
How automation streamlines assessments and onboarding and can help service providers accelerate client discovery by 90%
Client onboarding is the first step of any service provider engagement, forming the foundation for effective service delivery and lasting partnerships. Yet the process is often slow and resource-intensive, requiring significant input from clients. In many cases, assessments can take weeks or even months, with key business context scattered across emails, documents, and spreadsheets.
The result? A slower start to value delivery, resource bottlenecks, and a rocky start to what should be a long-term, high-impact relationship.
These may seem like minor inefficiencies, but they potentially impact the overall effectiveness and scalability of a provider’s service delivery over time. In this blog, we’ll explore why traditional cybersecurity onboarding and assessments are so often a source of friction, the hidden costs that come with manual, fragmented processes, and how providers can use automation and standardization to dramatically improve speed, consistency, and client experience.
The Root of the Problem: Manual and Unstructured Processes
Each new cybersecurity engagement typically starts from scratch, with teams tasked with understanding business and their needs, evaluating the client’s security posture and identifying compliance requirements. Providers frequently rely on Word documents, spreadsheets, and lengthy interviews to gather information, using generic questionnaires that can overwhelm clients with irrelevant questions.
This reliance on disconnected tools leads to fragmented processes. Teams chase down emails, spreadsheets, and scattered documentation, resulting in workflows that are difficult to manage, prone to delays, and nearly impossible to replicate consistently across clients.
Without a clear, standardized structure, every assessment can feel like an isolated, one-off project that requires rebuilding the process each time. This can lead to inconsistent quality, slower delivery, and a disjointed client experience, even when engagements are handled by the same team. Moreover, it can take weeks to get to results, and those findings are often difficult to deliver in a clear, visual format that effectively communicates value to business leaders.
Common challenges include:
- Lack of standardized assessment templates – Teams reinvent the wheel with each engagement, resulting in inconsistent outputs.
- Delays in gathering key inputs – Business context, asset inventories, and compliance needs are often incomplete or delayed because the information is spread across multiple stakeholders, not easily accessible, or requires coordination between departments.”
- Overreliance on disconnected tools – Emails, spreadsheets, and shared drives hinder collaboration and scale.
- Inconsistent delivery across team members – Without a repeatable process, outcomes vary based on who’s managing the engagement.
- Limited reporting and communication – Results are often delayed and may be presented in formats that are not accessible or actionable for non-technical stakeholders. This can reduce client clarity, engagement, and confidence.
These inefficiencies delay time-to-value, reduce client satisfaction, and ultimately impact trust, retention, and revenue growth.
The Result: Stalled Business Growth for Service Providers and a Lengthy, High-Friction Experience for Clients
Inefficient onboarding doesn’t just slow things down, it can hinder a provider’s ability to grow. When service delivery is inconsistent and resource-intensive, scaling becomes a significant challenge.
For newly signed clients, this can mean delayed outcomes and reduced momentum, which may erode trust and diminish overall satisfaction. Clients may feel stuck in administrative limbo, eager to see real progress but instead encountering repeated information requests.
At the same time, experienced team members often find themselves handling repetitive administrative tasks, while new hires face a steep learning curve due to unstructured, ad hoc workflows. This imbalance can stretch resources thin and reduce overall efficiency.
When structure is lacking, it becomes harder to deliver services at scale. Even providers experiencing high demand may struggle to onboard clients efficiently, ultimately missing chances to deepen relationships or expand service offerings.
Automation: The Key to Faster, Smarter, and More Scalable Onboarding and Assessments
Automation can fundamentally reshape one of the most time-consuming phases of client engagement: onboarding and risk assessments. Instead of relying on emails, Word docs, and spreadsheets, automation introduces structure and intelligence into the process, transforming disorganized workflows into streamlined, strategic operations.
One of the most powerful benefits of automation is standardization. Interactive questionnaires, built-in system scans, and centralized data capture allow providers to apply the same high-quality methodology across every engagement, regardless of who is leading it. This ensures assessments are both consistent and tailored to the client’s unique context, including business priorities, regulatory requirements, and technical environments.
With everything captured in a single, unified platform, teams no longer need to chase down documents or repeat the same interviews. Instead, automated tools guide the process from start to finish – collecting the right data, surfacing the most critical insights, and building a clear, prioritized remediation plan. This saves time, reduces human error, and makes onboarding not only faster, but also more valuable to the client.
