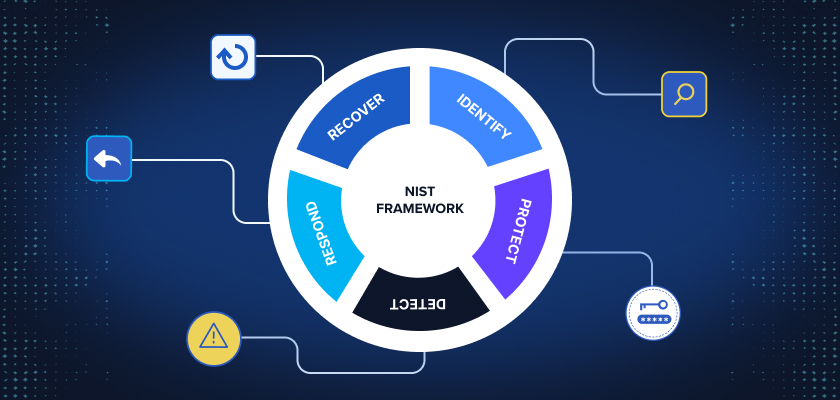
The NIST Cybersecurity Framework (CSF) provides a structured and standardized approach to managing cybersecurity risks. Developed by the National Institute of Standards and Technology (NIST), the framework is widely regarded as the gold standard for risk management and compliance.
Its flexibility and scalability make it ideal for organizations of all sizes and industries. For MSPs, MSSPs, and other service providers, adopting the NIST CSF strengthens cybersecurity posture, enhances service delivery, and demonstrates a commitment to protecting sensitive information.
What Is the NIST Cybersecurity Framework (CSF)?
The NIST Cybersecurity Framework (CSF) is a voluntary, risk-based framework developed by the National Institute of Standards and Technology (NIST) to help organizations manage and mitigate cybersecurity risks. It provides a common language and methodology for identifying vulnerabilities, prioritizing risks, and implementing safeguards to protect critical systems and sensitive information.
Designed with flexibility in mind, the framework can be tailored to organizations of all sizes and across various industries. Its primary goal is to enhance security practices by offering a structured yet customizable approach that aligns with each organization’s unique risk tolerance and operational needs.
The NIST CSF is widely adopted by businesses, government agencies, and service providers worldwide. For MSPs and MSSPs, the framework is particularly valuable as it provides the foundation for delivering standardized and scalable cybersecurity services to clients while supporting regulatory compliance efforts.
Why Is the NIST Cybersecurity Framework Important?
The NIST CSF offers organizations a robust framework for addressing the increasingly complex challenges of cybersecurity.
- Comprehensive Security Coverage: Addresses every stage of the cybersecurity lifecycle, from risk management to recovery.
- Standardization and Consistency: Enables organizations to implement consistent, repeatable security processes.
- Compliance Readiness: Aligns with regulatory standards like HIPAA, GDPR, and CMMC, simplifying audits and certifications.
- Global Recognition: Trusted worldwide as a gold standard for cybersecurity frameworks
Core Components of the NIST Cybersecurity Framework
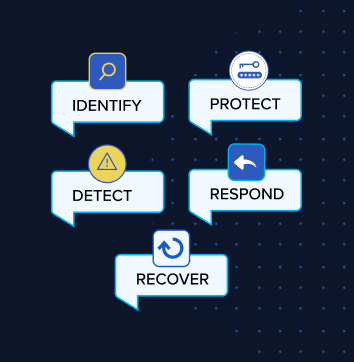
NIST CSF Core Functions:
The NIST CSF is structured around six core functions:
- Identify: Recognize and understand risks, assets, and vulnerabilities within an organization.
- Protect: Implement measures to safeguard critical systems and data.
- Detect: Monitor systems for real-time identification of threats and anomalies.
- Respond: Develop and execute a plan to contain and mitigate incidents.
- Recover: Restore normal operations quickly and efficiently after an incident.
Tiers and Implementation Levels:
The NIST CSF includes four tiers to help organizations assess their maturity and risk tolerance:
- Tier 1 – Partial: Informal processes and reactive responses to threats.
