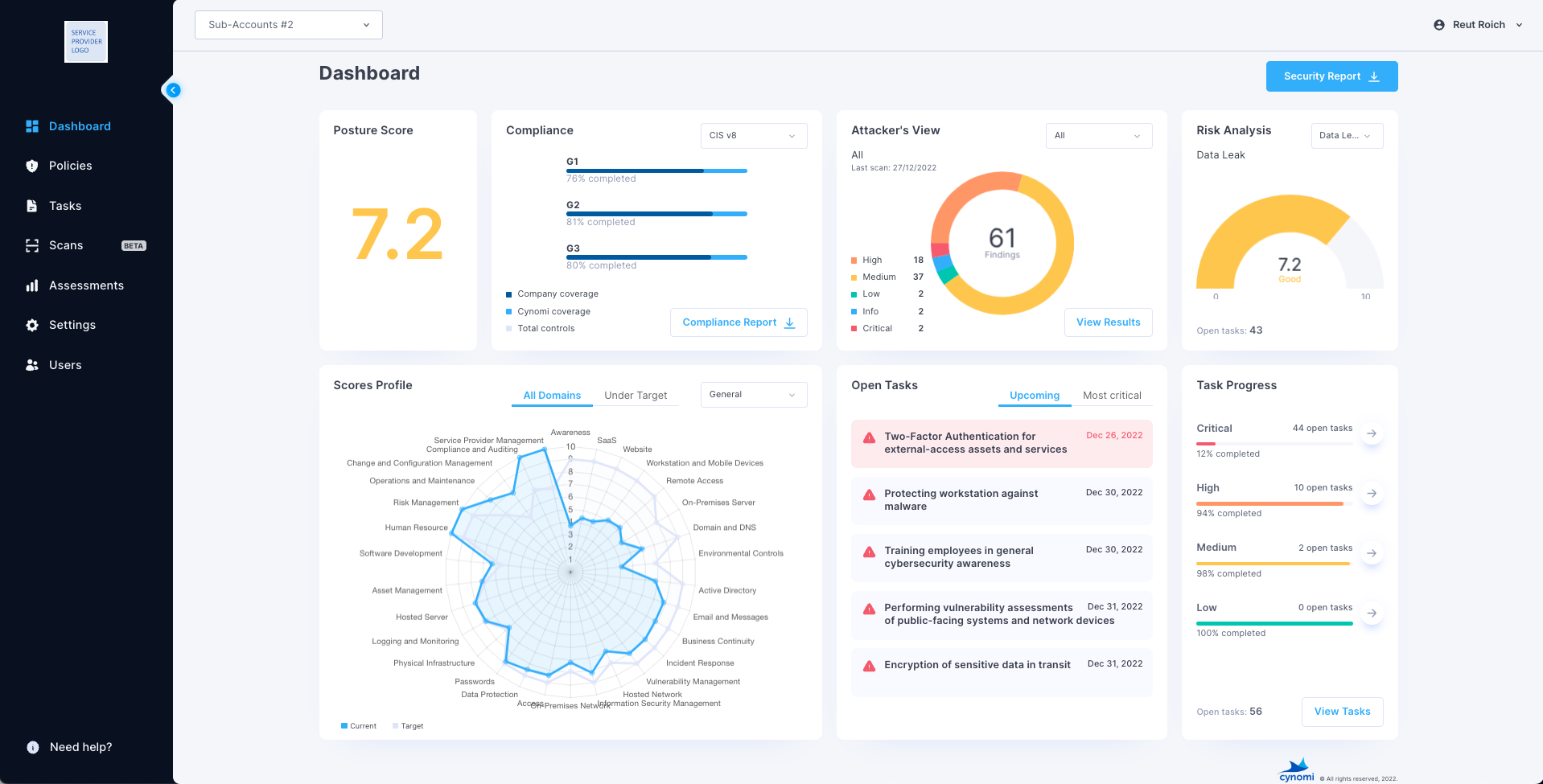
The result is an insightful dashboard that shows each organization’s security posture, risk areas, and domains to focus on, as can be seen in the attached screenshot.