Here’s an example of how automation can streamline assessment and onboarding:
| Type of process | Manual processes | Automation |
| Data collection | Manually collected via interviews, emails, forms, and spreadsheets. | Collected through interactive, guided questionnaires and technical scans. |
| Evaluating client business | Done through lengthy interviews and manual documentation. | Client business is evaluated often with elements of artificial intelligence using insights on business context, technical environment, industry and business priorities in comparison to industry standards. |
| Evaluating cybersecurity environment | Done by reviewing policies, conducting interviews, and analyzing system configurations across fragmented tools and documentation. | Business context, industry, and technical environment are analyzed using smart questionnaires and technical scans. |
| Uncovering vulnerabilities and gaps | Typically done manually through spreadsheets, interviews, and siloed tools, requiring extensive coordination across teams and environments. | Guided assessments and integrated security scans are often used to instantly identify vulnerabilities and gaps across the organization’s environment. |
| Presenting results | Word/PDF reports manually created and inconsistent. | Often with automated dashboards and easy to generate reports. |
By shifting assessments from a manual, one-off effort to an automated, repeatable process, providers can:
- Accelerate onboarding timelines
- Increase assessment accuracy
- Free up senior staff for strategic work
- Empower junior team members
- Deliver more professional, consistent client experiences
In short, automation turns a previously tedious task into a high-value service, unlocking new revenue streams, improving margins, and enabling long-term, scalable growth.
A more structured and insightful assessment experience also creates natural entry points for upselling additional services. When clients clearly understand their risks and gaps through well-delivered assessments, they are more likely to invest in follow-up services, projects, and long-term strategic guidance.
Background
Secure Cyber Defense, a growing cybersecurity service provider, faced a familiar challenge: onboarding and assessments were slow, manual, and resource-heavy. Their team relied on Word documents, spreadsheets, and lengthy interviews to gather information – a process that varied from one client to the next and took weeks to complete. As a result, service delivery was delayed, consistency suffered, and scaling operations became increasingly difficult.
The Automation Difference
To address these inefficiencies, Secure Cyber Defense adopted Cynomi, the leading cybersecurity and compliance management platform to streamline their onboarding and assessment workflows. The platform enabled them to standardize how client information was gathered, risk was assessed, and remediation plans were developed. Interactive questionnaires and automated scans replaced manual data collection, ensuring more accurate inputs and eliminating repetitive tasks. This not only accelerated their process but also made it more repeatable across clients.
“Before Cynomi, assessments were largely manual, using Word documents and spreadsheets. Now, we’ve automated much of the process, which not only saves time but ensures consistency across every engagement.”
– Shawn Waldman, CEO of Secure Cyber Defense
The Impact
- Client discovery time dropped by 90%
- Sales cycles were reduced from 3 months to just 3 weeks
- Junior staff were able to deliver senior-level assessments
With automation in place, Secure Cyber Defense improved operational efficiency, enhanced client experience, and unlocked a more scalable, high-margin service model. To learn more about how Secure Cyber Defense streamlined assessments, read the full case study here
Conclusion: It’s Time to Rethink Onboarding
Manual onboarding and assessment processes may feel manageable in the early stages, but they often become limiting over time. These approaches can slow value delivery, consume valuable team resources, and result in varied client experiences.
By standardizing and automating these essential early steps, providers can enhance consistency, elevate service quality, and accelerate delivery. This also allows teams to shift their focus to strategic guidance, enabling scalable growth and stronger client relationships.
With the right tools, cybersecurity providers can reduce manual friction, streamline onboarding, and begin delivering value sooner in the client journey.
How Cynomi Partners Elevate Client Onboarding
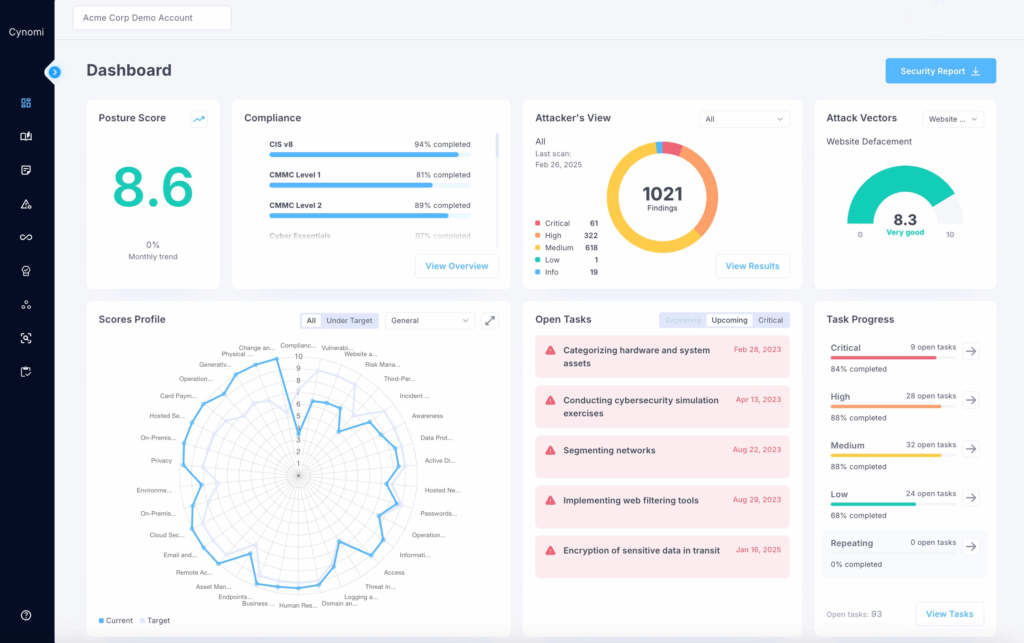
Cynomi helps service providers streamline and elevate client onboarding. Interactive, guided questionnaires and built-in technical scans speed up data collection and make the process more intuitive and enjoyable for clients. Once assessments are completed, the findings are displayed instantly in clear visual formats, showing open gaps, vulnerabilities, and compliance status. These insights are immediately translated into a structured security and compliance roadmap, complete with prioritized remediation steps and associated policies.
