The rollout of Cybersecurity Maturity Model Certification (CMMC) 2.0 represents a watershed moment for service providers. On one hand, it offers a massive revenue opportunity. Thousands of defense contractors in the Defense Industrial Base (DIB) are scrambling to meet strict cybersecurity requirements to retain their contracts. On the other hand, it presents significant liability and operational challenges for the service providers supporting them.
Navigating this landscape requires a fundamental shift in how providers approach scope, documentation, and shared responsibility. To help you cut through the noise, we recently hosted a webinar featuring three industry experts: Wil Burchett, Lead CMMC Certified Assessor (LCCA) at Logos Systems, Michael Cardenas, CTO & Founder at MC3 Technologies, and Patrick Costello, Partner Account Manager at Cynomi.
Together, they broke down exactly what CMMC 2.0 entails, where service providers often stumble, and how to build a scalable, defensible compliance program. If you missed the live session, here are the critical takeaways your team needs to know now. Watch the full replay here.
The Shift from Self-Attestation to Accountability
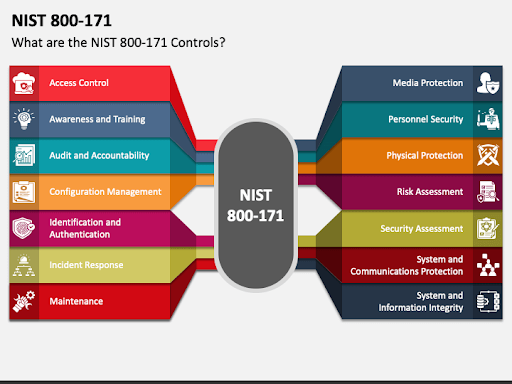
The history of defense compliance is a story of escalating enforcement. Since 2017, defense contractors have been required under DFARS 7012 to implement NIST SP 800-171 controls and self-attest to their compliance. However, the Department of Defense (DoD) eventually realized that self-attestation wasn’t working. Most companies simply weren’t meeting the requirements they claimed to be.
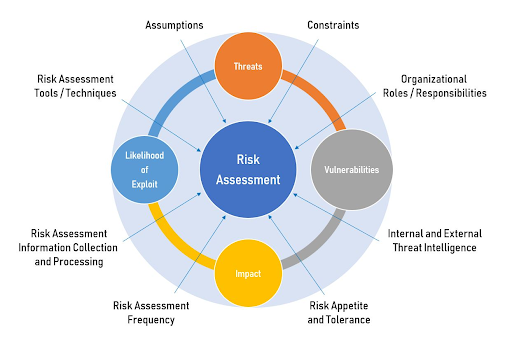
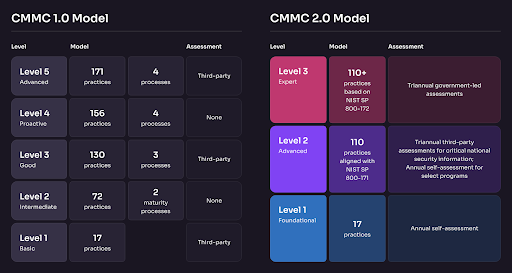
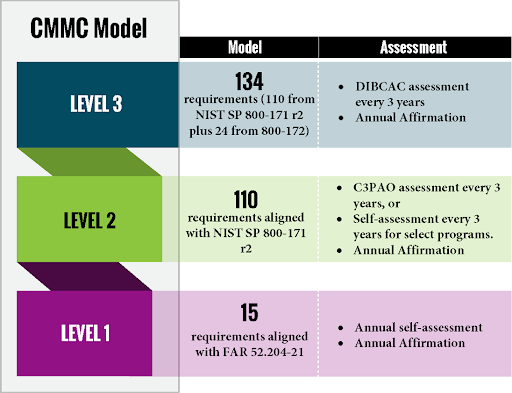
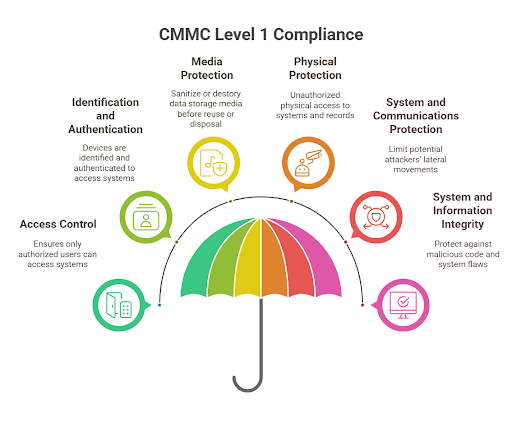
This realization gave rise to CMMC, which moves the industry toward verified compliance. While Level 1 (focusing on Federal Contract Information, or FCI) still allows for self-assessment, CMMC Level 2 (focusing on Controlled Unclassified Information, or CUI) raises the stakes significantly. For contractors handling critical data, compliance is no longer an honor system; it now requires a formal assessment by a Certified Third-Party Assessor Organization (C3PAO).
