If you already provide strategic security advisory services, you know the potential they hold: deeper client relationships, recurring revenue, strategic positioning, and, most importantly, delivering stronger and more resilient security that helps your clients protect what matters most.
Still, many providers face challenges in scaling these services effectively. Manual, time-consuming processes limit efficiency, upsell opportunities are often missed, new client acquisition can be inconsistent, and service packaging isn’t always optimized for repeatability and profitability.
This blog explores why many providers struggle to scale their ongoing advisory services effectively and outlines steps that can be taken to overcome these challenges.
The Pain Points Holding Many Service Providers Back
Even the most experienced providers can encounter roadblocks when trying to expand their strategic security services. These challenges are common realities in a fast-evolving market. Recognizing and addressing them can open the door to greater scale, profitability, and client impact.
Upsell Opportunities Are Missed
Your current clients are often the most accessible and valuable source of growth. Yet even providers with a strong advisory practice often overlook opportunities sitting within their current book of business. One-off project clients, such as those who engaged you for a HIPAA assessment, may benefit from additional offerings, like ongoing compliance support, executive reporting, or roadmap development.
Tapping into this opportunity begins by identifying where clients can benefit from expanded support and introducing structured, value-driven services that help them meet their broader security and business goals.
Services Aren’t Structured to Scale
Custom engagements can deliver value, but they also demand significant resources. Without a defined structure, such as service tiers or standardized deliverables, it becomes difficult to maintain consistency across clients or clearly communicate the full value of your offerings. Well-defined packages help clients see how your services align with their needs today and how those services can evolve with them.
New Client Acquisition Feels Limited
Even for experienced providers, gaining new clients can be one of the most persistent challenges. Many rely on referrals or long-standing networks, which may not deliver the consistent growth needed to scale. At the same time, selling strategic services requires a different approach than selling tactical fixes. Prospective clients may not understand what an advisory engagement entails or why it’s necessary. Without clear positioning, messaging, and sales enablement tools, even strong offerings can be overlooked.
Manual Processes Are Slowing You Down
Many providers still rely on tools like Word documents, spreadsheets, and ad hoc workflows to deliver and manage their security services. While these methods can work at a small scale, they quickly become a bottleneck as demand grows. Manual processes slow down delivery and make it harder to serve more clients without increasing overhead or burning out your team.
The Solution: 4 Ways to Start Scaling
1. Prioritize Upsells
Your current clients are the most accessible and efficient starting point for expanding your advisory services. These organizations already know your work and trust your expertise, which reduces the friction often associated with introducing additional offerings. By focusing on the relationships you’ve already built, you can uncover unmet needs and identify opportunities for strategic upselling that align with each client’s goals.
The key to doing this effectively is segmentation. Begin by grouping clients by industry, size, and security maturity. This provides a clearer picture of their challenges and priorities, enabling you to tailor your advisory services accordingly. Industry segmentation reveals compliance drivers and sector-specific pain points, such as HIPAA for healthcare or CMMC for government defense contractors.
Company size can help determine the level of support needed. Smaller clients may need foundational support, while mid-sized organizations might benefit from strategic planning and executive reporting. Larger clients, even those with internal security teams, may still need fractional or deputy CISO leadership to align their programs with business objectives.
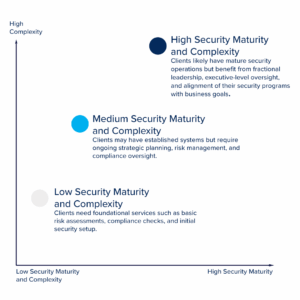
A matrix can help segment client needs:
Once segmented, prioritize clients who are most likely to benefit from expanding into advisory services. For example, if you notice a concentration in medium maturity, medium complexity, you should prioritize developing specific advisory packages that address the unique needs of each segment, ensuring they align with client expectations and challenges. This approach allows you to grow revenue and deepen relationships by maximizing the potential within your current client base before turning attention to new acquisitions.
