The NIST Incident Response Plan, is an essential framework for managing cybersecurity incidents effectively. As part of the NIST Cybersecurity Framework (CSF), it guides organizations in detecting, responding to, and recovering from threats like data breaches, ransomware, and malware attacks.
Businesses, Managed Service Providers (MSPs), Managed Security Service Providers (MSSPs), and government agencies rely on this framework to minimize the impact of incidents, ensure business continuity, and maintain regulatory compliance. By implementing a NIST-aligned incident response plan, organizations can strengthen their cybersecurity defenses while building trust with stakeholders.
What Is a NIST Incident Response Plan?
A NIST Incident Response Plan is a structured process that enables organizations to handle cybersecurity incidents with speed and efficiency. Established by NIST SP 800-61, this plan provides guidelines for identifying, mitigating, and recovering from cyber threats while minimizing their impact on business operations.
The primary purpose of this plan is to enhance an organization’s ability to respond proactively to incidents, ensuring critical systems and data remain secure. It is highly recommended for businesses, MSPs, and government agencies that manage sensitive data or critical infrastructure, as it helps mitigate risks, maintain compliance, and support operational resilience.
Why Is a NIST Incident Response Plan Essential?
The NIST Incident Response Plan is critical for organizations aiming to maintain strong cybersecurity practices. By following this framework, organizations can effectively prepare for and manage cybersecurity incidents, ensuring minimal disruption to their operations.
Key reasons why this plan is essential include:
- Minimizes Downtime: Quickly isolates and mitigates threats to maintain business continuity.
- Reduces Data Breach Impact: Limits the spread of malware and the loss of sensitive data.
- Supports Compliance: Aligns with regulations like CMMC, HIPAA, and PCI-DSS to ensure compliance during audits.
- Strengthens Cybersecurity Posture: Encourages proactive threat detection and response, reducing vulnerabilities.
- Improves Client Trust: Demonstrates a commitment to protecting sensitive information, fostering customer confidence.
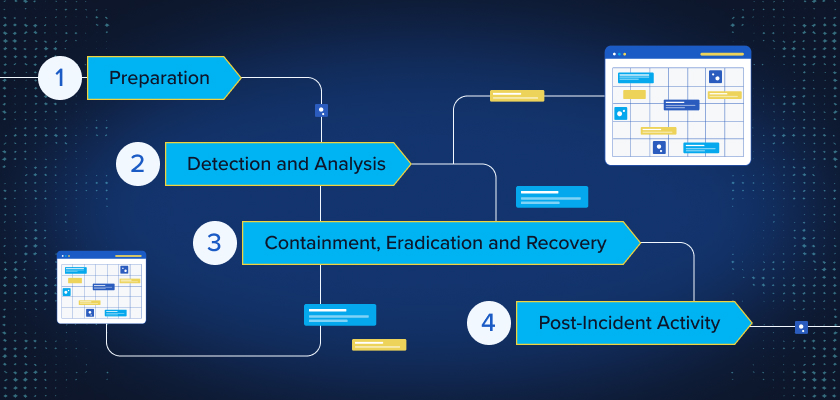
The NIST Incident Response Process: Four Key Phases

The NIST Incident Response Plan consists of four critical phases, ensuring a comprehensive and structured approach to managing cybersecurity incidents:
| Phase | Objective | Key Actions |
| Preparation | Establish an incident response capability before incidents occur. | Develop an incident response policy, assign team roles, and conduct regular employee training. |
| Detection and Analysis | Identify, report, and analyze potential incidents. | Monitor system logs, use detection tools, and evaluate incident severity based on predefined criteria. |
| Containment, Eradication, and Recovery | Limit the spread of an incident, eliminate the threat, and restore systems. | Isolate affected systems, remove malware, recover from backups, and validate system functionality. |
| Post-Incident Activity | Learn from incidents to prevent future attacks. | Conduct root-cause analysis, update security policies, and share findings with stakeholders. |
How the NIST Incident Response Plan Aligns with NIST CSF
The NIST Incident Response Plan aligns closely with the core functions of the NIST Cybersecurity Framework, offering a seamless integration for managing cybersecurity risks.
- Core Function: Respond (RS): The “Respond” function in NIST CSF is directly supported by the incident response process, ensuring quick and effective action during incidents.
- Core Function: Detect (DE): Detection tools and monitoring systems, emphasized in CSF, aid in identifying incidents during the detection and analysis phase.
- Core Function: Recover (RC): Post-incident recovery aligns with CSF’s “Recover” function, ensuring continuity and resilience after incidents.
- Continuous Improvement: Both frameworks emphasize learning from incidents to enhance future cybersecurity policies.
Best Practices for Managing Incident Response
Effective incident response management requires a proactive approach supported by the right tools and strategies.
- Automate Incident Detection: Use advanced tools for real-time threat monitoring, logging, and alerting.
- Create a Communication Plan: Develop internal and external communication strategies for incident notifications.
- Use Data Backups and Disaster Recovery Plans: Ensure frequent backups of critical data, test recovery plans, and encrypt stored backups.
- Review and Update Regularly: Continuously update incident response policies based on emerging threats and lessons learned.
- Engage Third-Party Experts: Partner with managed security services or consultants for expertise in handling complex incidents.
Stay Resilient with a NIST Incident Response Plan
Adopting a NIST-aligned Incident Response Plan is essential for organizations to prepare for, respond to, and recover from cybersecurity incidents. By following the structured approach defined in NIST SP 800-61, and using our NIST Incident Response Plan Template, businesses can reduce the impact of incidents, maintain compliance with regulations, and build a more resilient cybersecurity posture.
Investing in these best practices not only minimizes risks but also demonstrates a commitment to protecting sensitive information and maintaining client trust. Cynomi’s AI-powered platform further simplifies the process by automating key elements of incident response planning, helping businesses identify gaps, generate policies, and ensure readiness through continuous monitoring and compliance tracking. With Cynomi, organizations can streamline their IR plan development and improve their ability to detect, contain, and recover from security incidents efficiently.
Step-by-Step Guide to NIST Compliance for Service Providers
Simplify NIST compliance with a step-by-step roadmap, actionable best practices, and tools to help your MSP or MSSP scale services efficiently and securely.
Frequently Asked Questions About NIST Incident Response Plans
A structured process for managing and responding to cybersecurity incidents as defined by NIST SP 800-61.
It minimizes incident impact by ensuring quick detection, response, and recovery.
Preparation, Detection and Analysis, Containment, Eradication and Recovery, and Post-Incident Activity.
Roles typically include IT specialists, legal counsel, public relations, and senior leadership.
The “Respond” and “Recover” functions in the CSF align with the incident response process.