For MSPs, this means the “set it and forget it” approach to security is obsolete. You aren’t just securing a network–you are preparing a client for a high-stakes audit that determines whether they stay in business.
The “In-Scope” Wake-Up Call for MSPs
One of the most sobering insights from the webinar is that many MSPs do not realize they are part of the assessment scope until it is too late.
If you are an MSP managing IT for a defense contractor, you are considered an External Service Provider (ESP). If your tools (RMM, backup solutions, ticketing systems) or your staff touch the client’s CUI (or even the security protection assets protecting that CUI), you are in scope.
As Michael Cardenas noted, “If your employees are remoting into client machines and seeing documents on the screen that are FCI or CUI, you inherit those controls.” This means your MSP’s own internal security posture effectively becomes part of your client’s audit. If your house isn’t in order, your client cannot pass their assessment.
Defining Shared Responsibility
To manage this liability, MSPs must be explicitly clear about who owns what. This is where a detailed Shared Responsibility Matrix (SRM) becomes your most valuable asset.
An assessor will look at the System Security Plan (SSP) and identify which controls the client claims the MSP handles. They will then ask to see the contract and the SRM to verify that obligation. Finally, they will turn to you, the MSP, and ask you to prove it.
“Am I defining all the services and tools that I use? Am I defining what controls from CMMC that aligns with?” asked Cardenas. If you cannot answer those questions defensibly in writing, you are exposing both your firm and your client to failure.
Inside the Mind of an Assessor: What to Expect
Wil Burchett provided a rare look behind the curtain at what assessors actually want. A common misconception is that buying the right software tool solves compliance. Burchett clarified that while tools help track progress, they do not satisfy an assessor. Assessors don’t log into your GRC tool to poke around. They evaluate evidence based on the narrative in your SSP.
Evidence Over Screenshots
Assessors are required to validate controls using two of three methods:
- Examine: Reviewing documentation or artifacts.
- Interview: Talking to the staff responsible for the control.
- Test: Watching a live demonstration of the control in action.
“We don’t assess screenshots,” Burchett warned. Screenshots are static and easily forged. Instead, assessors want to see live interactions. For example, if you claim unauthorized users are blocked, an assessor will ask you to try logging in with a disabled account and watch it fail in real-time.
The “Paper” Trap
Scoping is the most critical phase of preparation, and it is where many organizations fail. A common strategy is to create a secure “digital enclave” for CUI to keep the rest of the network out of scope. However, physical workflows often break this containment.
If a client downloads a sensitive file from a secure cloud enclave and prints it, the resulting physical paper brings their physical premises, and potentially the local network used to print it, back into scope. Burchett highlighted that a Data Flow Diagram is essential here. You must track exactly how data moves, including through physical mediums like paper or USB drives, to ensure your scoping boundaries hold up under scrutiny.
Navigating Cloud and FedRAMP Requirements
For MSPs leveraging cloud services to store or process CUI, the requirements are strict. Any cloud offering involved must meet FedRAMP Moderate equivalency. This creates complexity when selecting vendors, particularly for productivity suites like Microsoft 365.
During the webinar, the panel discussed the nuances of Microsoft Commercial versus Government (GCC High) tenants. Burchett pointed out that Microsoft’s FedRAMP package specifically notes that inheriting controls often requires being on a government SKU. While commercial tenants may meet certain security standards, they may not support the inheritance of controls required for a CMMC assessment in the same way a GCC High environment does.
This is a technical but vital distinction. Recommending the wrong license could force a client to undergo a costly migration right before their assessment.