2. Standardize and Package Your Offerings by Tier
Once you’ve assessed your client base using the security maturity matrix, the next step is to identify where to expand advisory services and how to deliver them consistently and at scale. Standardizing both the structure and delivery of your offerings ensures that, regardless of the client’s maturity level, you have a clear, repeatable path to deepen the relationship and grow your impact.
Look at your clients through the lens of their current maturity and align your upsell approach accordingly:
- Low-maturity clients may have engaged you for tactical needs, but they’re often in urgent need of foundational advisory services. Offer structured, ongoing programs that build their security maturity over time, guiding them through risk assessments, compliance planning, and policy development.
- Medium-maturity clients likely have some processes in place and are ready to benefit from a more strategic advisory relationship. This is where services like recurring risk reviews, compliance oversight, and long-term planning can be introduced. Standardized formats for roadmaps and executive reporting help demonstrate clear, ongoing value.
- High-maturity clients often have internal teams but still require executive-level leadership support. The opportunity here is to position yourself as a fractional or deputy CISO, providing executive guidance, program alignment, and board-level communication. Deliverables should follow defined engagement plans and reporting structures to ensure consistency and scale.
It’s not only about standardizing the packaging of your services but also the services themselves. Defining how key elements, such as risk assessments, remediation planning, compliance tracking, and executive reporting, are conducted ensures consistent quality and enables scaling delivery across more clients without reinventing the process each time. Standardization brings efficiency, clarity, and repeatability to every engagement, enabling sustainable growth and development.
Burwood Group, for example, implemented a standardized risk assessment process and now sees over 50 percent of those assessments convert into ongoing vCISO engagements. By formalizing their approach, they created a scalable model that opens the door to long-term, high-value client relationships.
3. Build a System for Client Acquisition
Scaling your advisory services requires a consistent, intentional approach to attracting new clients. Start by tapping into your existing network, where trust is already established. Reconnect with past clients, current contacts, and industry peers who may know organizations in need of more strategic security guidance. This approach was key for Donna Gallaher, founder of New Oceans Enterprises, who built her initial client base by leveraging her professional network and relationships developed over a long career in enterprise IT and security. Many of her early clients were smaller companies launching new products or larger organizations seeking specialized expertise.
From there, expand your reach through targeted thought leadership. Donna later scaled her visibility through LinkedIn articles, referrals, and public speaking, methods that helped position her as a governance-first advisor and grow her vCISO practice. Educational content, such as blog posts, webinars, executive workshops, and industry briefings, helps providers communicate their expertise and demonstrate how cybersecurity and compliance directly support business goals. Focus your messaging on the outcomes that matter most to your ideal clients, such as reduced risk exposure, increased compliance, and stronger alignment with business strategy.
Cynomi provides powerful support to help service providers drive client acquisition and scale faster through a comprehensive suite of tools, visibility programs, and strategic resources. Providers can boost visibility and establish thought leadership by being featured in the vCISO Directory and collaborating with Cynomi on educational and promotional initiatives, including social media campaigns, partner webinars, email outreach, and participation in Cynomi’s vCISO Academy. Together, these programs create a comprehensive system that empowers providers to grow efficiently and win more business.