- Tier 2 – Risk-Informed: Risk management is understood but inconsistently applied.
- Tier 3 – Repeatable: Standardized processes that are consistently applied and monitored.
- Tier 4 – Adaptive: Continuously improving processes that dynamically address risks and threats.
Profiles:
Organizations can create tailored profiles to align the framework’s core functions with their specific business goals and regulatory needs.
How the NIST Cybersecurity Framework Works
The NIST Cybersecurity Framework (CSF) operates as a practical guide to developing, implementing, and maintaining a strong cybersecurity posture. By breaking down cybersecurity management into manageable steps, the framework ensures that organizations can comprehensively address risks, meet compliance requirements, and respond effectively to emerging threats.
This process is flexible, allowing businesses to customize it according to their industry, size, and specific security needs. Whether for federal agencies or private enterprises, the framework promotes a proactive and iterative approach to cybersecurity.
- Assessment and Planning: Conduct a risk assessment to identify vulnerabilities and understand the current security posture.
- Framework Customization: Create a security profile that aligns with industry-specific needs and business objectives.
- Control Implementation: Apply security controls tailored to the organization’s risk profile and operational requirements.
- Monitoring and Response: Use monitoring tools and an incident response plan to detect and address security threats proactively.
- Review and Improvement: Conduct regular assessments to adapt to new threats and ensure compliance with evolving standards.
Key Benefits of Adopting the NIST CSF
Adopting the NIST Cybersecurity Framework equips organizations with a proven strategy for managing and mitigating risks in an ever-evolving digital landscape. More than just a technical standard, the CSF serves as a business enabler, helping organizations align cybersecurity practices with broader operational goals.
- Improved Cybersecurity Posture: Uses globally recognized best practices to proactively address risks.
- Enhanced Compliance Readiness: Simplifies compliance with standards like HIPAA, PCI-DSS, and ISO 27001.
- Risk Reduction: Identifies and mitigates potential threats before they become significant problems.
- Business Continuity and Resilience: Ensures minimal disruption from cyber incidents through robust response and recovery measures.
- Client Trust and Market Competitiveness: Demonstrates a commitment to strong cybersecurity, building confidence with clients and stakeholders.
How to Implement the NIST CSF
Implementing the NIST Cybersecurity Framework requires more than just a one-time effort; it demands a thoughtful, iterative approach tailored to the unique challenges and objectives of each organization. This structured process integrates risk management, policy development, and ongoing monitoring to establish a comprehensive security program.
- Conduct a Security Assessment: Identify and document current cybersecurity measures and gaps.
- Define a Risk Management Plan: Create a roadmap for mitigating and monitoring identified risks.
- Develop Security Policies: Establish policies for access control, incident response, and data protection.
- Automate Monitoring and Reporting: Use automated tools to continuously monitor systems and ensure compliance.
- Train Employees and Stakeholders: Conduct regular cybersecurity awareness sessions and technical training.
- Review and Update Regularly: Adapt your program to address new threats, regulatory changes, and audit findings.
Strengthen Your Cybersecurity with the NIST Cybersecurity Framework
The NIST Cybersecurity Framework is an essential tool for organizations looking to enhance their cybersecurity practices, reduce risks, and achieve compliance with regulatory standards. By adopting the framework, businesses can establish a robust security posture and build resilience against cyber threats.
Step-by-Step Guide to NIST Compliance for Service Providers
Simplify NIST compliance with a step-by-step roadmap, actionable best practices, and tools to help your MSP or MSSP scale services efficiently and securely.
Frequently Asked Questions About the NIST Cybersecurity Framework
A voluntary, risk-based framework designed to manage and mitigate cybersecurity risks.
Businesses, government agencies, and service providers seeking to improve cybersecurity.
It provides a structured approach to identify, protect, detect, respond to, and recover from threats.
No, but it is highly recommended for organizations to strengthen cybersecurity and meet compliance requirements.
Identify, Protect, Detect, Respond, and Recover.