Here’s a quick look at Cynomi’s onboarding and assessment process:
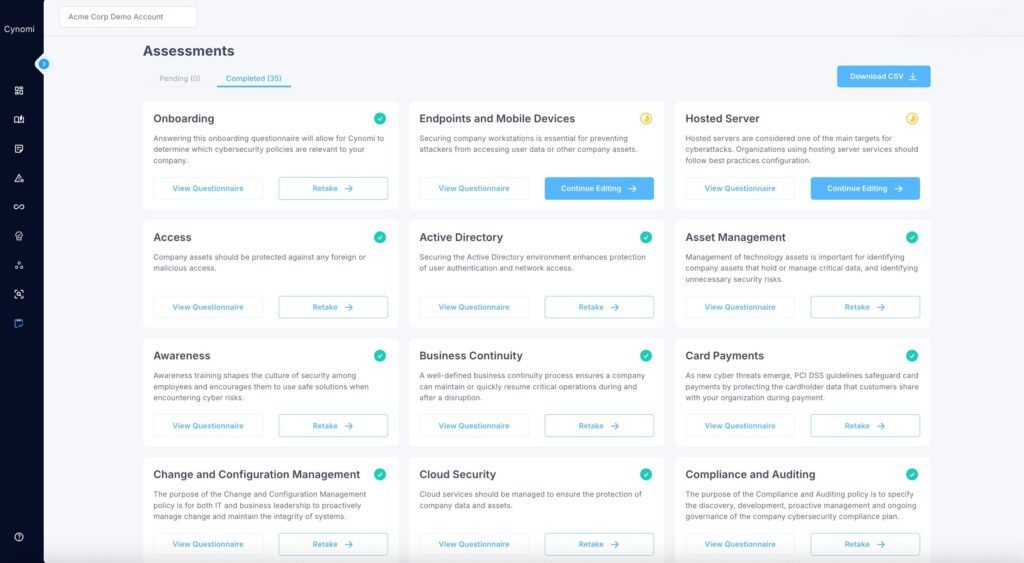
Step 1: Begin the onboarding and assessments process
Screen: Assessments dashboard
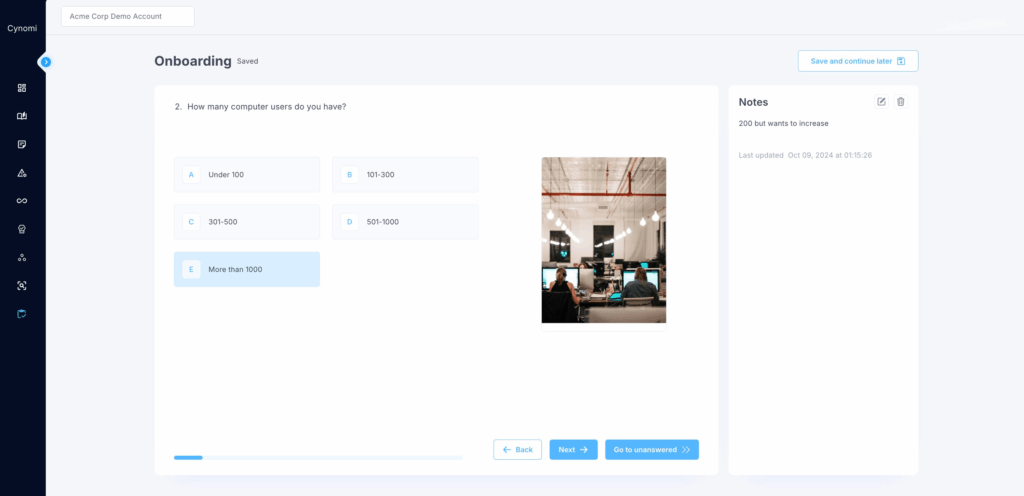
Step 2: Answer various questions, including:
Screen: Onboarding Assessment: Industry

Screen: Onboarding Assessment: Company size
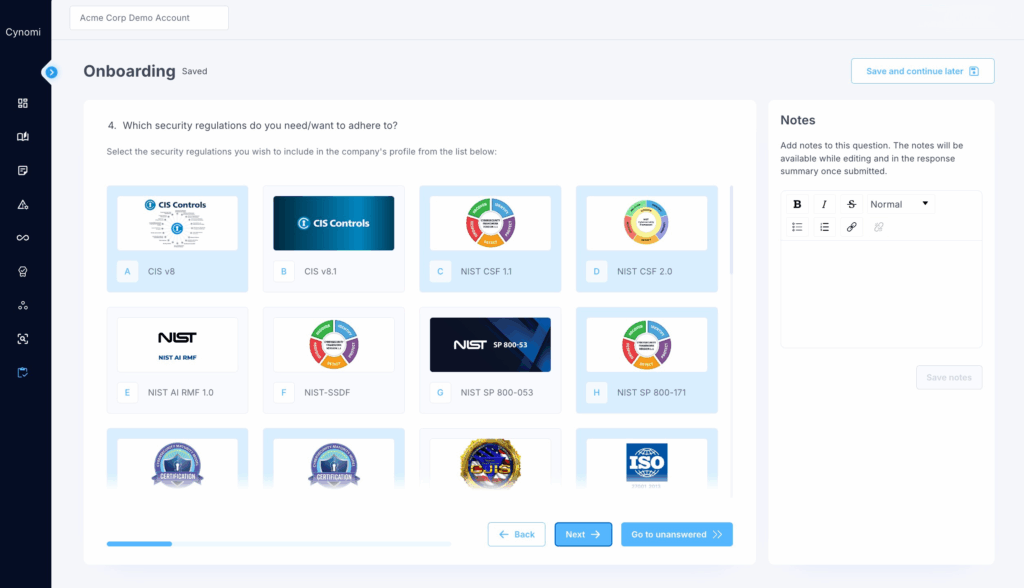
Screen: Onboarding Assessment: Security Regulations
Step 3: Instantly see gaps, vulnerabilities and compliance status