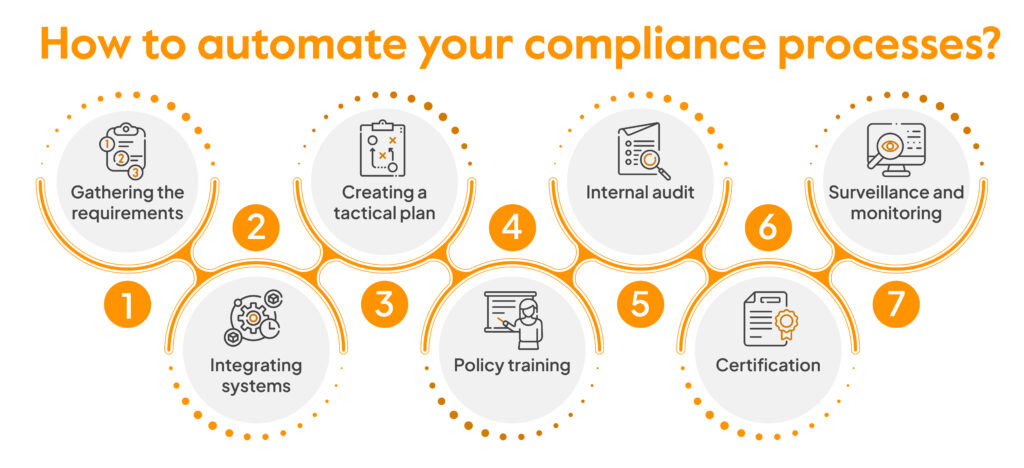
4. Leverage Automation to Multiply Impact
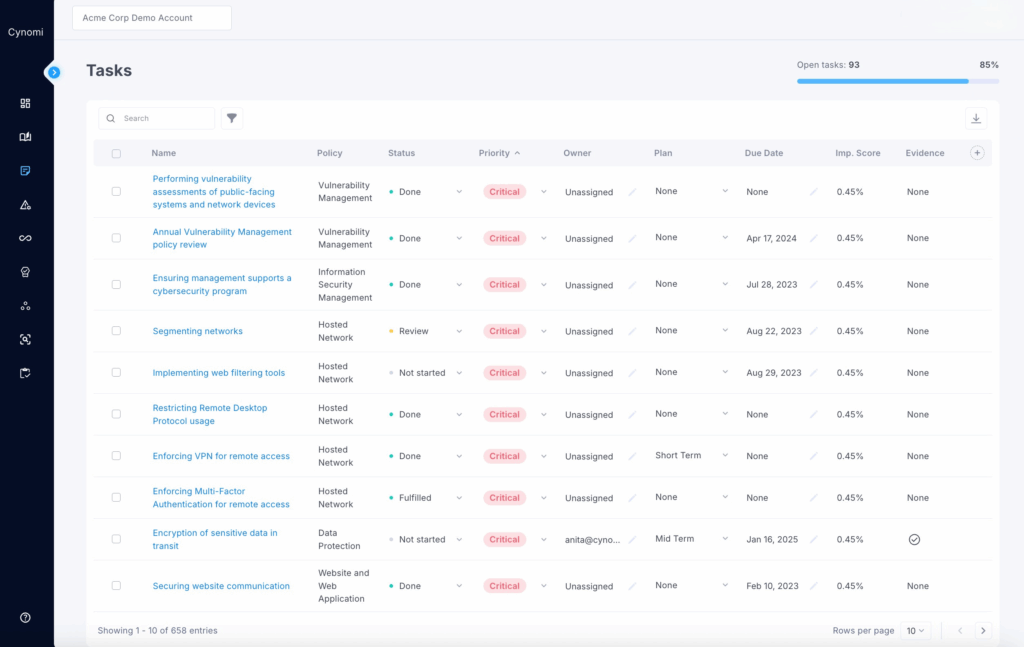
Manual processes remain one of the biggest bottlenecks to growth for service providers. From assessments and remediation planning to policy creation and reporting, providers often spend hours on repeatable tasks that consume valuable resources and limit capacity. This not only slows delivery but also makes it harder to maintain consistency across clients or scale services efficiently.