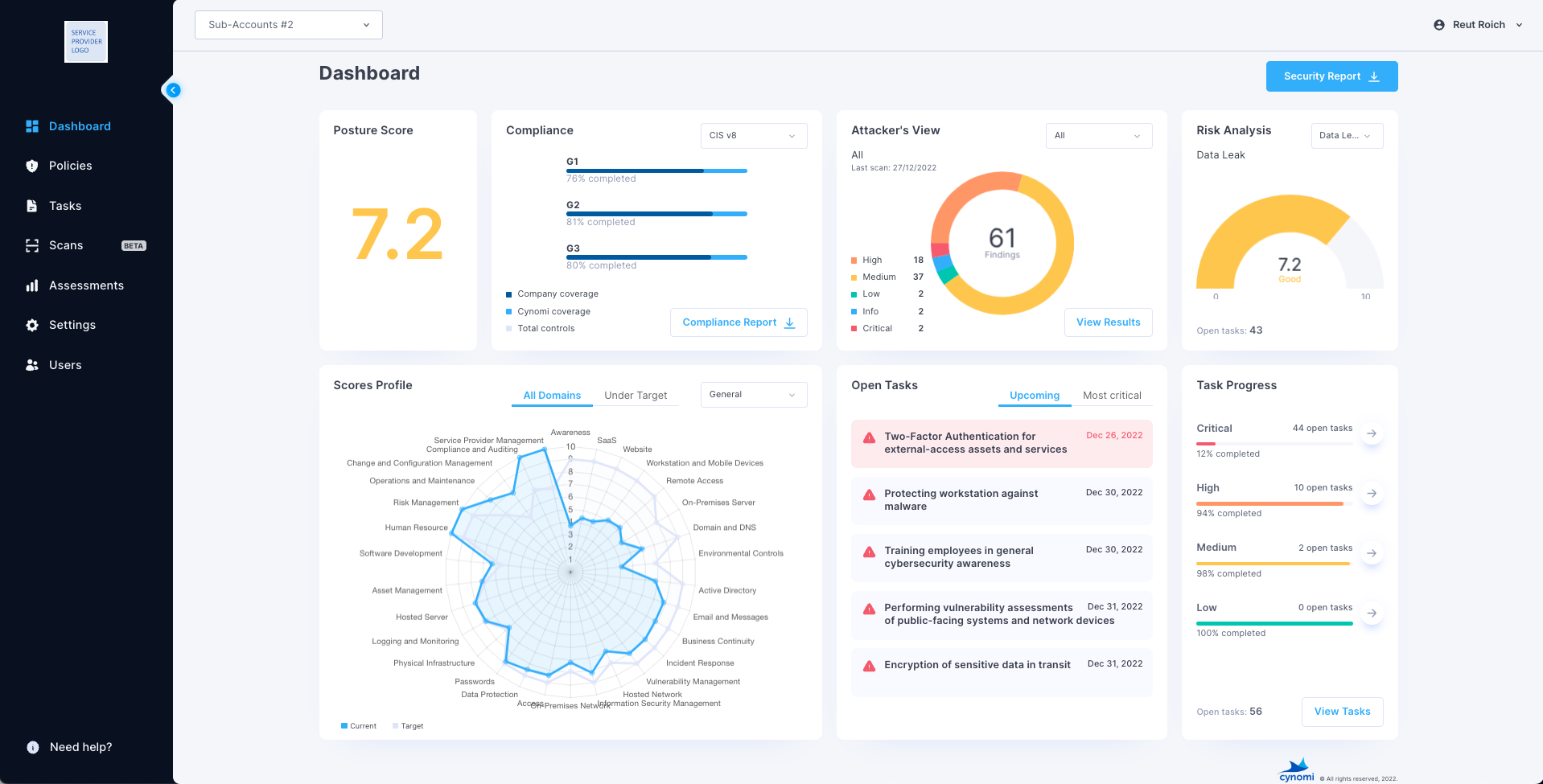
Streamlining Compliance with Cynomi
Managing these complex requirements manually is nearly impossible at scale. This is where Cynomi’s Security Growth Platform steps in to support service providers. The platform has introduced specific features to help MSPs manage CMMC 2.0 readiness effectively:
- SPRS widget: A live, dynamic look at a client’s Supplier Performance Risk System (SPRS) score, allowing you to track progress toward the target score required for assessment.
- POA&M reports: One-click generation of the Plan of Action & Milestones (POA&M), which serves as a project management tool to track and close gaps before the audit.
- SSP Control Implementation Report: An exportable report that provides the narrative detail assessors need, mapping controls to specific tasks and owners.
While no tool can completely automate a System Security Plan since it requires a unique narrative about the client’s specific environment, Cynomi standardizes the data collection and evidence tracking, getting you 80% of the way there. This allows your team to focus on the high-value advisory work rather than administrative drudgery.
Turn Compliance into a Strategic Advantage
CMMC 2.0 is not going away. In fact, experts predict the framework will likely influence other federal compliance standards in the future, meaning this ecosystem will only grow.
For MSPs, the choice is clear: treat this as a burden, or embrace it as a strategic opportunity. By mastering scoping, clarifying shared responsibilities, and leveraging platforms like Cynomi to standardize your delivery, you can position your firm as an indispensable partner to the Defense Industrial Base.
Ready to dive deeper into the details?
Watch the full webinar replay here to get all the insights from our expert panel.










![The Essential cyber insurance risk assessment [XLS Download]](https://cynomi.com/wp-content/uploads/2025/02/The-Essential-cyber-insurance-risk-assessment-XLS-Download-1-1-768x366.png)






![The Definitive Cyber Security Policy Template [XLS Download]](https://cynomi.com/wp-content/uploads/2024/12/The-Definitive-Cyber-Security-Policy-Template-XLS-Download-1-768x366.png)