Screen: Main Dashboard
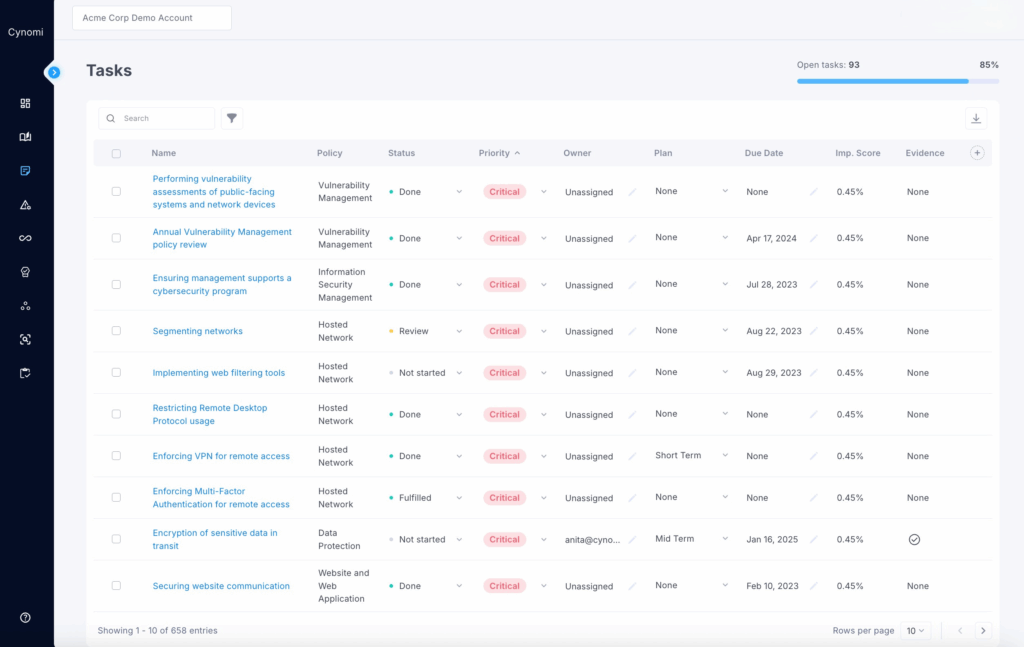
Step 4: Tasks are automatically generated to create a prioritized security and compliance workflow roadmap with associated policies
Screen: Tasks
By standardizing workflows and automating time-consuming tasks, Cynomi enables service providers to efficiently scale operations, expand client bases, and deliver high-impact cybersecurity services. To learn how Cynomi can help you streamline your onboarding and assessment processes, visit cynomi.com.