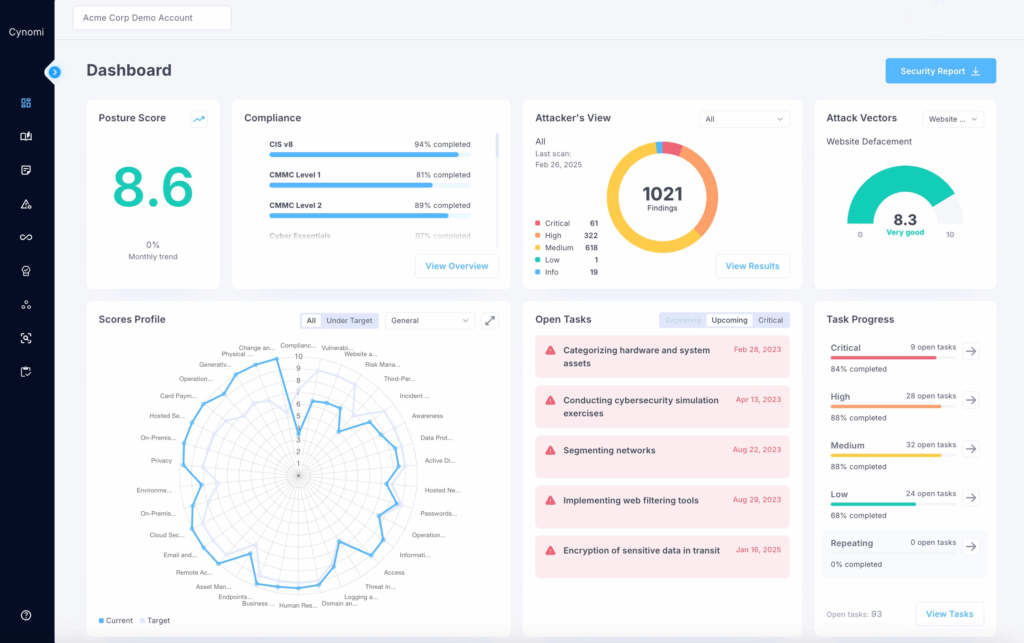
Cybersecurity and compliance management platforms, like Cynomi, leverage automation to bring structure, speed, and consistency to service delivery. Automated workflows streamline the entire process, from onboarding and assessments to remediation planning, compliance tracking, and reporting, ensuring nothing falls through the cracks. Risk assessments are guided and comprehensive, policies are auto-generated and tailored to each client’s needs, and remediation plans are built from prioritized insights. Executive-ready reports are created in seconds, replacing hours of manual work.
The time savings add up quickly. For example, automation can save nearly 10 hours on risk assessments, up to 11 hours on policy creation, and as much as 13 hours on progress reporting per client. Multiply that across dozens of clients, and the impact on capacity, margins, and client satisfaction is substantial. This end-to-end automation enhances efficiency and accuracy, allowing teams to operate with greater capacity as trusted, strategic partners. In today’s competitive landscape, automation is not just a productivity tool; it’s a strategic advantage for growing and sustaining a high-impact advisory practice.
Real-world results: Cynomi clients, such as Secure Cyber Defense, have unlocked significant operational efficiency gains through automation, such as cutting client discovery time by 90% and accelerating deal closures by threefold. Read the full case study here.
Scaling Doesn’t Require Reinvention, Just the Right Strategy
Expanding your advisory services doesn’t mean taking on more work or overhauling everything you’ve built. It means identifying what already works and applying the right structure, standardization, and tools to do it more efficiently, and at scale.
The key is to prioritize upsell opportunities within your existing client base, where trust and familiarity already exist. Package your services into clear, maturity-aligned tiers that are easy to sell and deliver. Create a repeatable system for attracting new clients through thought leadership and targeted outreach. Most critically, embrace automation to streamline delivery, free up resources, and maintain consistency as your business grows.
The path to scale is achievable. With a focus on client value, smart operational choices, and support from cybersecurity and compliance management platforms like Cynomi, you can scale your existing advisory services while continuing to deliver the strategic impact your clients rely on.
Ready to accelerate your cybersecurity and compliance services?
The Cynomi cybersecurity and compliance management hub enables service providers to develop new services and scale existing ones through streamlined service delivery, guided processes, and efficient workflows.
As a result of enhanced efficiency and additional service offerings, providers can enter and succeed in competitive markets, driving fresh revenue streams and new client acquisition. For service providers struggling to scale, Cynomi brings structure and automation to service delivery by embedding policies and frameworks while simplifying key processes such as risk assessments, compliance readiness, remediation planning, task management, and reporting. Cynomi is made for the service provider and includes features such as the Solution Showcase, which maps service offerings to the specific needs uncovered in client cybersecurity assessments, transforming routine assessments into powerful upsell opportunities.
Discover how Cynomi enables service providers to scale their operations, achieve faster, measurable outcomes, and focus on strategic growth at cynomi.com.