Cynomi Dashboard for Partners
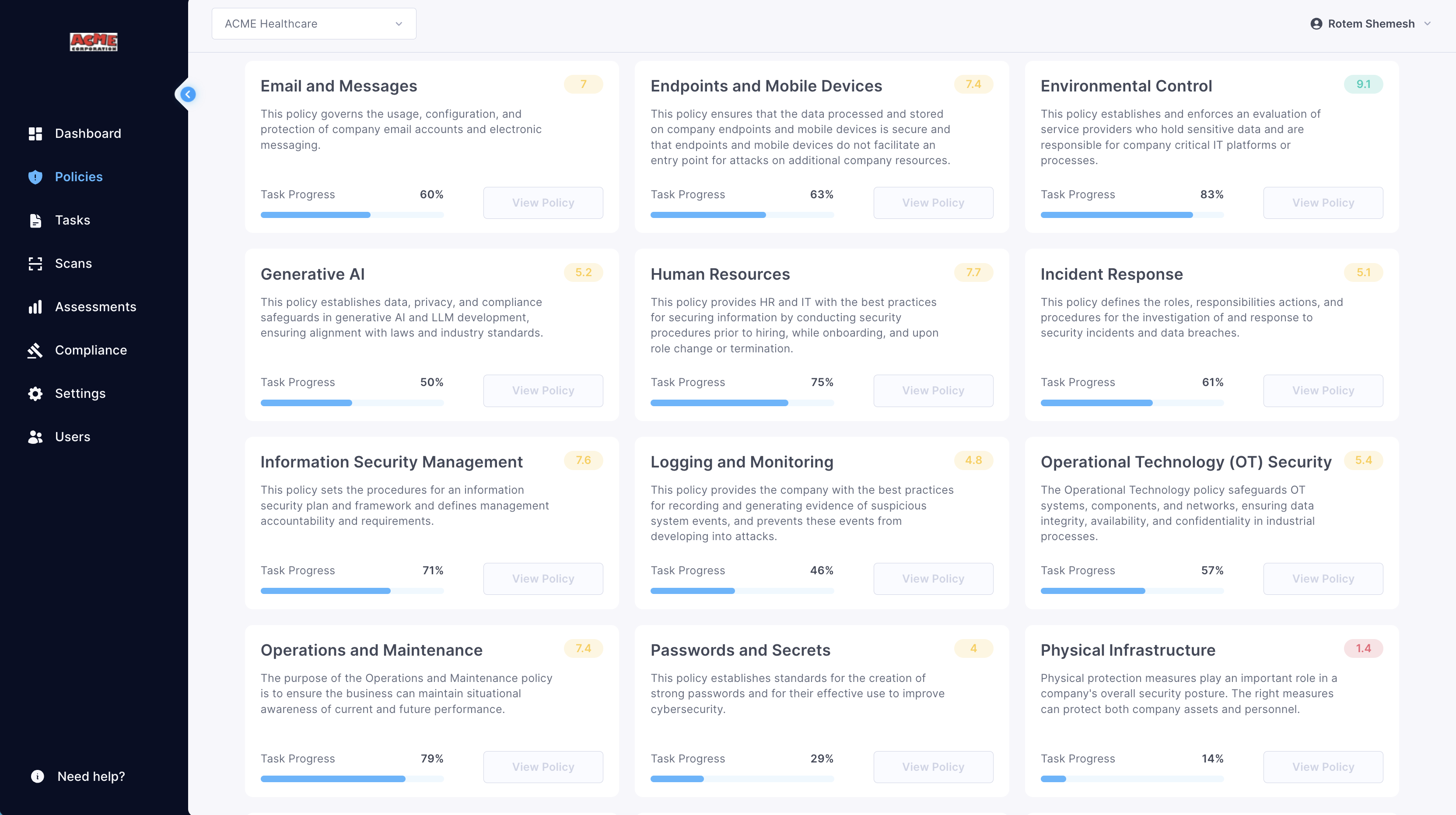
Cynomi Policy for Partners
Cynomi Assessments Organised by Domain
Automate Cybersecurity Risk Assessments at Scale With Cynomi’s vCISO Platform
A cybersecurity risk assessment template is a document that requires a lot of maintenance and customization for each of your clients and projects. It is a time-consuming challenge for InfoSec teams and the MSPs guiding them.
While there are advantages to using a familiar format like Excel for assessing cybersecurity risk, you should consider adopting an MSSP-centric platform like Cynomi that automates cybersecurity risk assessments and streamlines the process. Cynomi creates a unique cybersecurity profile per company, and uses adaptive, customized risk assessment questionnaires to automate the risk assessment process. It also leverages built-in scans to uncover critical vulnerabilities in externally visible IPs and URLs, including ports, protocols, encryption, and websites. Cynomi’s vCISO platform acts as the one source of truth for each of your customers’ risk assessment and augments the InfoSec team, enabling you to scale your InfoSec offering and demonstrate its value using your existing resources.
Book a demo today to learn more about how MSPs and MSSPs use Cynomi to scale operations, reduce costs, and upsell effective and accurate InfoSec solutions to their customers.