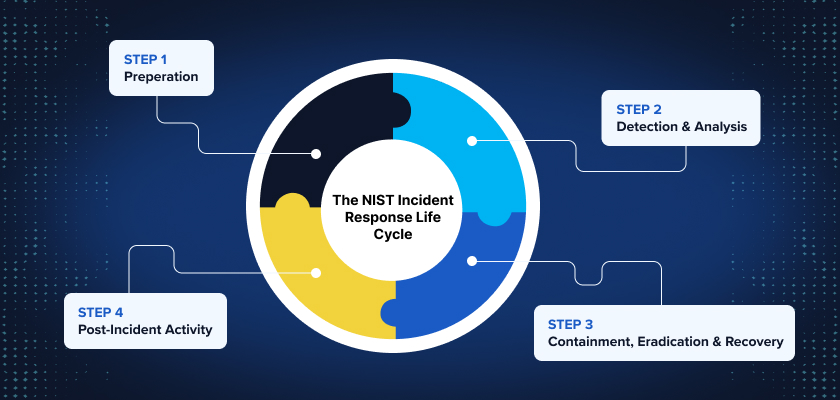
The NIST Incident Response Life Cycle, defined in NIST SP 800-61, is a four-phase process designed to help organizations effectively handle cybersecurity incidents. By providing a structured approach, the life cycle ensures that businesses can prepare for, respond to, and recover from incidents, minimizing their impact.
This framework is essential for organizations managing sensitive data or critical systems, including IT service providers, Managed Service Providers (MSPs), and Managed Security Service Providers (MSSPs). It builds cybersecurity resilience and demonstrates a proactive approach to incident management, helping businesses maintain operations and compliance during cyber events.
What Is the NIST Incident Response Life Cycle
The NIST Incident Response Life Cycle is a repeatable process that guides organizations in handling cybersecurity incidents efficiently and effectively. By breaking incident management into four distinct phases, the life cycle ensures a consistent, systematic approach to mitigating threats.
Its purpose is to minimize damage from incidents like data breaches, ransomware attacks, or malware infections. It’s widely adopted across industries by organizations that prioritize robust cybersecurity management to protect sensitive data and critical infrastructure.
Why Is the NIST Incident Response Life Cycle Essential?
Adopting the NIST Incident Response Life Cycle provides organizations with a clear roadmap for managing incidents, ensuring they can address cyber threats proactively.
Key benefits include:
- Minimizes Security Risks: Reduces the impact of breaches through a swift, coordinated response.
- Supports Compliance: Aligns with regulatory standards like CMMC, HIPAA, and PCI-DSS.
- Improves Preparedness: Builds resilience through regular training and incident simulations.
- Ensures Business Continuity: Maintains operations during and after incidents by addressing them effectively.
- Strengthens Client Trust: Demonstrates a commitment to cybersecurity and transparency.
Phases of the NIST Incident Response Life Cycle

The NIST Incident Response Life Cycle is composed of four distinct phases, each critical to effective incident management.
| Phase | Objective | Key Actions |
| Preparation | Establish incident response capabilities before a cybersecurity event occurs. | • Develop an incident response policy and incident handling procedures. • Define roles and responsibilities within the incident response team. • Conduct regular employee security training and tabletop exercises. • Deploy security tools like firewalls, endpoint protection, and SIEM solutions. |
| Detection and Analysis | Identify and evaluate potential security incidents. | • Monitor system logs, network traffic, and security alerts. • Use automated threat detection tools and threat intelligence platforms. • Analyze indicators of compromise (IOCs) and suspicious activity. • Classify incidents by severity level and business impact. |
| Containment, Eradication, and Recovery | Limit the spread of the incident, eliminate threats, and restore normal operations. | • Short-Term Containment: Isolate affected systems to prevent further damage. • Long-Term Containment: Apply patches, disable compromised accounts, and strengthen security controls. • Eradication: Remove malicious files, malware, or intruders from the system. • Recovery: Restore affected systems from backups and validate system functionality, and conduct post-recovery assessments to ensure normal operations. |
| Post-Incident Activity | Learn from the incident to improve future response efforts. | • Conduct root-cause analysis to identify how the incident occurred. • Review incident handling procedures and update response plans accordingly. • Generate a post-incident report with findings and recommended improvements. • Share lessons learned with the incident response team and relevant stakeholders. |
How the Incident Response Life Cycle Aligns with the NIST CSF
The NIST Incident Response Life Cycle is deeply integrated with the NIST Cybersecurity Framework (CSF), supporting its core functions:
- Detect (DE): Monitoring systems for anomalies and generating alerts support the Detection and Analysis phase.
- Respond (RS): Activities like containment and eradication align directly with the Respond function in NIST CSF.
- Recover (RC): Recovery efforts ensure continuity and align with the Recover function, addressing operational resilience.
- Identify (ID): The Preparation phase incorporates risk assessments and audits, aligning with the Identify function.
Best Practices for Managing the Incident Response Life Cycle
To maximize the effectiveness of the NIST Incident Response Life Cycle, organizations should adopt these best practices:
- Develop a Comprehensive Incident Response Plan: Include detailed procedures for each phase of the life cycle, ensuring clarity and consistency.
- Define Roles and Responsibilities: Assign clear roles for incident managers, forensic analysts, IT staff, and legal advisors.
- Use Automated Monitoring Tools: Deploy SIEMs, endpoint detection tools, and automated alerting systems to streamline detection.
- Conduct Regular Training and Simulations: Train employees annually and simulate incidents to improve preparedness and response skills.
- Review and Update Incident Response Policies: Regularly revise incident response plans to reflect lessons learned and address emerging threats.
Build Resilience with the NIST Incident Response Life Cycle
The NIST Incident Response Life Cycle provides organizations with a structured approach to managing cybersecurity incidents effectively. By following our NIST Incident Response Plan Template and adopting best practices, businesses can reduce the impact of threats, maintain compliance, and improve their overall security posture.
Incorporating this framework into your cybersecurity strategy demonstrates a proactive commitment to resilience, client trust, and operational excellence.
Step-by-Step Guide to NIST Compliance for Service Providers
Simplify NIST compliance with a step-by-step roadmap, actionable best practices, and tools to help your MSP or MSSP scale services efficiently and securely.
Frequently Asked Questions About the NIST Incident Response Life Cycle
Preparation, Detection and Analysis, Containment, Eradication and Recovery, and Post-Incident Activity.
By providing a repeatable, structured approach to addressing and learning from security incidents.
Roles include IT staff, legal advisors, incident managers, and PR representatives.
Plans should be reviewed at least annually or after major incidents to incorporate lessons learned.
It focuses on root-cause analysis and continuous improvement to strengthen future responses.